Tracking logon and logoff time in Active Directory is an essential requirement for security and compliance regulations. One indication of a compromised user account is when a user logs on outside of business hours, or outside of their normal working pattern and this could happen because either their account has been compromised or they plan to act maliciously. There are of course situations when users have legitimate reasons to log on outside of their normal working pattern but by monitoring all user logon/logoff activity, anomalies can be detected, and potential security threats mitigated.
In this article, we will discuss how to configure and track logon/logoff time first by using native tools followed by how to do this in a much simpler way using the Lepide Auditor.
Step 1: Configure the Audit Policies
- Go to “Start” ➔ “All Programs” ➔ “Administrative Tools”. Double-click “Group Policy Management” to open its window.
- In the “Group Policy Management” console navigate to “Forest” ➔ “Domains” ➔ “www.domain.com”.
- Under the “Domain Controllers” node, right-click any customized policy. Click “Edit” to access the “Group Policy Management Editor”.
Note: We recommend that you create a new GPO, link it to the domain and edit it.
- Go to “Computer configuration” ➔ “Policies” ➔ “Windows Settings” ➔ “Security Settings” ➔ “Advanced Audit Policy Configuration” ➔ “Audit Policies” ➔ “Logon/Logoff”.
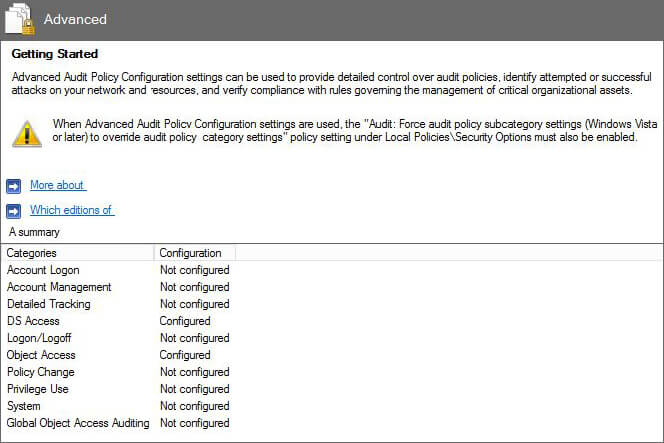
Figure 1: Group Policy Management Editor - You have to configure the following policies:
- Audit Logon
- Audit Logoff
- Audit Other Logon/Logoff
- Double-click “Audit Logon” to access its properties.
- Click to select “Configure the following audit events”.
- To audit successful and failed events, click both the “Successful” and “Failure” checkboxes.
- Click “Apply” and “Ok”. Repeat the steps for the “Audit Logoff” and “Audit Other Logon/Logoff” policies.
- Close “Group Policy Management Editor”.
- In “Group Policy Management Console”, select the GPO that you have modified. In the “Security Filtering” section in the right pane, click “Add” to add “Everyone” for applying this policy to all Active Directory objects.
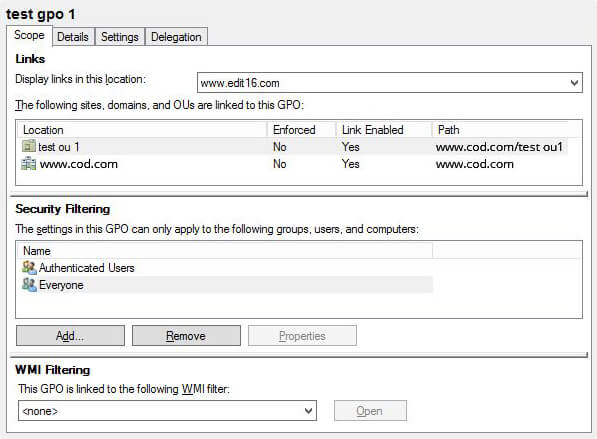
Figure 2: Group Policy Management Console - Close “Group Policy Management Console”.
- At the “Run” prompt or in “Command Prompt”, run the following command to update the group policies.
gpupdate /force
Step 2: Track Active Directory User Logon Session Time using Event logs
Perform the following steps in the Event Viewer to track session time:
- Go to “Windows Logs” ➔ “Security”.
- Open “Filter Current Log” on the rightmost pane and set filters for the following Event IDs. You can also search for these event IDs.
