
In this IT age, networking is the key to most business operations. Every access to any system in a network domain is thus entrusted through user accounts and upon correct user password approval. Since, critical business data and transactions are shared on the network, illicit attempts for account access is an alluring prospect for trespassers who try to supersede in their own felonious intentions. Thus, account lockout and password usage helps to combat such malpractices.
Microsoft recommends using the account lockout feature as per your organization’s security requirements to help deter malicious users and automated attacks from discovering user passwords. This is because most attacks today are automatic and software generated; having lenient Active Directory account lockout policies leave scope for serious threats.
Setting the basics right
Malicious users will try to guess a numerous passwords during a password-based attack. Therefore, the first and foremost thing would be to enforce complex password settings to discourage successful attack opportunities.
For example, if you enforce password complexity with a password length of 6 characters and set password expiry to 60 days, a user can choose from a permutation of 26 lowercase characters, 26 uppercase characters, 32 special characters and 10 numbers.
This means that:
- 26 + 26 + 32 + 10 = 94 possible characters in a password
- Password length policy = 6
- 946 = 689,869,781,056 unique password permutations
Within the defined 60 days password expiration interval, the malicious user would have to make 133,076 password attempts every second to try all of the possible passwords during that password’s limited lifetime.
To even decrease the chances of accidental password discovery, you can choose a character length of 7. Under the same settings with password length to 7, the possible password permutations exceed 64 trillion (947 = 64,847,759,419,264). Thus, stringent password policies can play a significant role in defeating malicious attacks.
Recommended Password Policy Settings
(Source: http://technet.microsoft.com)
Check the table to see recommended password policy settings for various security configurations:
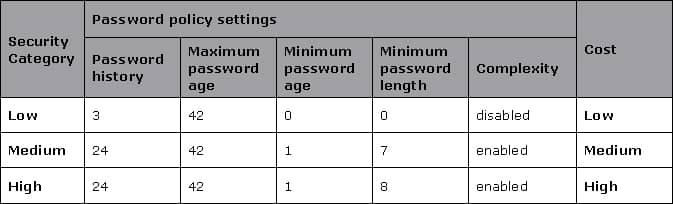
Figure: ‘Cost’ here refers to the downtime (productivity loss) cost for the user whose account gets locked out, as well as the support cost for servicing the locked out account.
Keep track on updates
Also, you must take notice to apply the latest service packs and hotfixes to all of the domain controllers, servers, and clients to confirm that the expected account security settings are applied and to ensure that the domain controllers and operating systems are in updated state.
Ensure auditing is “ON”
While logging in, there are two primary authentication protocols used by Windows: NTLM and Kerberos. Therefore to find out whether account lockouts were real threats or just lockouts within designated users, you must enable these settings beforehand:
- Enable auditing at the domain level
- Enable Netlogon logging
- Enable Kerberos logging
Microsoft recommends that you frequently review the Security event logs of all computers to be are aware of any lockout patterns that might indicate an attack or user error. The values that are necessary to identify specific malicious users and targets can be obtained only after you implement auditing in advance.
Thus, these settings can help to prevent a brute force attack on user passwords.
A deterring factor to consider
In an environment where you set such stringent password policies and account lockout settings, it’s very likely that many actual users may forget their complex passwords or multiple incorrect password attempts lead to a large number of lockouts. This may be another discerning factor as it involves a lot of cost and raises burden for the help-desk team.
It is quite obvious that, the stronger the security that is implemented, higher will be the cost associated with maintaining that security. ‘Cost’ accounts for both the productivity loss of the user and the support cost for servicing the locked out account.
To maintain balance between optimum security demands and costs involved, self-service password reset solutions can play a vital role as end users can directly mitigate such issues. Lepide Active Directory Self Service (LADSS) allows users to reset their password/unlock account directly from their login (ALT+ CTRL + DEL) screen and nullify downtime and IT help desk costs.
To know more about LADSS and see how it can effectively bring down costs, visit https://www.lepide.com/active-directory-self-service/
 Important Group Policy Settings & Best Practices to Prevent Security Breaches
Important Group Policy Settings & Best Practices to Prevent Security Breaches 15 Most Common Cyber Attack Types and How to Prevent Them
15 Most Common Cyber Attack Types and How to Prevent Them Why Active Directory Account Getting Locked Out Frequently – Causes
Why Active Directory Account Getting Locked Out Frequently – Causes
