
Auditing successful and failed logon and logoff attempts in the Active Directory is a vital element of identity security and robust data security strategy. Being able to identify whether users are attempting to, or even successfully logging on outside of business hours, for example, will help you spot threats.
In this blog, we will go through the process of auditing login and logoff events using the Event Viewer in Active Directory. We will also talk briefly about the challenges of this method and suggest a better way.
“Audit Logon Events” and “Audit Account Logon Events”, meant for monitoring the logon/logoff events, are disabled by default. It is required to enable these policies manually. Before going to learn how to enable these policies, it is important to know in brief about them.
Audit Logon Events policy defines the auditing of every user attempt to log on to or log off from a computer. The account logon events on the domain controllers are generated for domain account activities, whereas these events on the local computers are generated for the local user account activities.
Audit Account Logon Events policy defines the auditing of every event generated on a computer, which is used to validate the user’s attempts to log on to or log off from another computer. Such account logon events are generated and stored on the domain controller when a domain user account is authenticated on that domain controller. For local user accounts, these events are generated and stored on the local computer when a local user is authenticated on that computer.
Steps to track logon/logoff events in Active Directory:
- Step 1 – Enable ‘Audit Logon Events’
- Step 2 – Enable ‘Audit Account Logon Events’
- Step 3 – Search Related Logon and Logoff Event Logs in Event Viewer
Step 1 – Enable ‘Audit Logon Events’
-
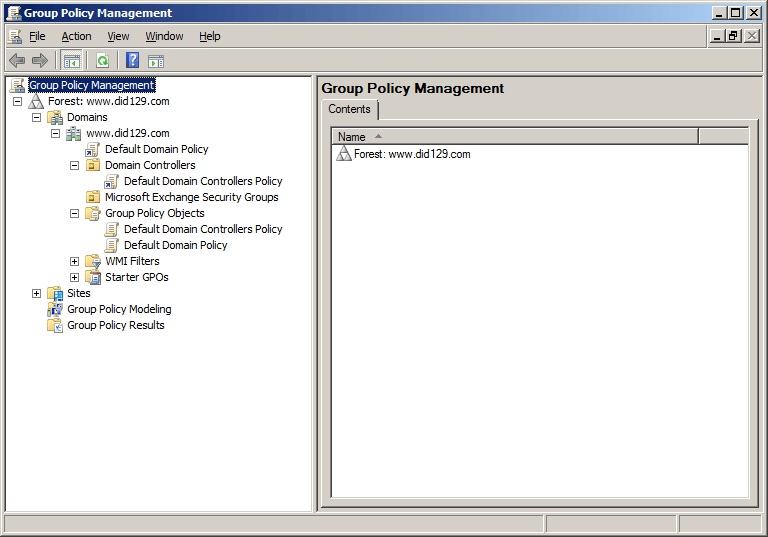
- Run gpmc.msc command to open Group Policy Management Console
-
- If you want to apply this on the whole domain then Right-click on the Domain Object and click on Create a GPO in this domain, and Link it here….
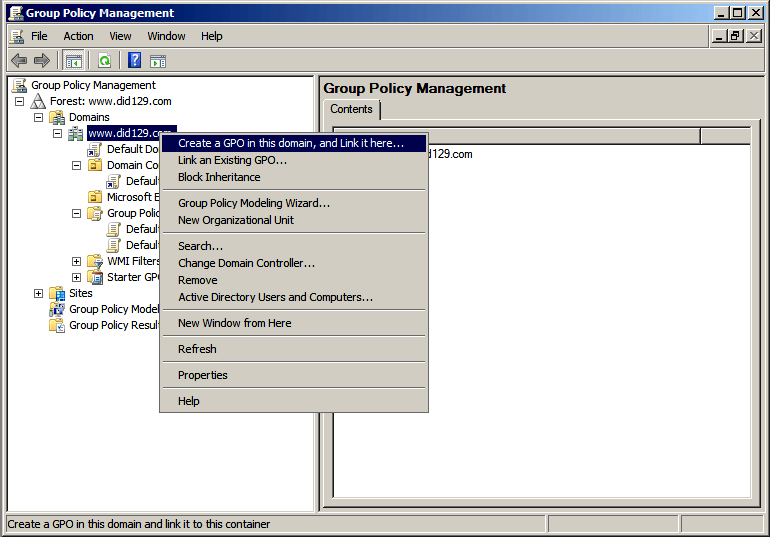
Note- If you do not want to apply this on the whole domain then you can select any OU rather selecting a domain.
