Tracking file and folder modifications in Windows file servers holds significant importance due to several reasons. Firstly, it aids in identifying unauthorized access or alterations made to sensitive data. Secondly, it assists in troubleshooting issues related to file access and permissions. Lastly, it serves as evidence in the occurrence of a security incident.
There are various approaches to audit changes to files and folders in Windows file servers. One commonly used method involves utilizing the built-in auditing features. To implement this, it is necessary to enable auditing for the desired files and folders. Once auditing is enabled, Windows will document all access and modification events in the security event log.
Alternatively, one can opt for a third-party file auditing tool to monitor file and folder changes. These tools offer more detailed auditing information than the built-in features and enable monitoring of file access across multiple servers.
Irrespective of the chosen method, tracking file and folder modifications is vital for safeguarding data and systems. By effectively monitoring such changes, unauthorized access or alterations can be swiftly identified and addressed, problems related to file access or permissions can be troubleshooted, and evidence can be provided in the case of a security incident.
In this article we will explore both the native method for tracking modifications/changes to files and folders on File Server, and how Lepide Auditor for File Server can make the process simpler.
How to Track File and Folder Changes using Event Logs
Below is a detailed description of the procedure for tracking activities on files and folders:
- Open the ‘Run’ window, type ‘gpmc.msc’, and click OK
Run ‘gpmc.msc’ on DC or workstation where Administration Tools pack installed.
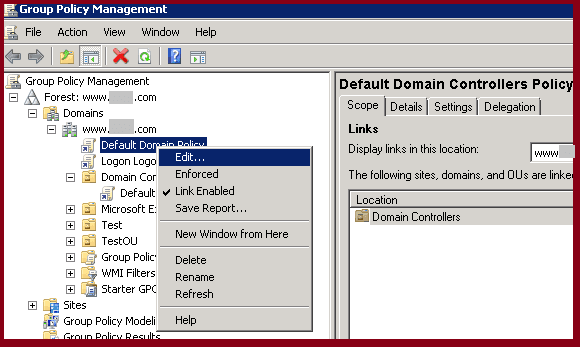
- Right-click on a domain policy and select Edit
- Double-click on ‘Audit object access’
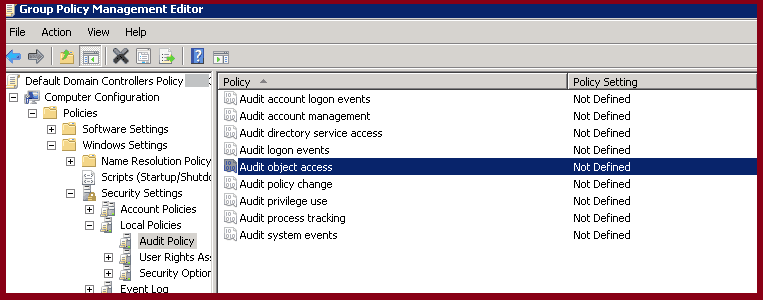
Now expand as Computer Configuration → Windows Settings → Security Settings → Local Policies → Audit Policy and double-click ‘Audit object access’.
