Insider threats often prove to be more difficult to defend against than external ones as often insider threats are completely unintentional. However, monitoring events such as user logons, critical files access, privileged accounts, and so on can be an effective way to detect suspicious user activity.
Native Active Directory auditing tools can be used to monitor logon activity, but it is a time-consuming and often complex task. Lepide Auditor overcomes the limitations of native auditing by giving you the visibility you need to detect and react to insider threats quickly and efficiently. This article looks at two ways to identify suspicious insider activity by monitoring logon activity and identifying privileged user accounts and explains two methods to do this:
- Identify Suspicious Insider Activities Using Event Logs
- Identify Suspicious Insider Activities Using Lepide Auditor
Identify Suspicious Insider Activities Using Event Logs
Monitoring Active Directory Logon Activities
- Enable Audit Policy
- Open Server Manager on Windows server.
- From the Tools menu, open the Group Policy Management console.
- Go to Forest, Domain, Your Domain, Domain Controllers.
- You can either edit an existing group policy object or create a new one.
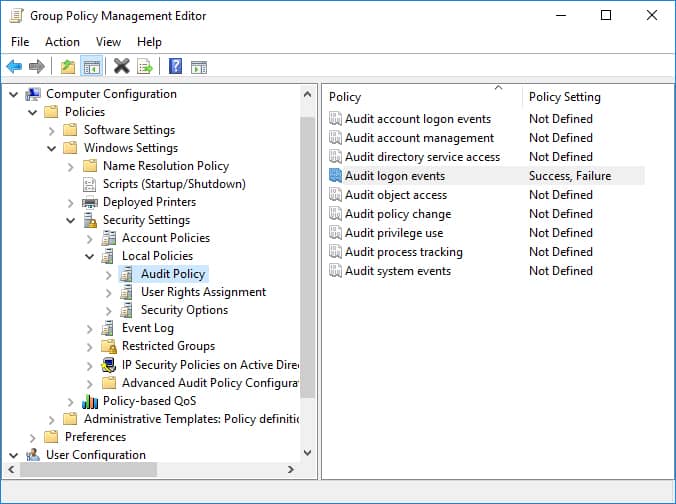
- In the Group Policy Editor, navigate to Computer Configuration, Policies, Windows Settings, Security Settings, Local Policies, and Audit Policy.
- In Audit Policy, select Audit logon events and enable Success and Failure auditing.
- Enable logon-logoff
- Go back to Computer Configuration. Navigate to Windows Settings, Security Settings, Advanced Audit Policy Configuration, Audit Policies, Logon/Logoff.
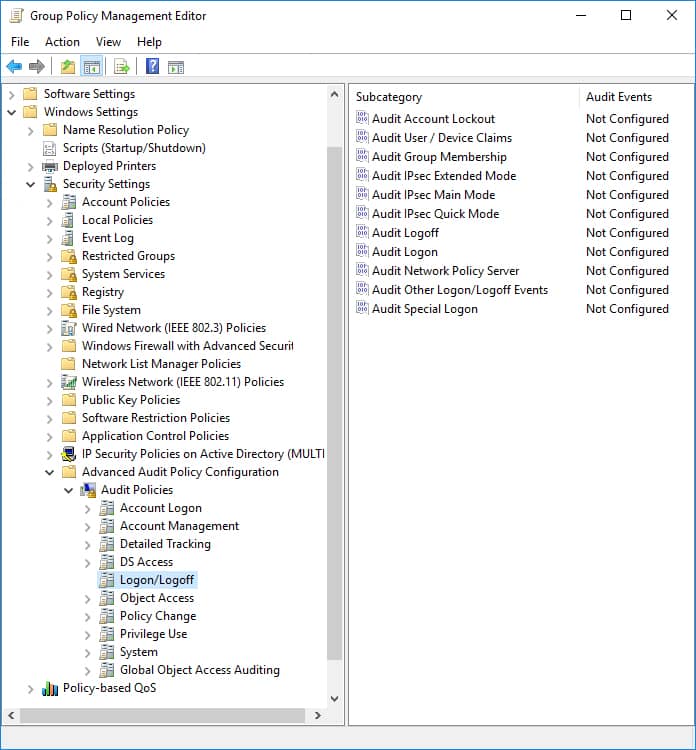
- Next, enable Success and Failure auditing for Audit Logon, Audit Logoff, and Audit Special Logon.
- Open the Group Policy Management console and select the GPO that you have edited or created.
Under Security Filtering, add the users whose logons need to be tracked. You can also choose to audit every domain user’s logon by selecting All Users. To audit, a group of domain users, the specific group(s) can be added.