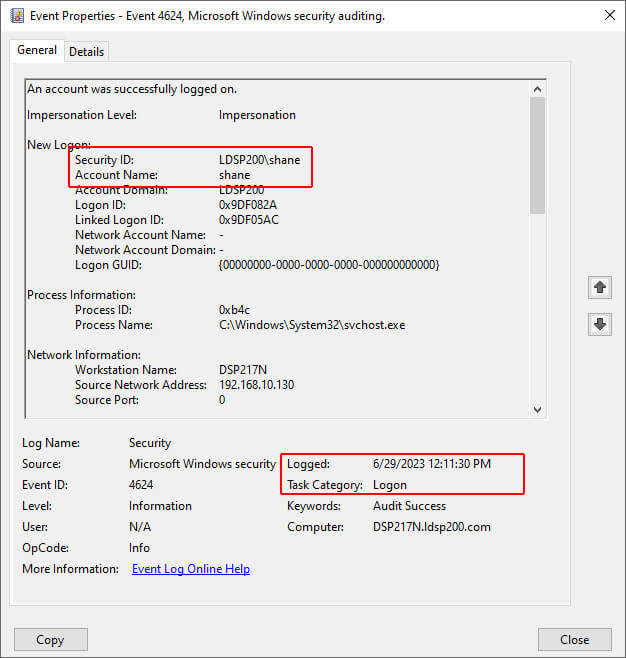
- Double-click the event ID 4624 to access the Event Properties. The session start time is displayed as Logged. In the Event Properties given below, a user, Shane, had logged in on 6/29/2023 at 12:11:30 PM.
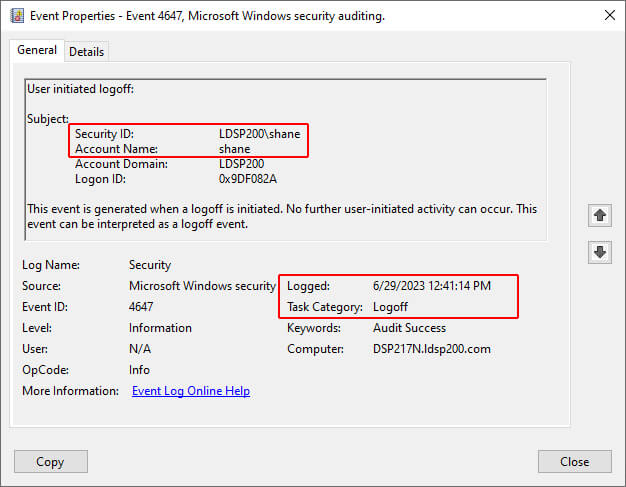
- The session end time (which can be obtained using the Event ID 4647 shown in the below screenshot) is 6/29/2023 at 12:41:14.
You can obtain the user’s logon session time using these details.
This process becomes quite complicated and time-consuming when you have to track logon session time for multiple users. In the majority of cases, it simply isn’t practical to rely on event logs for this information. To get the exact session time; you need to consider the very first logon and logoff time displayed in the event properties.
How to Use Lepide Active Directory Auditor to check User Logon Session Time
With cutting-edge Active Directory auditing software, like Lepide Auditor for Active Directory, monitoring and controlling the network activities of your organization is simple. Lepide offers real-time reports with granular details of all event activities. The Logon/Logoff reports generated by Lepide Active Directory Auditor mean that tracking user logon session time for single or multiple users essentially becomes an automated process.
The screenshot given below shows a report generated for Logon/Logoff activities:
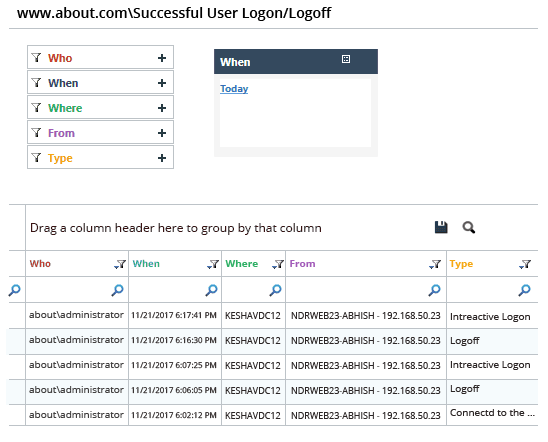
Why You Need to Be Using Lepide to Audit Logon/Logoff Events
In this article, we went through the steps you need to take if you want to audit logon/logoff events using the Event Logs themselves. Clearly, this is not the most effective and sensible way to conduct your Active Directory auditing. Event logs are noisy, they don’t contain a lot of contexts, and for more complex auditing tasks, they simply do not provide enough information to be of any use.
An easier and more efficient way to audit logon/logoff activities, along with other critical events in Active Directory, is to use Lepide Auditor for Active Directory.