-
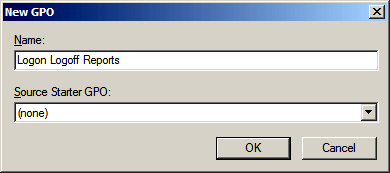
- Write a new GPO name as shown in below image
-
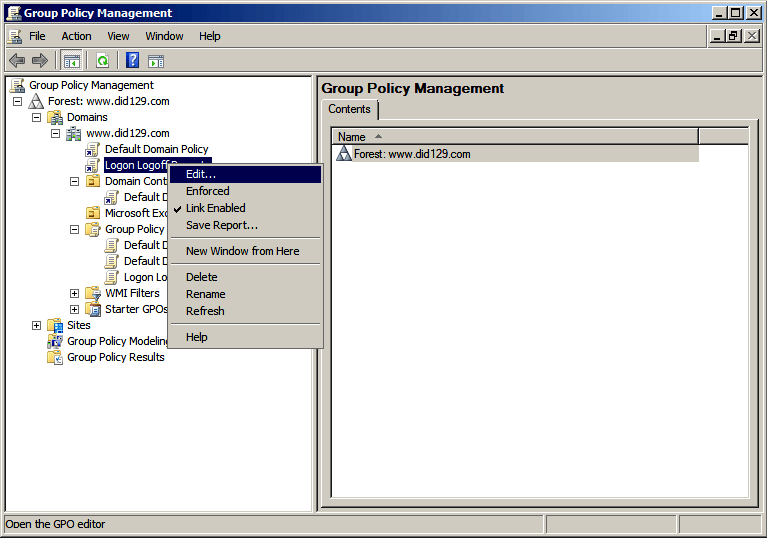
- A new GPO “Logon Logoff Reports” created. Right click on this and click on Edit option
-
- A new window of Group Policy Management Editor (GPME) will open.
- Now under Computer Configuration go to Policies node and expand it as
Policies -> Windows Settings -> Security Settings -> Local Policies -> Audit Policy - In the right hand panel of GPME, either Double click on “Audit logon events” or Right Click -> Properties on “Audit logon events”
- A new window of “Audit logon events” properties will open. Check “Success” and “Failure” boxes and click “Ok”
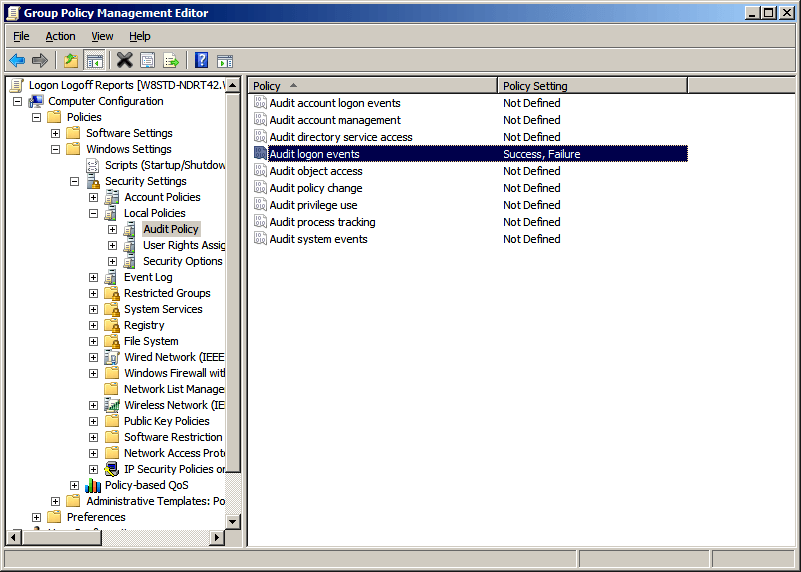
- Now, run gpupdate /force to update GPO
Now, we have successfully enabled “Audit Logon Events”
Step 2 – Enable ‘Audit Account Logon Events’
-
- Run gpmc.msc command to open Group Policy Management Console.
