There are many reasons why you may want to track file and folder activities on Windows File Servers; including data security and compliance. Knowing when users are accessing, reading, creating, modifying or deleting your files and folders is of paramount importance when it comes to ensuring the security and integrity of your File Servers. In this article, we will show you how to keep track of what’s happening to your files and folders using native processes, and also how using Lepide File Server Auditor can help to simplify the entire process. The following are the steps:
Step 1: Configure the “Audit Object Access” audit policy
Perform the following steps to set up this audit policy:
- On the primary domain controller, or on a workstation where “Administration Tools” are installed, open “Run” dialog box, type “gpmc.msc”, and click “OK” to open the “Group Policy Management” console.
- In the “Group Policy Management” window, right-click on the default or a customized domain policy, and select “Edit” from the context menu to open the Group Policy Management Editor window.
Note: It is recommended to create a new GPO, link it to the domain and edit it.
- In “Group Policy Management Editor” window, navigate to “Computer Configuration” ➔ “Windows Settings” ➔ “Security Settings” ➔ “Local Policies” ➔ “Audit Policy”.
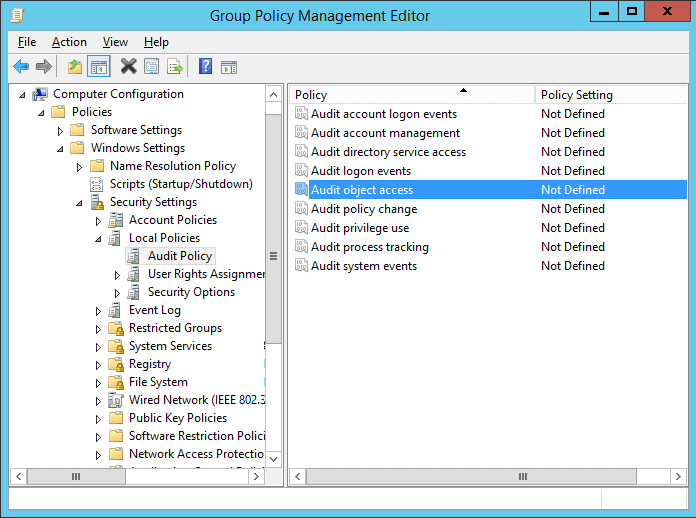
Figure 1: Properties of “Audit Object Access” policy - Double-click “Audit Object Access” to view its properties.
- Click “Define these policy settings” checkbox. Click “Success” and “Failure” check boxes.
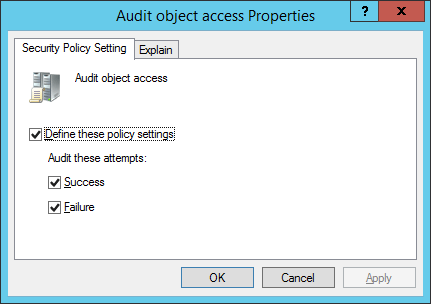
Figure 2: “Audit object access” policy
Step 2: Configure auditing on files and folders
Follow the below steps to enable auditing for the files and folders you want to audit on your Windows File Server.
- Open “Windows Explorer”, and navigate to the folder that you want to track.
- Right-click the folder and select “Properties” from the context menu. The folder’s properties window appears on the screen.
Note: If you want to track multiple folders, you will have to configure audit for every folder individually.
- Navigate to “Security” tab.
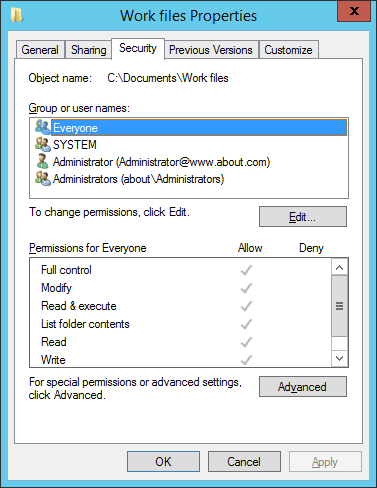
Figure 3: Security tab of “Work files” folder’s properties - Click “Advanced” to access “Advanced Security Settings”. In “Advanced Security Settings” window, navigate to “Auditing” tab.
