Lepide Auditor
Windows File Server Auditing Software
The easiest, yet most comprehensive way to audit file server changes and data access, track interactions with data and detect threats.
Detailed audit trails and pre-set reports for all file server interactions, including file deletions, file access attempts, file copy events, and file modifications.

See who has access to files/folders, what level of access they have, and where they are getting access from. Track permission changes.

Determine which users have permissions that they do not need and automatically implement least privilege by revoking excessive access using AI-led technology.

Discover and classify data on file server so that you can build a picture of what your risk surface looks like.

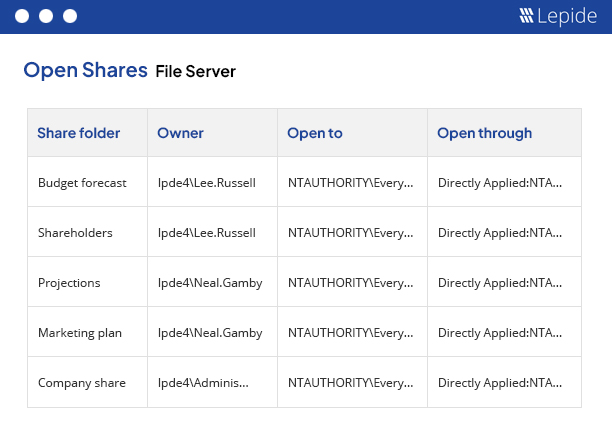
Data open to all users through open shares is a security risk. Generate a list of all open shares and get real time alerts whenever new open shares are created.
Unlike our competitors, we can audit and alert you when your users are copying files with sensitive data.
Lepide Auditor for File Server enables you to audit when files and folders are created, accessed, modified, copied or deleted in file server. We also help organizations track and compare permissions across their file servers and our AI-backed automated permissions management makes revoking permissions a straightforward process. Our File server auditing software addresses common sysadmin challenges, including investigating deleted files, failed access attempts, and generating detailed audit reports. Lepide overcomes the limitations of PowerShell and event logs to provide full Windows File Server auditing capabilities.

Alerts delivered in real time for any events or changes. Automated workflows and threat models for instant visibility and response.

All our reports and dashboards are fully customizable, allowing you to search, sort, and filter to get to the information you need.

Lepide’s file server auditing solution can be deployed on-premises or as SaaS to suit your requirements.
Lepide’s machine learning tool enables you to spot and react to anomalies in what’s happening to your file server.

Get quick, concise answers and summaries of reports by asking our AI helper, Lepide IQ, so that you can interrogate data faster.

Get real time alerts, a live feed of events, and automatic threat response in the palm of your hand.
Get an instant list of all the folders that are open to all of your users so that you can start to implement least privilege and reduce risk.
Download free tool
File server auditing is the process of tracking and logging access to files and folders on a file server (in this case, Windows file server) in order to monitor user behavior, detect unwanted activity, track permissions, and more. In general, file server auditing is a crucial aspect of data security and compliance.
File server auditing works by logging events in the security logs, including things like file and folder access, modifications, and deletions. By logging these events, administrators can track user actions, detect unauthorized access, and enforce security policies.
The most common method companies use to check file server audit logs is using the Event Viewer. Within the Event Viewer (eventvwr.msc), go to Windows Logs → Security and search for event IDs 4656 or 4663 to check access attempts and success access respectively. You will need to ensure auditing is enabled via Group Policy. This method has several obvious drawbacks when compared to Lepide, including being cumbersome, reactive, and difficult to piece together event sequences.
To audit file server permissions natively, you will have to use tools like PowerShell, the Windows File Exporter Security tab, or (more likely) third party file server auditing tools. If using the security event log, you’ll have to search for Event ID 4670 for permission changes.
File server auditing is crucial for tracking unauthorized access, changes, and deletions of sensitive data. It enhances security, ensures compliance with regulations, and helps in identifying and responding to potential data breaches promptly.
Windows file auditing software tracks and logs activities on Windows file servers. It monitors file access, modifications, and deletions, providing detailed reports and alerts to help organizations maintain security and compliance.
Best practices for auditing file servers include defining clear auditing policies, regularly reviewing and updating audit logs, setting up real-time alerts for suspicious activities, ensuring data integrity, and maintaining compliance with regulatory standards.
Spot security threats by monitoring audit logs for unusual file access patterns, unexpected modifications, and unauthorized deletions. Real-time alerts and detailed reports help in quickly identifying and responding to potential security incidents.
File system audit tools monitor and log file access, modifications, permission changes, and any other event occurring on file systems. They typically collect logs and format them in readable reports so that administrators can use them to ensure compliance, track user activities, and identify security threats.