PowerShell has evolved into an indispensable administrative tool over the past decade, providing IT professionals with powerful command-line capabilities for managing Windows, macOS, and Linux environments. One particularly valuable application is its ability to retrieve and analyze Azure AD sign-in logs, giving administrators visibility into user authentication activities across their organization. This guide walks through the complete process of accessing, filtering, and analyzing these sign-in logs using PowerShell’s scripting capabilities.
Why is it Important to check Azure AD Sign-In Logs?
Organizations should prioritize Azure AD sign-in log monitoring for several important reasons:
- Quickly identify suspicious login attempts, potential credential theft, and unauthorized access.
- Satisfy compliance frameworks that require comprehensive access tracking and documentation.
- Quickly diagnose and fix user login issues by examining failed authentication attempts.
- Build accurate timelines during incident response by analyzing historical access patterns.
- Spot compromised accounts by identifying unusual login locations, times, or patterns.
How to use PowerShell to Find Azure AD Sign-in Logs?
Prerequisites
Before you begin, ensure you have the following:
- The AzureAD and AzureADPreview modules are installed.
- The necessary permissions to access Azure AD sign-in logs.
Step-by-Step Guide to Use PowerShell
- Install the AzureADPreview Module
- Open PowerShell as an administrator.
- Run the following command to install the AzureADPreview module:
Install-Module AzureADPreview -AllowClobber
- Connect to Azure AD
- Connect to your Azure AD tenant by running the following command:
AzureADPreview\Connect-AzureAD
- Connect to your Azure AD tenant by running the following command:
- Retrieve Sign-In Logs for the Last 45 Days
- Use the Get-AzureADAuditSignInLogs cmdlet to fetch sign-in logs for the past 45 days:
$startDate = (Get-Date).AddDays(-45).ToString("yyyy-MM-ddTHH:mm:ssZ")
Get-AzureADAuditSignInLogs -Filter "createdDateTime ge $startDate"
- Use the Get-AzureADAuditSignInLogs cmdlet to fetch sign-in logs for the past 45 days:
- Filter Sign-In Logs by User
- To filter sign-in logs by a specific user, use the userPrincipalName or userDisplayName attribute:
Get-AzureADAuditSignInLogs -Filter "userPrincipalName eq 'user@domain.com'"
- To filter sign-in logs by a specific user, use the userPrincipalName or userDisplayName attribute:
- Filter Sign-In Logs by Application
- To filter sign-in logs by a specific application, use the appDisplayName attribute:
Get-AzureADAuditSignInLogs -Filter "appDisplayName eq 'Application Name'"
- To filter sign-in logs by a specific application, use the appDisplayName attribute:
- Filter Sign-In Logs by Status Code
- To retrieve only successful sign-in logs (errorCode eq 0)
Get-AzureADAuditSignInLogs -Filter "status/errorCode eq 0" -All $true - To retrieve only failed sign-in logs (errorCode ne 0)
Get-AzureADAuditSignInLogs -Filter "status/errorCode ne 0" -All $true
- To retrieve only successful sign-in logs (errorCode eq 0)
- Export Sign-In Logs to CSV
- To export all sign-in logs to a CSV file
Get-AzureADAuditSignInLogs -All $true | Export-CSV "C:\AzureADAuditSignInLogs.csv" -NoTypeInformation -Encoding UTF8
- To export all sign-in logs to a CSV file
- Schedule the Script
- You can use Windows Task Scheduler to run your PowerShell script at a specific time of day or week. Here is an example script that gets today’s sign-in logs and exports them to a CSV file:
# Connect to Azure AD
Connect-AzureAD
# Get today's date
$today = Get-Date
# Fetch sign-in logs
$signInLogs = Get-AzureADAuditSignInLogs -Filter "createdDateTime ge $today"
# Export logs to CSV
$signInLogs | Export-Csv -Path "C:\Path\To\Export\SignInLogs.csv" -NoTypeInformation
- You can use Windows Task Scheduler to run your PowerShell script at a specific time of day or week. Here is an example script that gets today’s sign-in logs and exports them to a CSV file:
How Lepide Helps
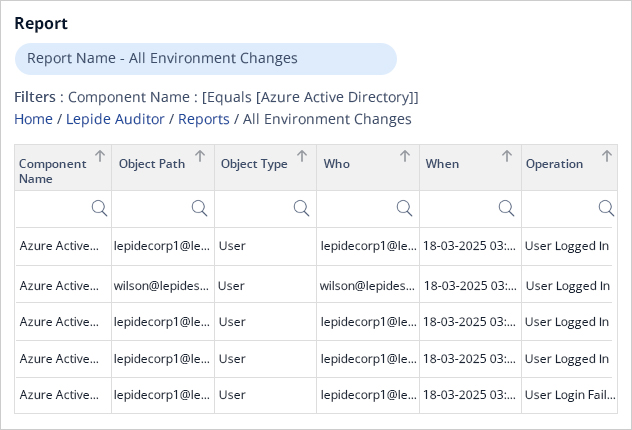
Lepide Auditor for Azure AD simplifies Azure AD sign-in log monitoring by providing real-time visibility into user authentication activities across your environment. It automatically captures and consolidates sign-in events, including successful and failed logins, enabling you to quickly spot suspicious behavior such as unusual login times or locations. This proactive monitoring helps prevent security breaches and supports faster incident response.
The tool offers detailed, easy-to-understand reports that show who logged in, when, and from where, giving you clear insights without the complexity of manual PowerShell scripting. These reports can be scheduled or generated on demand, making compliance audits and security reviews more efficient.