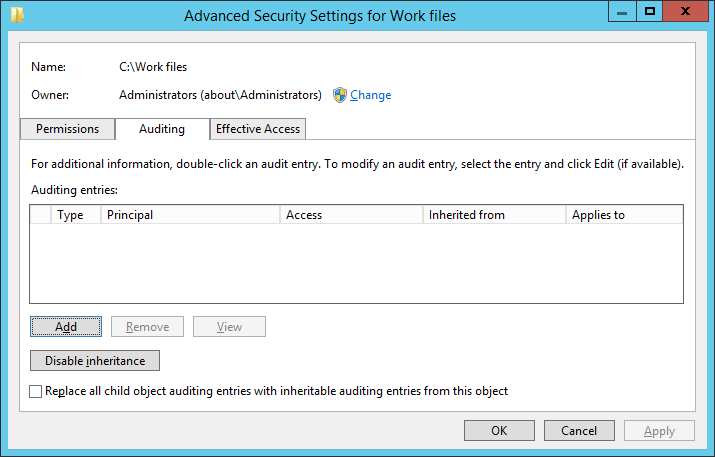
Figure 4: Auditing tab of “Advanced security settings” window - To create a new auditing entry, click “Add”. “Auditing Entry” window appears on the screen.
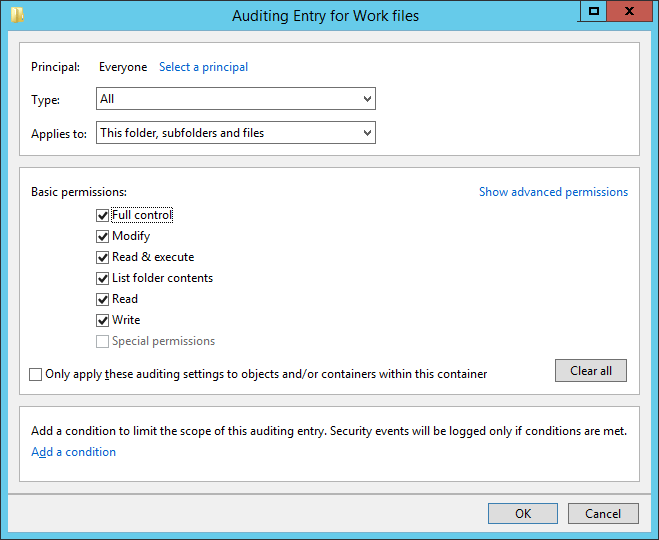
Figure 5: “Auditing entry” window of the folder - Click “Select a Principal” to choose users whose activities you want to track.
- “Select User, Computer, Service Account, or Group” dialog box appears on the screen. If you want to audit all users’ activities, enter “Everyone” in the “Enter the object name to select” dialog box, and click “Checknames”. In our case, we enter “Everyone”.
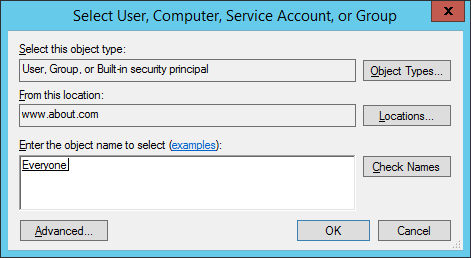
Figure 6: “Select users…” dialog box - Click “OK” to finalize your selection. It takes you back to “Auditing Entry” window.
- Select “All” in “Type” drop-down menu to monitor both successful and failure events. You can select “Success” to monitor only successful events or you can select “Failure” to monitor only failure events.