-
- Now, expand Domain Controllers node, Right-click on the “Default Domain Controllers Policy” and click “Edit”.
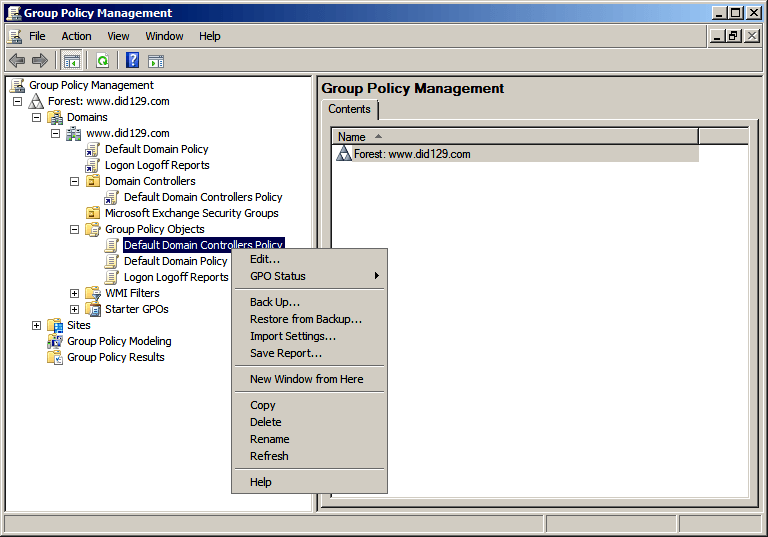
Note- You can also create your own GPO as we did for “Audit Logon Events” in case you do not want to edit Default Domain Controllers Policy.
-
- A new window of Group Policy Management Editor (GPME) will open.
- In GPME windows, expand Computer Configuration, go to “Policies” node and expand it as Policies -> Windows Settings -> Security Settings -> Local Policies -> Audit Policy
- In the right hand panel of GPME, either Double click on “Audit account logon events” or Right Click -> Properties on “Audit account logon events”
- A new window of “Audit account logon events” properties will open. Check “Success” and “Failure” boxes and Click on “OK”
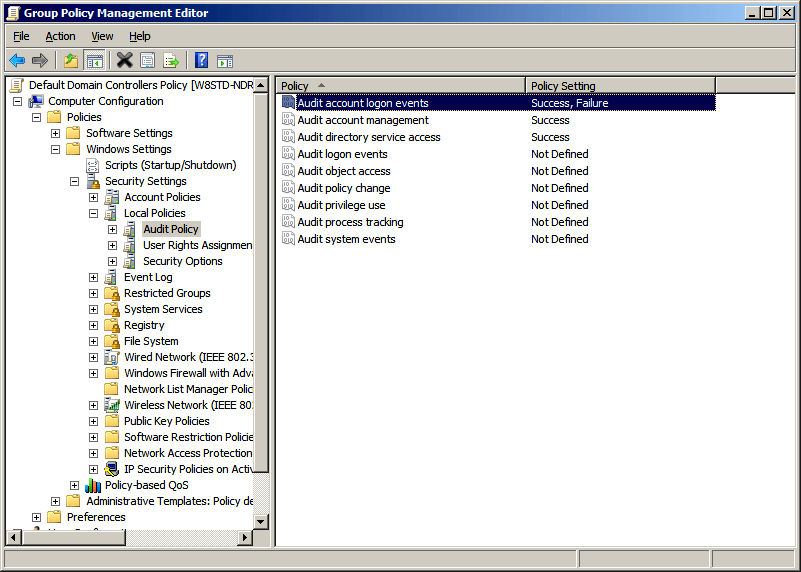
- Now, run gpupdate /force to update GPO
Now, we have successfully enabled “Audit account logon events”
Step 3 – Search Related Logon and Log Off Event Logs in Event Viewer
The event ids for “Audit logon events” and “Audit account logon events” are given below. You have to check these event ids in security logs to track successful logon / logoff and failed login attempts.
