Understanding and properly configuring file server permissions is crucial for permissions management, access control, and ensuring data security within an organization.
Best practice recommends managing permissions through group membership rather than assigning them directly to individuals. This ensures that sensitive information is protected, unauthorized access is prevented, and users can perform their tasks without compromising data integrity.
By determining how permissions are assigned and identifying users who have been granted direct file server permissions, you can remove inappropriate access and strengthen both your IT systems and your permissions management strategy.
In this guide, we will look first at the native way of using PowerShell to find users who have direct permissions on file shares and then look at a more straightforward approach using the Lepide Data Security Platform.
Using PowerShell
Open the PowerShell ISE on your file server and create a new script with the following code:
$search_folder = "\\share\path\"
$out_file = "C:\temp\directpermissionsexport.csv"
$out_error = "C:\temp\errors.csv"
$items = Get-ChildItem -Path $search_folder -recurse
$found = @()
$errors = @()
ForEach ($item in $items) {
try {
$acl = Get-Acl $item.fullname
ForEach ($entry in $acl.access) {
If (!$entry.IsInherited) {
$found += New-Object -TypeName PSObject -Property @{
Folder = $item.fullname
Access = $entry.FileSystemRights
Control = $entry.AccessControlType
User = $entry.IdentityReference
Inheritance = $entry.IsInherited
}
}
}
} catch {
$errors += New-Object -TypeName PSObject -Property @{
Item = $item.fullname
Error = $_.exception
}
}
}
$found |
Select-Object -Property Folder,User,Control,Access,Inheritance |
Export-Csv -NoTypeInformation -Path $out_file
$errors |
Export-Csv -NoTypeInformation -Path $out_err
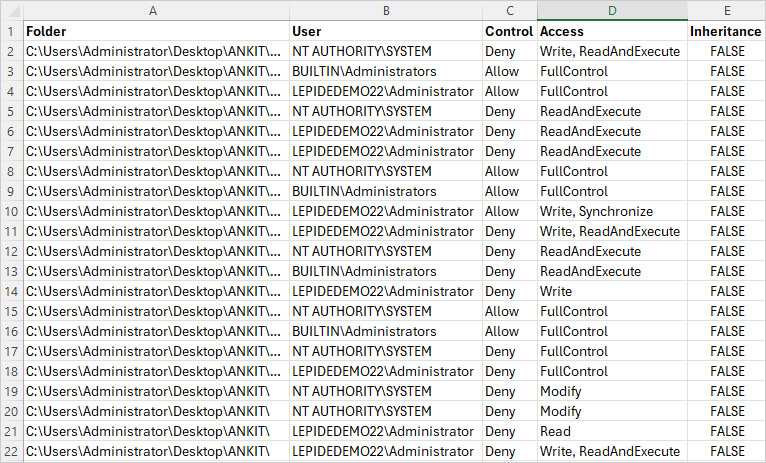
Specify the parameters below and run the script:
$search_folder: enter a path to a shared folder you want to inspect for direct permissions
$out_file: enter a path to a file with results
$out_error: enter a path to an error log file
Using the Lepide Data Security Platform
A more straightforward approach, which requires no knowledge of PowerShell scripting, is to use one of the many pre-defined reports included within the Lepide Data Security Platform. The following is an example of the Permissions by Object Report which shows how permissions have been derived:
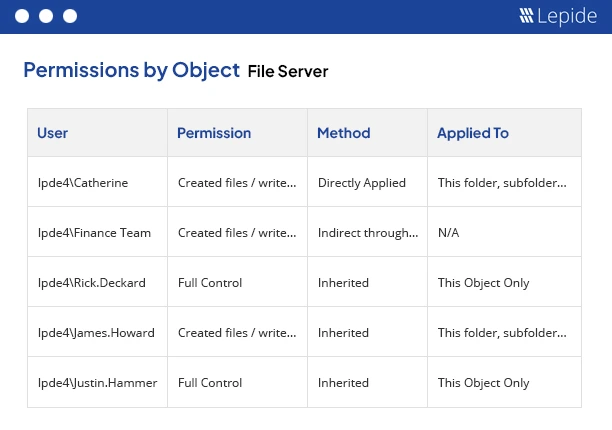
To run this report:
- Select Lepide Trust, Reports
- From here, expand Current Permission Analysis
- Select Permissions by Object
- Select Generate Report
- Expand the File Server icon and permissions for the selected folder will be displayed
The report can be filtered, sorted and exported to CSV and PDF formats.