Microsoft Teams and SharePoint Online provide many communication and collaboration tools in one place, and with so many more people now working remotely, this functionality is essential for them to do their jobs effectively. Users can invite anyone with an email address to join a site or team and this includes both internal and external users.
While this flexibility has the advantage of making working as a team from anywhere easy and efficient, it also means that the potential for malicious behavior is increased. It is therefore essential to closely monitor who gets access to your environment and to be able to quickly spot any escalation of permissions.
There are native tools to track this information, but they are limited and time-consuming and it’s difficult to quickly gain the insight you need to spot and block any threats. The Office 365 audit log records changes to group membership and permissions, but there is no easy way to track these activities. To review the details, you must either drill down into each event separately or download the data into a CSV file and analyze it there.
A solution to this time-consuming and complex process is to use the Lepide Auditor. With the Lepide Auditor, you can generate the All Modifications in SharePoint Online Report showing you SharePoint Online privilege escalations within a specified date range.
Here are two ways to audit privilege escalation in MS Teams and SharePoint online and they are described below.
- Using the Native Method
- Using the Lepide Auditor
Using the Native Way for Auditing Privilege Escalation
Please follow the below steps:
- Open the Office 365 Security & Compliance dashboard
- Go to Search, Audit log search
- From the Activities filters, choose Shared file, folder, or site and Unshared file, folder, or site
- Click Search
The search results will list the following: directly granting access rights, adding a user to a group, and changing group rights. The output table will include the following details:
- User — The name of the user who performed the action
- Item — The URL of the SharePoint site or Team where the change was made
- Detail — The user or group to which the change was applied
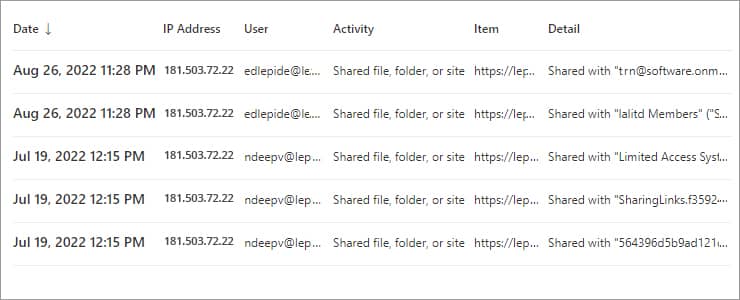
If you want to see whether privilege escalation took place, you will have to look further into the results.
This can be done by clicking the specific event and looking through the Details tab. Depending on the activity, you will need to search for the following information:
- If a user was added to a group with Full Control permissions:
- If rights were granted to a user directly:
EventData:
(Please note that by default, the group with Full Control permissions for a site or team is named [SiteName] Owners)
The EventData:
The Audit Log Search filter capabilities are quite simple and don’t enable you to exclude irrelevant results, so using this method means that you must click through each event individually. An alternative way to find privilege escalation is to export the data to a CSV file and parse the data in Excel as follows:
- To export results to a CSV file, click Export Results, Download all results
- In a new workbook, select the Data Tab, and from the Get & Transform Data section, click Get Data, From File, From Text/CSV and select the CSV file that you previously downloaded. Click Import, Transform Data.
- In the Power Query Editor, right-click the title in the AuditData column. select Transform, choose JSON
In the upper right corner of the AuditData column, click the Expand icon, deselect the properties that you don’t want to include, click OK.
The following properties are examples of those available to be included in the query:
- AuditData.CreationTime — The event timestamp
- AuditData.ClientIP — The IP address from which the event was performed
- AuditData.UserId — The name of the user who performed the action
- AuditData.EventData — The action performed
- AuditData.SiteUrl — The URL of the SharePoint site or Team where the change was made
- AuditData.TargetUserOrGroupName — The user or group to which the change was applied
Privilege Escalation Auditing Using the Lepide Auditor
This native way to audit Privilege Escalation in MS Teams and SharePoint Online is both time-consuming and complex. A more straightforward solution to this is to use the All Modifications in SharePoint Online Report from the Office 365 Auditing component of Lepide Auditor:
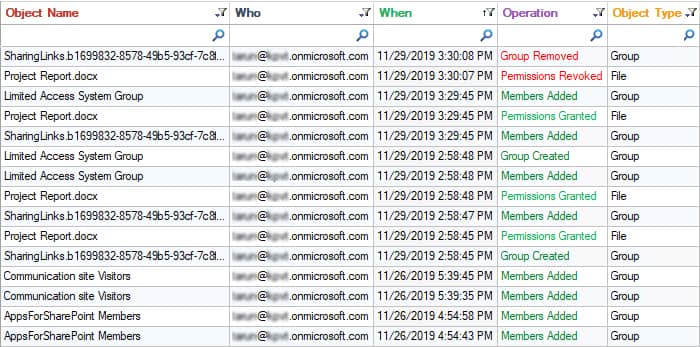
- Click the User & Entity Behavior Analytics icon and select SharePoint Online Modification Reports, All Modifications in SharePoint Online
- Select a Date Range, select the filters you require and click Generate Report
- To see further detail about a specific object, click Details and the Details Window will be displayed
- The report can be sorted, filtered, grouped, saved, and exported
NOTE– Similar process you can follow to generate a report for MS Teams.