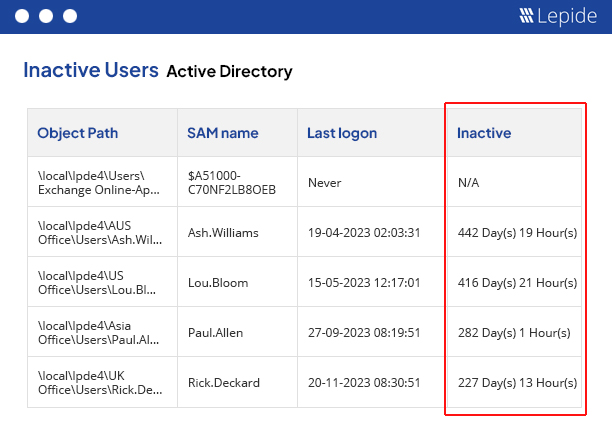
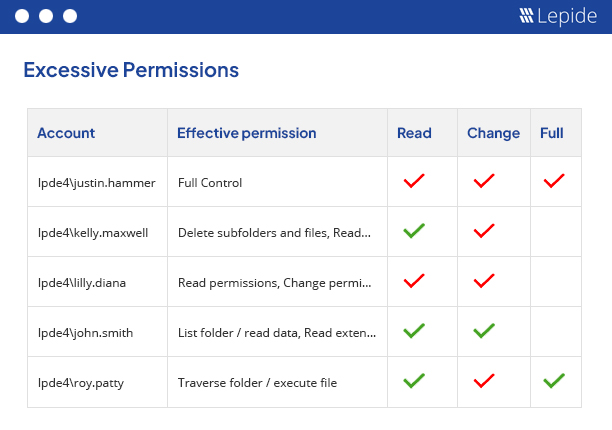
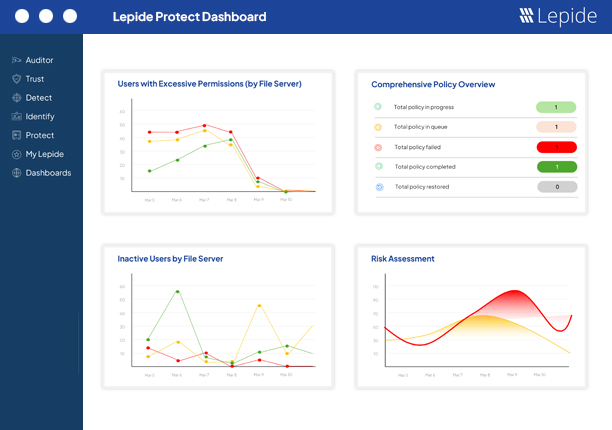
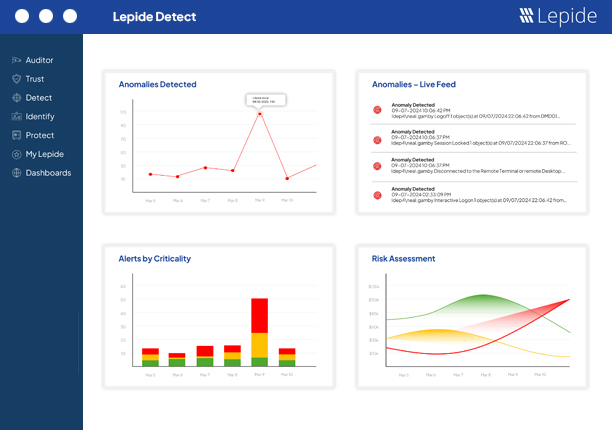
The Lepide
Data Security Platform.
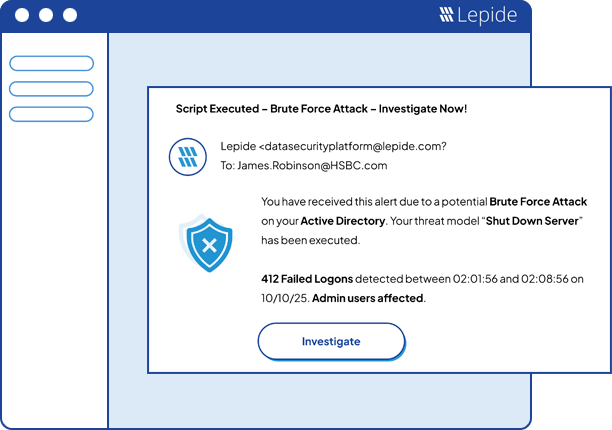
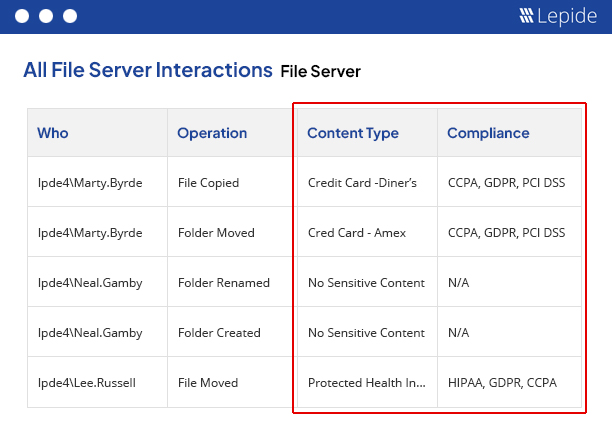
A single solution to help you protect your unstructured data, audit changes made to both on-premises and cloud platforms and meet data privacy and compliance requirements.
download the 20-day free trial