Significant improvements have been made to Active Directory (AD) functionality, reliability, and security over the years and one of these changes was a move towards a Single Master Model. This meant that just one Domain Controller (DC) could make changes to the domain. However, this was a problem as if the master DC went down, as no changes could be made at all until it was back up again.
The solution was to separate the responsibilities of the DC into several roles. This meant that if one of the DCs went down, another one could take over the missing role. This is known as Flexible Single Master Operation (also known as FSMO or FSMO Roles).
There are 5 Flexible Single Master Operations (FSMO) roles:
- Domain Naming Master (forest-wide role)
- Schema Master (forest-wide role)
- PDC Emulator (domain-wide)
- RID Master (domain-wide)
- Infrastructure Master (domain-wide)
Why Transfer FSMO Roles?
Initially, all 5 roles are assigned to the first domain controller created in a forest. If the forest contains multiple domains, the first DC created in each new domain will own all 3 of the domain-wide FSMO roles for that domain.
However, many organizations have multiple domain controllers in each domain of the forest to ensure the smooth running of their system if a component fails. In this case, they do not need to leave all master operations roles assigned to the original FSMO role holder. The recommendation from Microsoft is that the FSMO roles are carefully distributed and standby DCs are ready to take over each role.
An additional recommendation which Microsoft suggests is that the 2 forest-wide roles, Domain Naming Master and Schema Master, should be on the same DC and the PDC Emulator and RID Master roles should be on the same DC.
Here are some of the reasons why transferring FSMO roles to another DC may be required:
- A domain controller is being demoted: The FMSO roles are transferred automatically when demoting a domain controller. However, you can’t choose which domain controller it’s transferred to during the process, so you may want to manually transfer the FSMO role.
- Change of IP address for the Domain Controller
- The operating system of a DC is being upgraded: during hardware upgrades or operating system migrations, transferring FSMO roles ensures their availability on the new infrastructure.
- Domain controller failure: In the event of a domain controller failure, transferring FSMO roles to another domain controller helps maintain the continuity of Active Directory operations.
- Removing a DC from service for maintenance
What to Check before Transferring FSMO Roles?
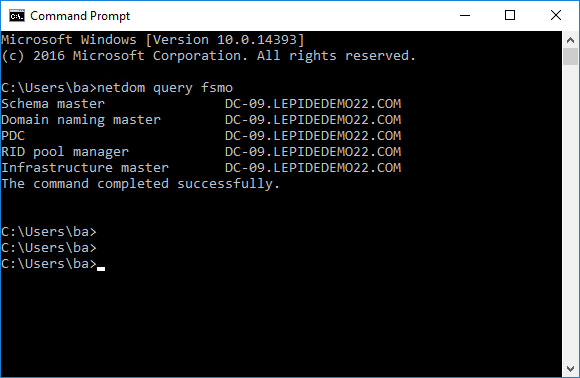
Before FSMO roles are transferred, it’s a good idea to check how the FSMO roles are assigned now. To do this, we can use the netdom query tool which requires a single command or PowerShell which requires two cmdlet commands.
List Current FSMO Role Holders using netdom: netdom query fsmo
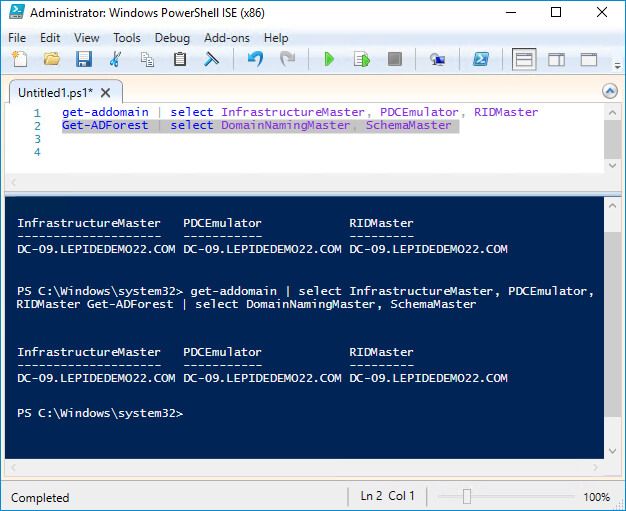
List Current FSMO Role Holders using PowerShell: You can list which domain controllers hold FSMO roles with these two PowerShell commands:
To get domain level FSMO roles:
get-addomain | select InfrastructureMaster, PDCEmulator, RIDMaster
To get forest level FSMO roles:
Get-ADForest | select DomainNamingMaster, SchemaMaster
To perform the FSMO roles transfer, the user account must be a member of the appropriate administrator group, as shown below:
- Schema Master and Domain Naming Master: A user must be a member of the Enterprise Admins group
- RID Master, PDC Emulator and Infrastructure Master: A user must be a member of the Domain Admins group
How to Transfer FSMO Roles using ADUC and PowerShell?