- Go back to Computer Configuration. Navigate to Windows Settings, Security Settings, Advanced Audit Policy Configuration, Audit Policies, Logon/Logoff.
- Use the Active Directory Event Viewer to check the logs
- Open Event Viewer and navigate to Windows logs, Security.
- Look for the event IDs:
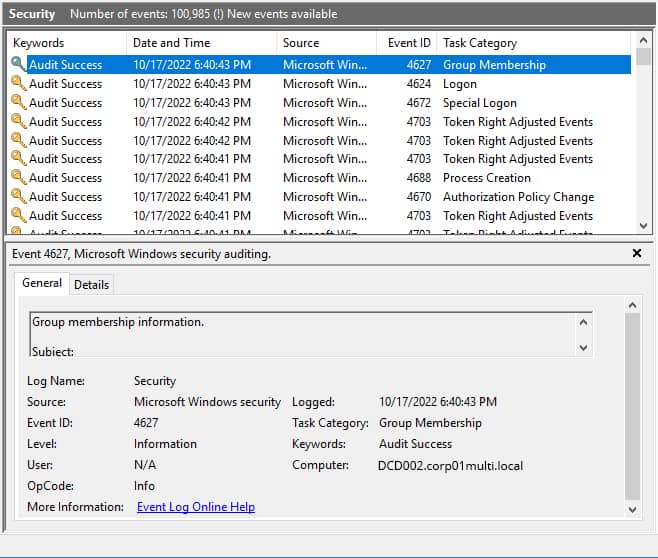
- Click Filter Current Log on the right side to filter the logs based on event IDs or the time range for which the information is required.
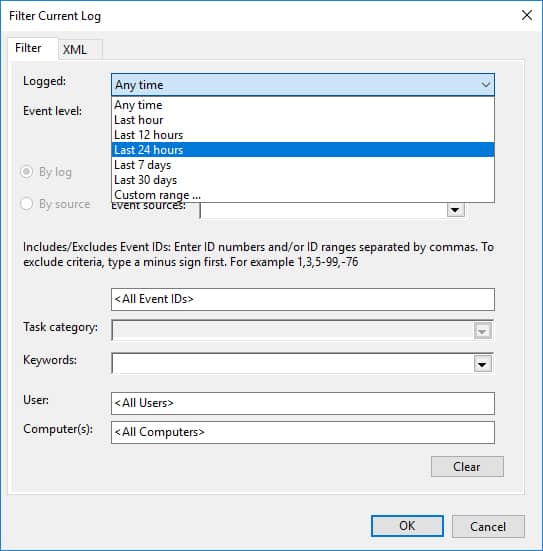
- System admins then need to search through the list of logon times and identify any suspicious patterns. This is a tedious and error-prone process as there are high chance that some logs may be overlooked.
Audit Privileged User Accounts Activities
- Identify the privileged user accounts
- If a domain user satisfies one or more of the below-mentioned criteria, they can be identified as privileged users:
- Users/groups who are members of any of the administrative groups.
- Users/groups who inherit administrative privileges through their Organizational Unit.
- Local user accounts and service accounts that may have received administrative privileges locally on domain controllers.
- Users who have the privileges to reset passwords and unlock the accounts of domain users.
- Users who have administrative privileges through which they can access Service Accounts.
- Users who have ‘write’ access to Group Policy Objects related to domain controllers.
- Users who have access to any application that manages Active Directory.
- Users who are administrators of the Virtual System Environment.
- You can list all the privileged users by using Active Directory Users and Computers, and the Group Policy Management Console.
- If a domain user satisfies one or more of the below-mentioned criteria, they can be identified as privileged users:
- Enable required audit policies
- Open Server Manager on Windows server.
- Under the Manage tab, open the Group Policy Management console.
- Go to Forest, Domain, Your Domain, Domain Controllers.
- You can either edit an existing group policy object or create a new one.
- In the Group Policy Editor, navigate to Computer Configuration, Policies, Windows Settings, Security Settings, Local Policies, Audit Policy.
- The Audit Policy lists all its sub-policies on the right-hand side of the screen, as shown in the example below.
- Select the policies you want to enable for both its successful and failure events. In the event of multiple failures, the organization can initiate security protocol, if necessary.
- Click Apply and OK to close Properties window

- Configure the advanced audit policy
- Launch Server Manager in your Windows Server instance.
- Under Manage, select Group Policy Management to launch the Group Policy Management console.
- Navigate to Computer Configuration, Windows Settings, Security Settings, Advanced Audit Policy Configuration, and System Audit Policies.
