
Active Directory (AD) is pretty much the go-to domain authentication services for enterprises all over the world and has been since its inception in Windows Server 2000.
Back then, AD was pretty unsecured and had some flaws that made it particularly difficult to use. For example, if you had multiple domain controllers (DCs), they would compete over permissions to make changes. This meant that you could be making changes and sometimes they simply wouldn’t go through.
What are FSMO roles in Active Directory
Over the last few decades, Microsoft has introduced numerous enhancements, patches, and updates that have drastically improved AD functionality, reliability, and security. One such change was to head towards a “single Master Model” for AD where one DC could make changes to the domain. The other DCs fulfilled automation requests.
However, people quickly realized that if the master DC goes down, no changes could be made at all until it was back up again. So, Microsoft had to rethink.
The solution they came up with was to separate the responsibilities of the DC into numerous roles. That way, if one of the DCs goes down, another can take over the missing role. This is known as Flexible Single Master Operation (also known as FSMO or FSMO Roles).
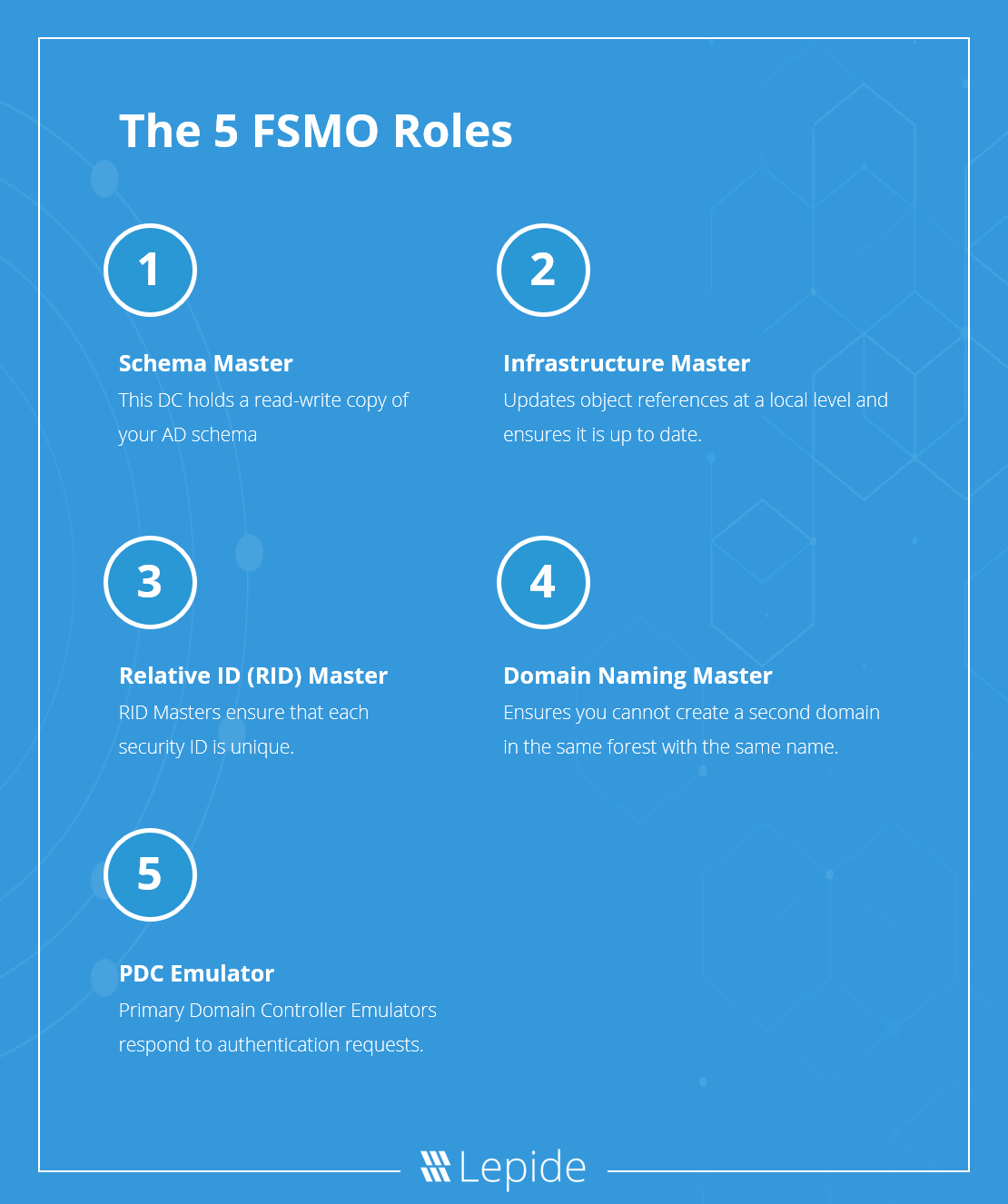
The 5 FSMO Roles in Active Directory
A full Active Directory system is split into five separate FSMO roles. Those 5 FSMO roles are as follows:
- Relative ID (RID) Master
- Primary Domain Controller (PDC) Emulator
- Infrastructure Master
- Domain Naming Master
- Schema Master
Schema Masters and Domain Naming Masters are limited to one per forest, whereas the rest are limited to one per domain.