Audit Logon Events
| Event ID | Description |
|---|---|
| 4624 | An account was successfully logged on |
| 4625 | An account failed to log on |
| 4648 | A logon was attempted using explicit credentials |
| 4634 | An account was logged off |
| 4647 | User initiated logoff |
| 4672 | Special privileges assigned to new logon |
| 4778 | A session was reconnected to a Window Station |
Audit Account Logon Events
| Event ID | Description |
|---|---|
| 4768 | A Kerberos authentication ticket (TGT) was requested |
| 4769 | A Kerberos service ticket was requested |
| 4770 | A Kerberos service ticket was renewed |
| 4771 | Kerberos pre-authentication failed |
| 4774 | An account was mapped for logon |
| 4776 | The domain controller attempted to validate the credentials for an account |
*Operating System for above ids – Windows Server 2008 or higher
Test Case – Here, we will search Event ID 4625 to track failed logins in Active Directory.
- Go to “Start Menu” ➔ ”All Programs” ➔ ”Administrative Tools” ➔ “Event Viewer”
- In the left panel, go to Windows Logs” ➔ “Security” to view the security logs → Click on ‘Filter Current Log..’
- Enter Event ID 4625 to search for it
- 4. Double-click on event to see its details like account name, date, and time of login failure.
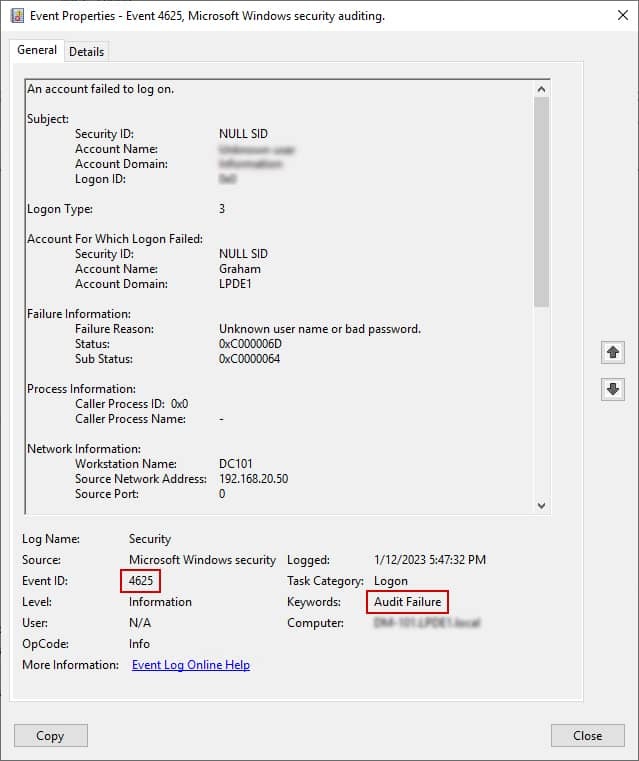
Issues with Native Auditing
The native auditing of Active Directory has numerous drawbacks. Multiple events are generated for a single event and it is very difficult to search for a particular event in the large pool of events. Event Viewer also consumes a lot of disk space to store the events for the long term.
All the above-mentioned procedure to audit successful and failed Logon / Logoff in Active Directory can be simplified with the help of Lepide Active Directory Auditor. With this, you can make the entire auditing process simple and thus helps to maintain a secure AD environment.
How Lepide Active Directory Auditor tracks Logon/Logoff in Active Directory
Lepide Auditor for Active Directory overcomes the limitations of native auditing and provides an easiest way to track all the logon/logoff activities of Active Directory users. See below for an example of both successful logon/logoff activity and failed logins.