- Select the required Audit Policies you want to enable and select both Success and Failure events.
- Force audit policy subcategory settings to override audit policy category settings in Group Policy to make sure that basic auditing is disabled.
- View the events using Windows Event Viewer
- Search using the Find option or create a custom view to display the events generated by a specific privileged account.
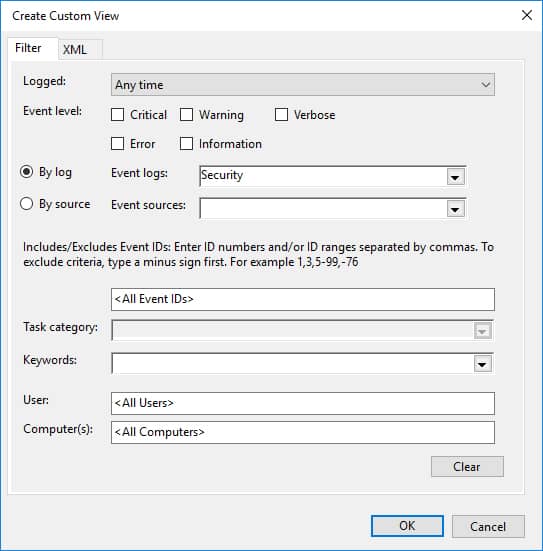
- Search using the Find option or create a custom view to display the events generated by a specific privileged account.
Identify Suspicious Insider Activities Using Lepide Auditor
Lepide Auditor for Active Directory overcomes the complexity of the native method by providing a straightforward way to identify suspicious insider activity using Active Directory by using Logon/Logoff Reporting and the Object Modifications Report.
Audit Logon Activities
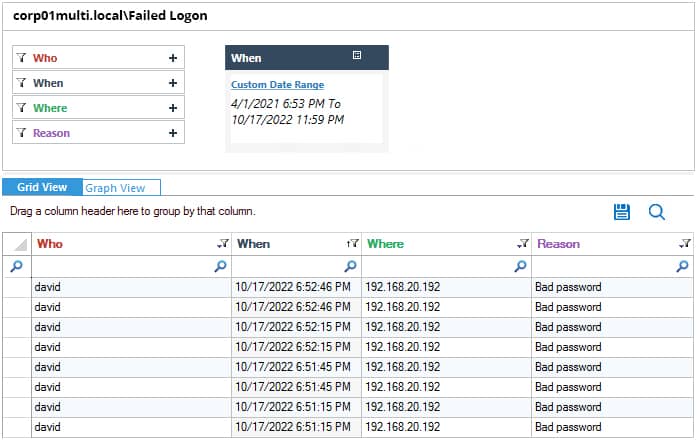
Below are the steps to run the Failed Logon Report in Lepide Auditor:
- Click the User & Entity Behavior Analytics icon and select Active Directory Reports, Logon/Logoff Reports, Failed Logon
- Select a Date Range and click Generate Report
- The report is generated and can be sorted, filtered, grouped, saved, and exported.
Privileged Account Monitoring
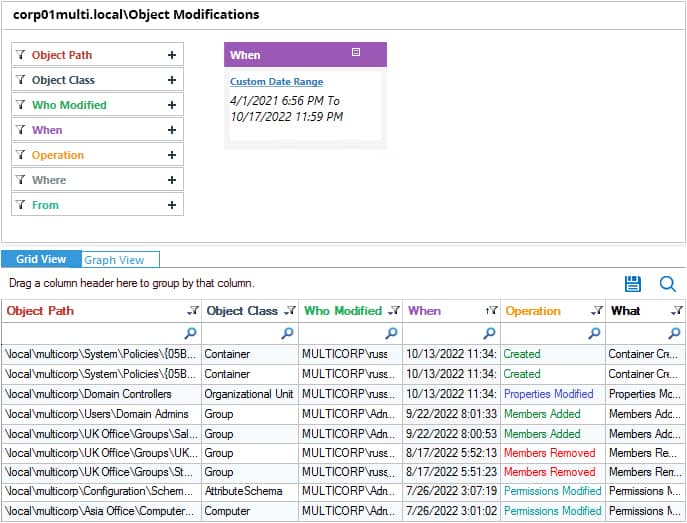
Follow the below-given steps to run the Object Modifications Report in Lepide Auditor
- Click the User & Entity Behavior Analytics icon and select Active Directory Reports, Active Directory Modification Reports, Object Modifications
- Select a Date Range and click Generate Report
- To see further detail about a specific object, click Details and the Details Window will be displayed
- The report is generated and can be sorted, filtered, grouped, saved, and exported.