- Select the check-boxes Success, Failure or both (as per your auditing needs)
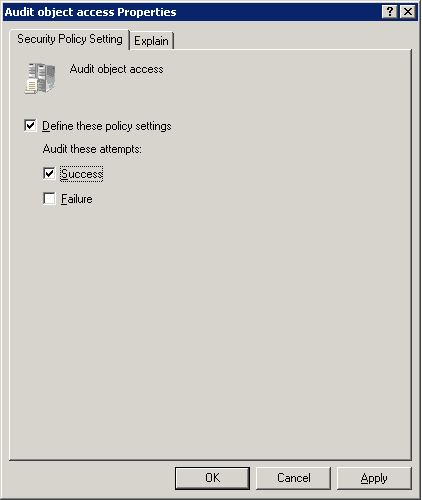
- Audit only successful attempts – Select ‘Success’ check box
- Audit only failed attempts – Select ‘Failure’ check box
- To audit both success and failed attempts – Select both check boxes
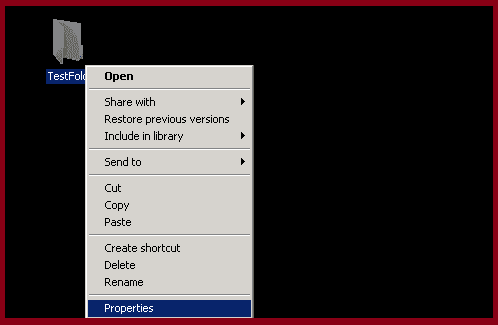
- Right-click the folder and select Properties
Now in Windows Explorer:
- Select the folder on which you want to track/audit activities
- Right click on the folder
- Click on properties
- In the Properties windows click the Security tab, and then click Advanced
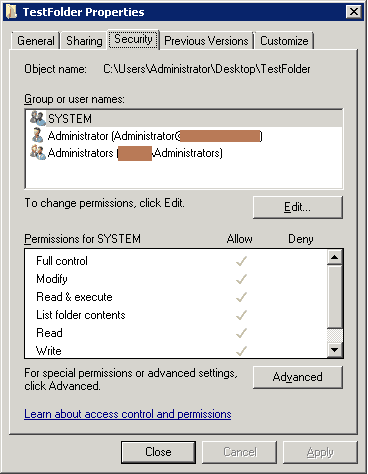
- Click the Auditing tab, and click Edit
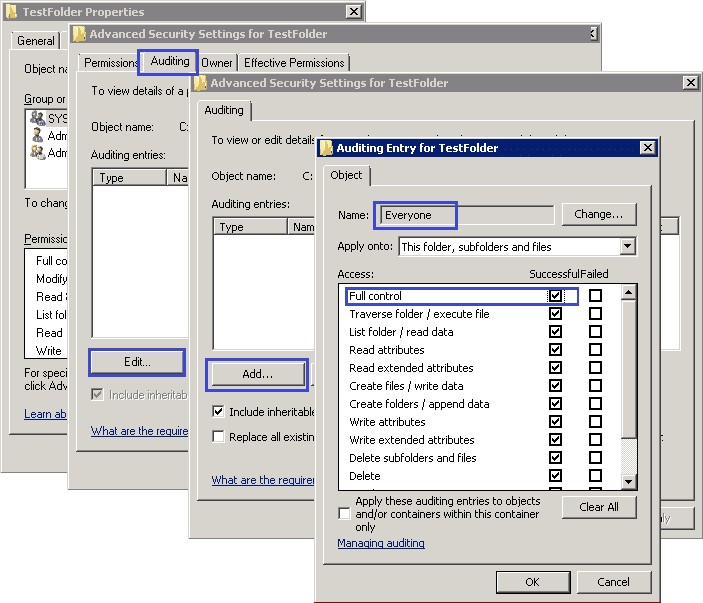
In the Advanced Security Settings for dialog box, click the Auditing tab, and click Edit.
In the new dialogue box, click Add and add Everyone to the list.
Now, in the Auditing entry for window, select Full control and click OK. Finally, close all open windows by clicking OK buttons
- Open ‘Event Viewer’
Go to start menu to open ‘Event Viewer’. Once ‘Event Viewer’ opens:
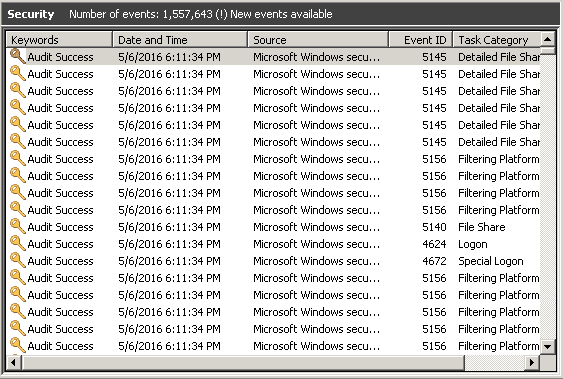
Expand ‘Windows Logs’ → Select ‘Security’ → Click on ‘Filter Current Log..’
