Exchange Server Mailboxes contain high business impact information (HBI) and personally identifiable information (PII), making them a prime target for attackers. Whenever there is non-owner access to a mailbox, it could lead to inappropriate access to sensitive data and so needs to be regularly monitored.
When setting up your Exchange Server, it is essential to define access control rights with the utmost care and ensure that the Principle of Least Privilege (PoLP) is adhered to with users having only the bare minimum of access permissions they need to do their jobs. Once permissions are set up, the regular auditing of Exchange Server permission changes is critical to ensure the security of mailboxes and to meet compliance requirements. Working in this way will mitigate risk and limit the chance of a data breach.
Why Compare Exchange Server Permissions?
Comparing Exchange Server permissions between two dates in time can be beneficial for an IT or security team in several ways:
- User Access Analysis: By comparing Exchange Server permissions, the team can assess any changes in user access rights over time. This analysis helps identify discrepancies, such as users gaining unauthorized access to sensitive email accounts or distribution lists. It allows the team to ensure that only authorized individuals have the appropriate access privileges, reducing the risk of data breaches or unauthorized actions.
- Compliance Verification: Many industries have specific compliance requirements, such as the Payment Card Industry Data Security Standard (PCI DSS) or the Sarbanes-Oxley Act (SOX). Comparing Exchange Server permissions helps validate compliance by ensuring that user access aligns with established policies and regulations. It assists in maintaining proper controls and minimizing the risk of non-compliance-related penalties or breaches.
- Security Incident Investigation: If a security incident or email-related breach occurs, comparing Exchange Server permissions can aid in the investigation. It helps identify if any unauthorized changes were made to user access rights or mailbox permissions that might have facilitated the incident. Analyzing the permissions between two dates provides crucial insights for understanding the scope and impact of the incident and determining the appropriate response.
- Change Management and Auditing: Exchange Server permissions are subject to changes due to various factors, including organizational restructuring, employee onboarding or offboarding, or system updates. By comparing permissions between two dates, the IT team can track and document these changes for auditing purposes. It ensures that all modifications to Exchange Server permissions are properly authorized, documented, and aligned with the organization’s policies.
- Proactive Security Measures: Regularly comparing Exchange Server permissions helps maintain a proactive security stance. It allows the team to identify potential vulnerabilities or suspicious changes in user access before they are exploited. By promptly addressing any unauthorized modifications or anomalous permissions, the team can mitigate security risks and prevent unauthorized access to critical email communications and sensitive information.
Can you Compare Permissions in Exchange Server Natively?
Historic permissions analysis is something that is not possible to do using native tools for Exchange Server, but it can be achieved using the Lepide Data Security Platform.
How to Compare Exchange Server Permissions using Lepide
The Lepide Historic Permissions Analysis Reports allow you to list historic permissions for a specified date range and to compare permissions between two dates. These reports can be generated for Exchange Server, Active Directory and File Server and here, we will look at the Exchange Server Analysis Report.
Exchange Server permission analysis displays the historical changes made in the permissions of Exchange Server objects. The Lepide Solution allows you to compare the permissions for these objects between two date and time intervals. You can also save separate reports on Permission History and Compare Permission in PDF, MHT or CSV formats.
Here is an example of the Exchange Server Analysis Report:
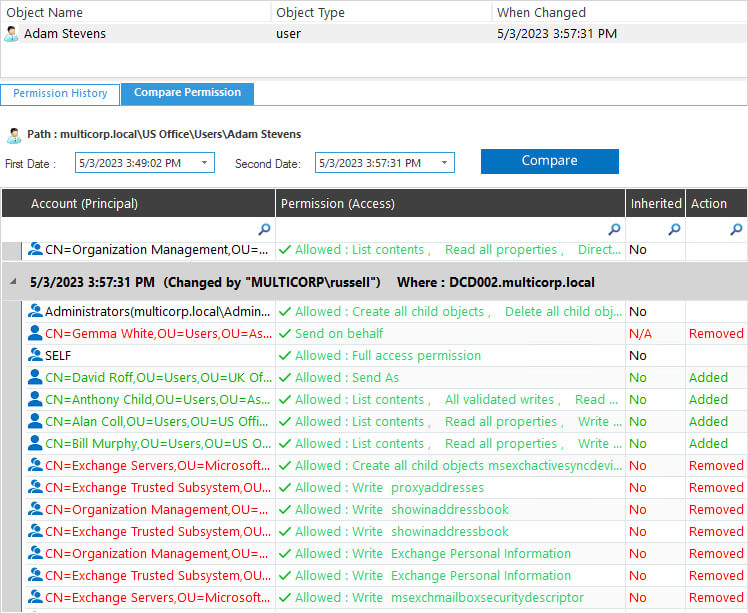
n this example, the dates are both 5/3/2023 but the times are different. They are 3.49 pm and 3.57 pm.
The report shows the permissions that have been changed between those times and who has changed them.
Permissions are color coded for clarity and are as follows:
- Green – permissions have been added
- Blue – permissions have been modified (not shown in this example)
- Red – permissions have been removed
The Exchange Server Analysis Report is straightforward to run:
- From the Permission and Privileges screen, choose Historic Permissions Analysis, Exchange Server Analysis
- Select a date range and click Generate
- Expand the relevant folder to see permission history
- To see the comparison between two dates.
- Click the Compare Permission tab
- Select the First Date and the Second Date and click Compare
- The permissions comparison data will be displayed