Exchange Server Mailboxes contain high business impact information (HBI) and personally identifiable information (PII), making them a prime target for attackers. Whenever there is non-owner access to a mailbox, it could lead to inappropriate access to sensitive data. Knowing when and where a mailbox has been accessed by a non-owner is critical to mailbox security. To ensure the security of a mailbox, it is important to regularly audit the user activities within them. This can be achieved using native Exchange auditing tools. The details of how to do this are below:
Steps to Track Mailboxes Access with Native Auditing
Step 1. Check whether Mailbox Audit Logging is enabled
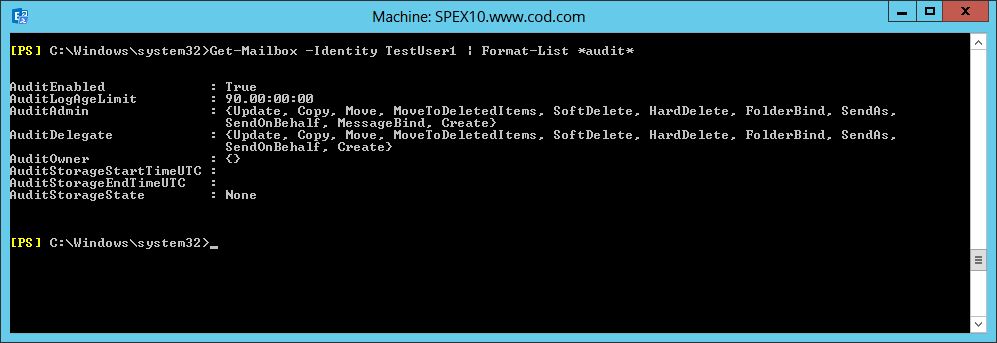
Go to ‘Start’ menu and open the ‘Exchange Management Shell.’ In the Shell, type the below command to get the ‘Exchange Server.’ In the shell, type the following command to verify whether auditing is enabled on a mailbox.
Get-Mailbox –Identity TestUser1 | Format-List *audit*If Audit is enabled, you will get a true value. Under AuditAdmin and Audit Delegate, you will get all the functions the mailbox can perform.
Step 2. Enable-Mailbox Audit Logging
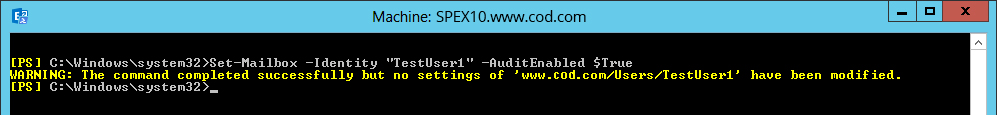
To enable mailbox audit logging, type the below command in Exchange Management Shell:
Set-Mailbox -Identity “TestUser1” -AuditEnabled $TrueThis command enables audit for TestUser1
Step 3. Enable-Mailbox audit logging for users and operations
Administrators, delegates or owners can enable mailbox auditing for specified operations. Run the below commands in Exchange Management Shell:
Set-Mailbox -Identity “TestUser1” -AuditAdminHardDelete, SoftDelete -AuditEnabled $TrueSet-Mailbox -Identity “TestUser1” -AuditDelegateSendAsSendOnBehalf -AuditEnabled $TrueSet-Mailbox -Identity” TestUser1” -AuditOwnerMoveToDeletedItems –AuditEnabled $True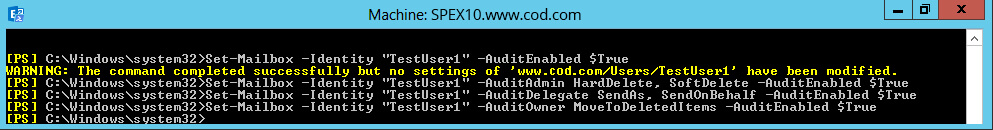
Step 4. Get-Mailbox audit log data for one or more mailboxes
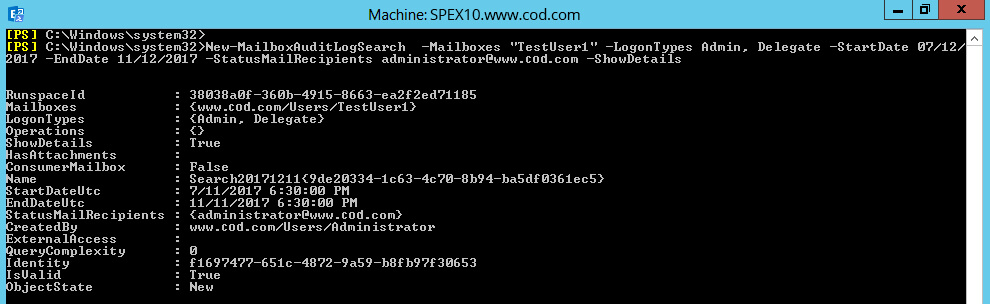
To get the audit log data by email (for TestUser1 mailbox), run:
New-MailboxAuditLogSearch –Mailboxes “TestUser1” –LogonTypes admin, Delegate –StartDate 07/12/2017 –EndDate 11/12/2017 –StatusMailRecipientsadministrator@www.domain.com –ShowDetailsHere, you will get information on logon details, start and end audit date, and recipients mail address on which you will receive mail.
An Administrator can also view the audit log for mailbox access in the Exchange Administrative Center.
Issues with the Native Method
The above method requires a sound knowledge of Exchange Management Shell. It can also be time-consuming and complex to perform. Using the native method may also be too reactive, meaning you could miss the chance to prevent a security breach before it spirals out of control. Administrators also have to create the audit entries manually for an audit report, which can be time consuming.
Audit Mailbox Access with Lepide Exchange Server Auditor
Auditing non-owner mailbox access is a vital aspect of ensuring your mailboxes remain safe and secure. In order to truly ensure that you know what is happening within your Exchange Server, it may be wise to deploy a proactive solution like Lepide Exchange Server Auditor (part of Lepide Data Security Platform).
Following report shows all non-owner accesses made to a user mailbox.
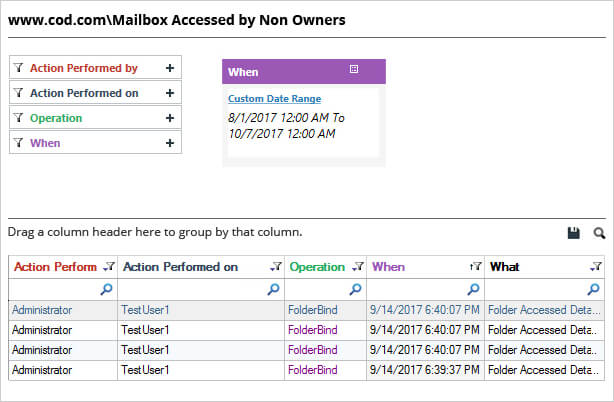
The above report gives details of who accessed a mailbox (user or a group), when and from where. You get all these details in one single record.