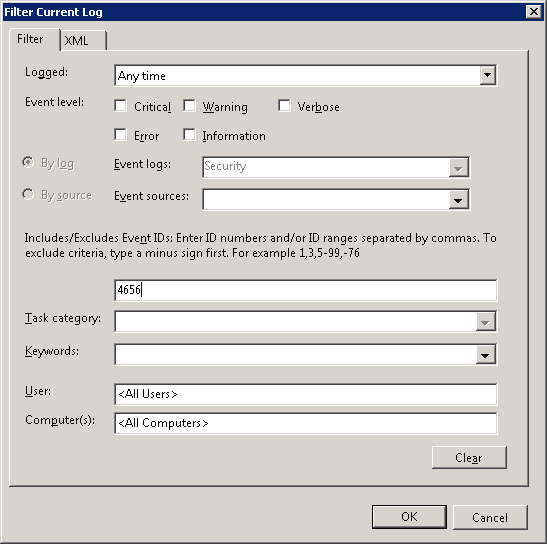
- Enter the event ID you want to search. Here, we are entering Event ID 4656 (the event that is generated when ‘a handle to an object was requested’).
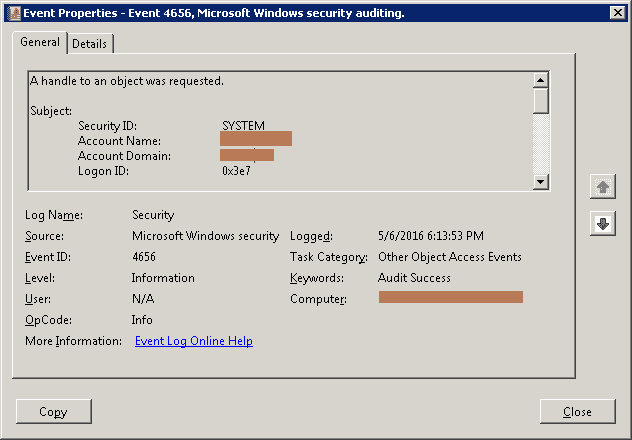
- When all the events having ID are listed, double-click on any event to see its details.
Search for other relevant event IDs given below.
Limitations of Native Auditing
However, most of the time, native file server auditing just doesn’t give enough level of detail. This is because it is an entirely reactive process. For more effective file server auditing, it is important to be constantly keeping an eye on changes. This is simply not possible with native methods. Fortunately, third-party auditing solutions, like Lepide File Server Auditor, can simplify this process using intuitive UIs and user-friendly features to automate what would otherwise be very time consuming tasks.
How Lepide File Server Auditor can help you better track file and folder changes
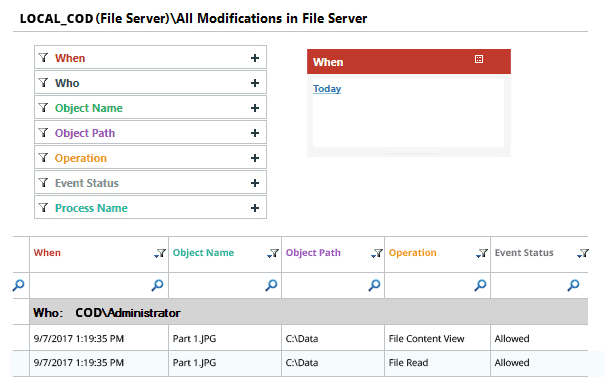
Lepide File Server Auditor captures file/folder events in order to monitor each and every activity of users in both Windows File Servers and NetApp filers. The solution generates an “All Modifications Report” in the “Audit Reports” tab that displays detailed information about all changes (in both Grid view and Graph View) that have been made by users in file systems. Below is a screenshot with an example of the “All Modifications Report”.