- In “Applies to” drop-down menu, select “This folder, subfolder, and files” option, if you want to audit all the subfolders and the files within this folder.
- Click “Show advanced permission” option in the permissions section to view all the permissions. Select all the actions that you want to audit. If you want to audit all the actions, click “Full Control” checkbox. Here, we have selected “Full Control” checkbox.
- Click “OK” to apply the auditing settings. It closes “Auditing Entry” window.
- Now on “Auditing” tab of “Advanced security settings” window, you can see the newly added audit entry.
- Click “Apply” and “OK” in the “Advanced Security Setting” window to close it.
- Click “Apply” and “OK” to close the folder properties window.
Step 3: View Events in Windows Event Viewer
After you have configured the above audit settings, you can track any change made to folders, subfolders, and files. For that, open “Windows Event Viewer” and go to “Windows Logs” ➔ “Security”. In the right pane, use the “Filter Current Log” option to find the relevant events.
For example, if anyone creates a new file, event ID 4656 and Event ID 4663 will both be logged. To illustrate this, in our case, a file has been created in the “Work files” folder. In the following image, you can see the details of the event ID 4656:
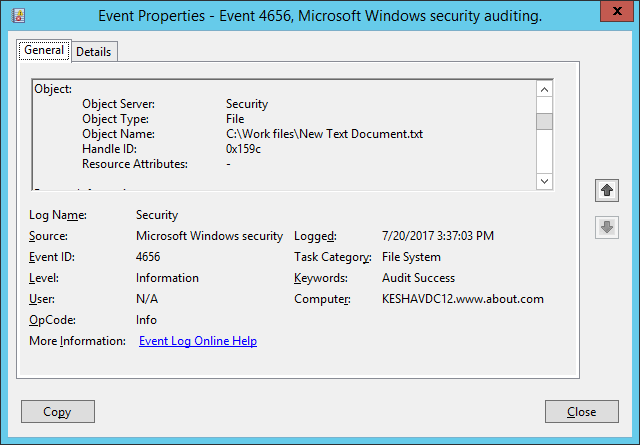
You can see the new file’s name (C:\Work files\New Text Document) which is visible after you scroll down the side bar.
The same event ID 4656 shows all accesses made to the objects, such as files and folders.
Track File and Folder Activities Easily with Lepide File Server Auditor
Lepide File Server Auditor can be used to track all file and the folder activities of users. Unlike Native Auditing, you do not have to manually enable the auditing for different files and folders. You just have to install the solution and configure the audit settings once and you are good to go.
The following image shows the files and folder creation report. You can filter the records by any column; including file name, creation time, user name, and any other available column. All the necessary information related to the create event is shown in a single line record.
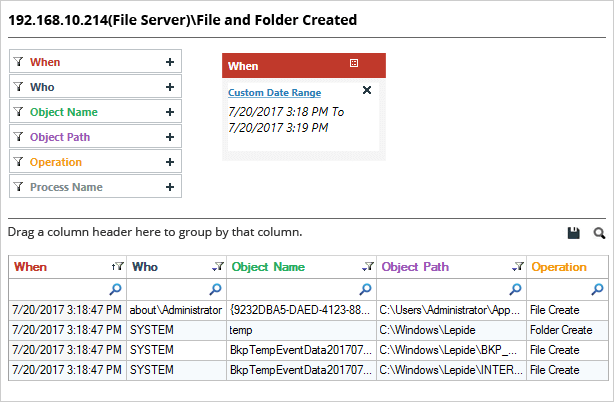
In the above image, we have highlighted the record which contains the information about where a file was created. Answers to all relevant audit questions, such as “who, what, when, and where” are available in a single line record.
Conclusion
In this article, you have seen how to keep track of all files and folder activities on your Windows File Server using both native methods and Lepide File Server Auditor. Clearly the easier option, Lepide’s File Server auditing software can help you keep track of all the files and folders on your Windows File Servers.