 The 5 FSMO Roles in Active Directory[/caption]
The 5 FSMO Roles in Active Directory[/caption]
1. Relative ID (RID) Master
If you want to create a security principle you are probably going to want to add access permissions to it. You can’t grant these permissions based on the name of a user or group because that can change. Instead, you associate them with a unique security ID (SID). Part of that unique identifier is known as the relative ID (RID). To prevent two objects having the same SID, a RID Master processes RID pool requests from DCs within a single domain and ensures that each SID is unique.
2. Primary Domain Controller (PDC) Emulator
This is the most authoritative DC in the domain. The role of this DC is to respond to authentication requests, managed password changes and manages Group Policy Objects (GPO). Users cannot even change their passwords without the approval of the PDC Emulator. It’s a powerful position!
3. Infrastructure Master
This controller understands the overall IT infrastructure in the organization, including what objects are present. The infrastructure master updates object references at a local level and also makes sure that it is up to date in the copies of other domains. It does this through unique identifiers, such as SIDs.
4. Domain Naming Master
This DC simply ensures that you are not able to create a second domain in the same forest with the same name.
5. Schema Master
This DC holds a read-write copy of your AD schema. Schema is essentially all the attributes associated with an object (passwords, roles, designations, etc.). So, if you need to change a role on a user object, you’ll have to do it through the Schema Master.
How to Check FSMO Roles
To check FSMO roles, you can use various methods depending on the Windows Server version and your preference:
Method 1: Using PowerShell
Open PowerShell as an administrator and run the following command:
Get-ADForest | Select-Object DomainNamingMaster, SchemaMaster Get-ADDomain | Select-Object InfrastructureMaster, RIDMaster, PDCEmulator
This PowerShell command will display the current FSMO role holders for the forest and domain.
Method 2: Using Command Prompt
Open Command Prompt as an administrator and run the following commands:
netdom query fsmo
This command provides a list of the servers holding the FSMO roles for the domain.
Method 3: Using Active Directory Users and Computers (ADUC)
- Open Active Directory Users and Computers on a computer with the Active Directory tools installed.
- Right-click on the root of the console (usually “Active Directory Users and Computers” at the top).
- Select Operations Masters…
This will open a dialog box showing the three FSMO roles for the domain. You can switch between tabs to view forest-level FSMO roles as well.
Method 4: Using Active Directory Administrative Center (ADAC)
- Open Active Directory Administrative Center on a computer with the Active Directory tools installed.
- In the left pane, select the root of the console.
- In the middle pane, select the Domain/Forest and navigate to the Operations Masters tab.
This will show you the current holders of the FSMO roles.
Additional Notes:
- If you have multiple domains in your forest, you need to check the FSMO roles for each domain.
- The netdom and PowerShell commands can be run from any computer with the Active Directory PowerShell module installed, while the ADUC and ADAC methods are typically performed on a domain controller or a computer with the Active Directory tools installed.
Remember that FSMO roles are critical for the proper functioning of the Active Directory environment, so it’s essential to know their current holders and be able to transfer or seize them if necessary.
FSMO Roles: Reliability and Availability
The 5 FSMO Roles are critically important as they go hand in hand with the security of your Active Directory. The domain controllers, therefore, need to be online at the time the services are needed. Thankfully, depending on the FSMO role, this may not be all that often. For schema master, for example, the DC only needs to be online during the update. The PDC, however, will need to be online and accessible at all time. For that reason, you need to make the necessary steps to ensure that the PDC emulator does not fall over.
If you find yourself in a scenario where one of the FSMO roles is unavailable (say, for example, the PDC emulator), you need to act quickly to get all your FSMO roles back up and running again. If you know that a particular FSMO role is going to undergo scheduled maintenance, you should transfer the FSMO role to a different DC. If the worst should occur, and your FSMO role crashes, you can always seize the FSMO role to another domain controller as a last resort.
Conclusion
It’s absolutely vital that you are proactively and continuously monitoring Active Directory changes in order to prevent insider threats, privilege abuse, and brute force attacks. Unsure about how to do this? Schedule a demo with one of our engineers today and see how Lepide Active Directory Auditor helps monitor and secure AD.

 Important Group Policy Settings & Best Practices to Prevent Security Breaches
Important Group Policy Settings & Best Practices to Prevent Security Breaches 15 Most Common Cyber Attack Types and How to Prevent Them
15 Most Common Cyber Attack Types and How to Prevent Them Why Active Directory Account Getting Locked Out Frequently – Causes
Why Active Directory Account Getting Locked Out Frequently – Causes