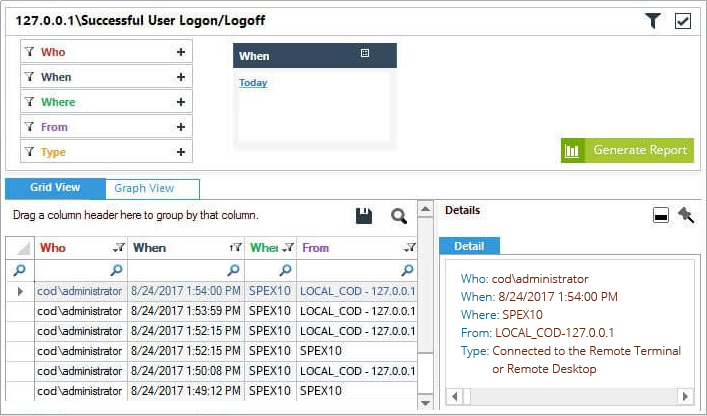 Figure 1: Successful User Logon Logoff report
Figure 1: Successful User Logon Logoff report
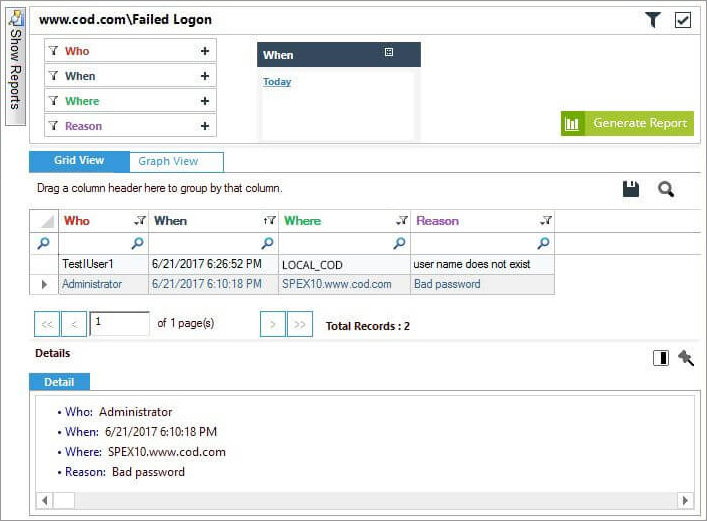 Figure 2: Failed Logon Report
Figure 2: Failed Logon Report
Lepide also makes it easy to spot potentially unwanted user behavior by reporting on when you Active Directory users are logging into Active Directory outside of business hours.
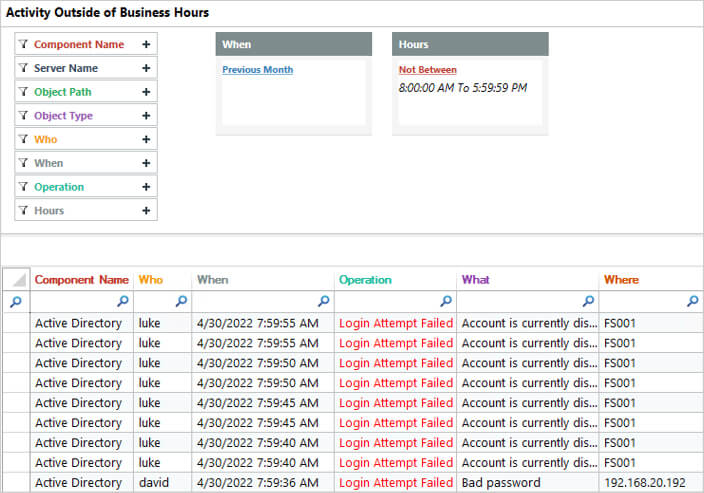 Figure 3: Failed Logon Report Outside Business Hours
Figure 3: Failed Logon Report Outside Business Hours
Lepide is incredibly simple to install and configure and provides instant value through hundreds of pre-set reports. Use the below form to start your free trial and give it go!

 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