The following steps explain how to transfer roles using the native methods of ADUC and PowerShell.
1. Transfer FSMO Roles Using Active Directory Users and Computers (ADUC)
To Transfer the Domain-Specific RID Master, PDC Emulator, and Infrastructure Master FSMO Roles:
- Open Active Directory Users and Computers (ADUC) from the Administrative Tools folder
- If you are NOT logged onto the target domain controller, right-click the icon next to Active Directory Users and Computers and press Connect to Domain Controller
- Select the domain controller that will be the new role holder, the target, and click OK
- Right-click the Active Directory Users and Computers icon again and select Operation Masters
- Select the appropriate tab for the role you wish to transfer and click the Change button
- Click OK to confirm the change
- Click OK
To Transfer the Domain Naming Master Role:
- Open Active Directory Domains and Trusts from the Administrative Tools folder
- If you are NOT logged onto the target domain controller, right-click the icon next to Active Directory Domains and Trusts and select Connect to Domain Controller
- Select the domain controller that will be the new role holder and click OK
- Right-click the Active Directory Domains and Trusts icon again and select Operation Masters
- Click Change
- Click OK to confirm the change
- Click OK
To Transfer the Schema Master Role
Register the Schmmgmt.dll library:
- Click Start, Run and type regsvr32 schmmgmt.dll
- Click OK and you will receive a success confirmation
- From the Run command open an MMC Console by typing MMC
- On the Console menu, select Add/Remove Snap-in
- Click Add. Select Active Directory Schema
- Press Add and click Close, OK
- If you are NOT logged onto the target domain controller, right-click the Active Directory Schema icon in the Console Root and click Change Domain Controller
- Press Specify and type the name of the new role holder. Click OK
- Right-click the Active Directory Schema icon again and click Operation Masters
- Click Change
- Click OK
2. Transfer FSMO Roles Using PowerShell
You can move or transfer FSMO roles using the PowerShell ‘Move-ADDirectoryServerOperationMasterRole’ cmdlet. The syntax is as follows:
Move-ADDirectoryServerOperationMasterRole -Identity -OperationMasterRole -Server
- Identity sets the domain controller (DC) you want to assign the role(s) to
- OperationMasterRole specifies the role(s) you want to seize. You can specify the roles by name or number
- To move the PDC Emulator role:
Move-ADDirectoryServerOperationMasterRole -Identity " DCD01" -OperationMasterRole PDCEmulator - To move RID Master
Move-ADDirectoryServerOperationMasterRole -Identity ” DCD01″ -OperationMasterRole RIDMaster
- To move Infrastructure Master
Move-ADDirectoryServerOperationMasterRole -Identity " DCD01" -OperationMasterRole InfrastructureMaster - To move Schema Master
Move-ADDirectoryServerOperationMasterRole -Identity ” DCD01″ -OperationMasterRole SchemaMaster
- To move Domain Naming Master
Move-ADDirectoryServerOperationMasterRole -Identity "DCD01" -OperationMasterRole DomainNamingMaster
How Lepide Helps
Lepide Active Directory Auditor provides detailed, real-time audit trails for all changes and events within Active Directory, including who made the change, what was changed, when, and where it happened. It offers multiple customizable audit reports covering activities such as group membership changes, failed logons, account lockouts, and permission modifications, helping organizations detect unauthorized access and track changes that could compromise security.
The platform delivers instant alerts for any significant events or suspicious activities, supports automated workflows for rapid incident response, and enables rollback of unwanted or unplanned changes to their original state. Lepide also includes user behavior analytics and machine learning to spot anomalies, as well as tools to analyze effective permissions and reverse unwanted permission changes.