
- Support
- |
- sales@lepide.com
- |
- +1-800-814-0578

| Functionality | Quest | Lepide |
|---|---|---|
| Active Directory risk assessment |  |
 |
| GPO configuration and change auditing |  |
 |
| Real-time threat detection |  |
 |
| User behavior analytics |  |
 |
| Automated threat response |  |
 |
| Active Directory Change auditing |  |
 |
| Logon/logoff auditing |  |
 |
| Account Lockout Analysis |  |
 |
| Excessive permissions reporting |  |
 |
| Current permissions reporting |  |
 |
| Historic permissions analysis |  |
 |
| Permission change analysis |  |
 |
| Configuration auditing |  |
 |
| Who, what, where, and when information |  |
 |
| Before and after values |  |
 |
| Built in AD and Group Policy rollback feature |  |
 |
Audit changes and interactions on a wide variety of on-premise and cloud platforms, including Active Directory, File Server, Exchange, Microsoft 365 and more. Audit how your users are interacting with your sensitive data, including moving, copying, renaming, modifying, deleting, and more. Consolidate raw log data into actionable, easy to understand reports. Access hundreds of pre-defined audit reports or customize your own reports to get the information you need.
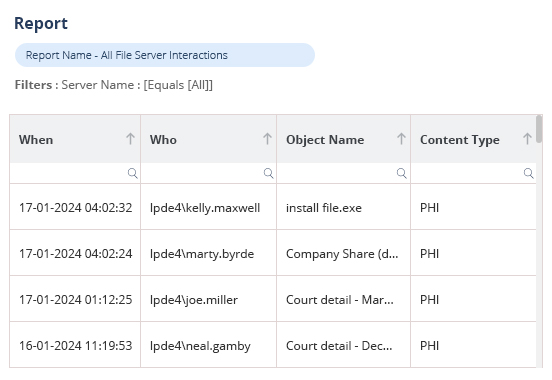
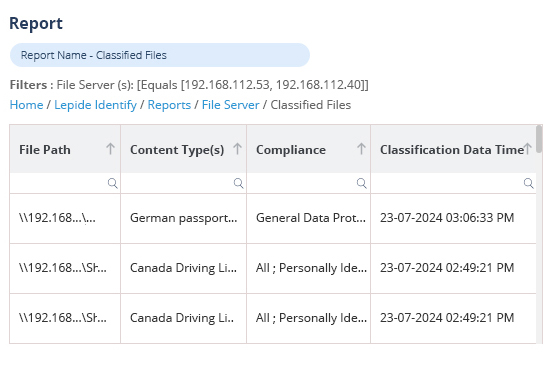
All our data classification technology has been fully developed in house and is supported by our world class internal support team. We allow you to find out where your most sensitive data is located and classify it according to sensitivity and related compliance requirements.
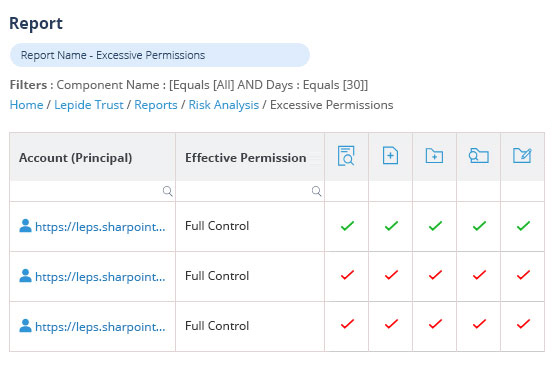
Easily determine who has access to your most sensitive data and spot excessive permissions with predefined reports. This insight will allow you to ensure that you are operating on a policy of least privilege where users only have access to the data they need to do their job – and thus reduce the risk of data breaches.
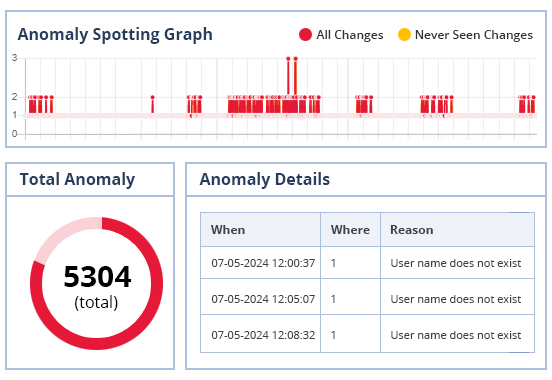
Spot anomalies in user behavior that could potentially be damaging to your data security. Our solution can also spot changes to systems and audit security states in Active Directory, File Server and others that are indicative of a potentially insecure environment.
We have a simple and reasonable approach to pricing and licensing which means you get the full value of our solution with no nasty hidden fees. Our agent or agent-less architecture and limitless integration capabilities mean that we are one of the most scalable solutions on the market today. Our award-winning support team are on hand 24x5 to help you with all manner of inquiries.

Through our universal auditing module, which enables you to connect to any platform using a restAPI or Syslog, you can get visibility over the broadest scope of platforms on the market today. No other vendor offers the range of on-premise and cloud-based platforms that Lepide can offer, including Varonis.