In this post, I’ll show you how to use PowerShell to generate an NTFS permissions report, an essential part of effective permissions management. If you’re responsible for managing permissions across files and folders, especially in enterprise environments, understanding how to extract and analyze access control data is important. This guide demonstrates how the Get-Acl cmdlet can be used to retrieve detailed permission information.
How to use Get-Acl to find NTFS Permissions Report on Files, Folders and Subfolders
The PowerShell Get-Acl cmdlet can be used to return permissions on objects like files, folders, and registry keys. The example below gets the permissions set on the C:\temp folder and all the available properties.
(Get-Acl -Path C:\temp).AccessGet-Acl cannot recursively return all the permissions of folders in the hierarchy. So, if you want to know the permissions set on all folders in a directory tree, you need to use the Get-ChildItem cmdlet with the -Recurse parameter to list all the folders in the tree and then pass the results to Get-Acl using a ForEach loop.
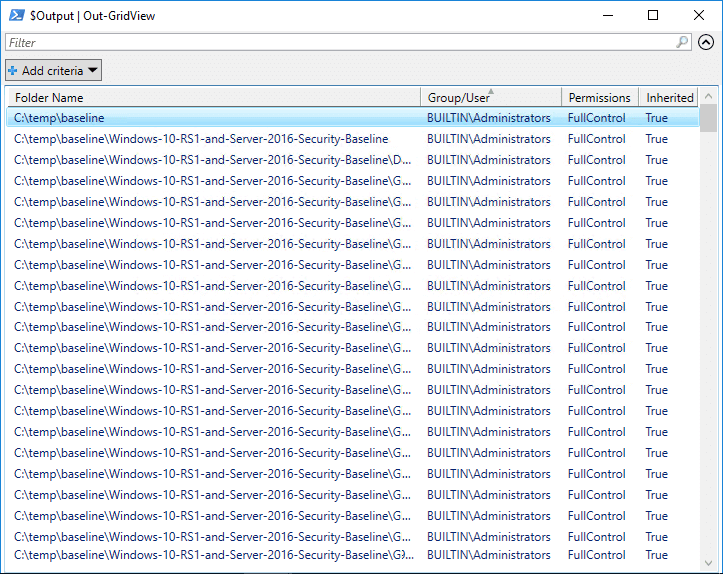
The script below puts the folder hierarchy into a variable ($FolderPath) and then passes each folder to Get-Acl in the first ForEach loop. A second ForEach loop formats each access control entry (ACE) into an ordered list, pulling out just the information that we need, making the results easy to read. The final output ($Output) is then piped to Out-GridView so that you can sort and filter the results.
$FolderPath = Get-ChildItem -Directory -Path "C:\temp" -Recurse -Force
$Output = @()
ForEach ($Folder in $FolderPath) {
$Acl = Get-Acl -Path $Folder.FullName
ForEach ($Access in $Acl.Access) {
$Properties = [ordered]@{'Folder Name'=$Folder.FullName;'Group/User'=$Access.IdentityReference;'Permissions'=$Access.FileSystemRights;'Inherited'=$Access.IsInherited}
$Output += New-Object -TypeName PSObject -Property $Properties
}
}
$Output | Out-GridViewHow Lepide Helps
It’s critical that you understand both current and historic File Server permissions to help prevent privilege abuse and maintain a policy of least privilege. Our Lepide File Server Auditor can easily analyze current effective permissions held by users on files and folders, as well as changes made to permissions, inherited permissions, direct permissions and indirect permissions. Click here to know more.
The following screenshot of Lepide File Server Auditor shows current permissions by users:
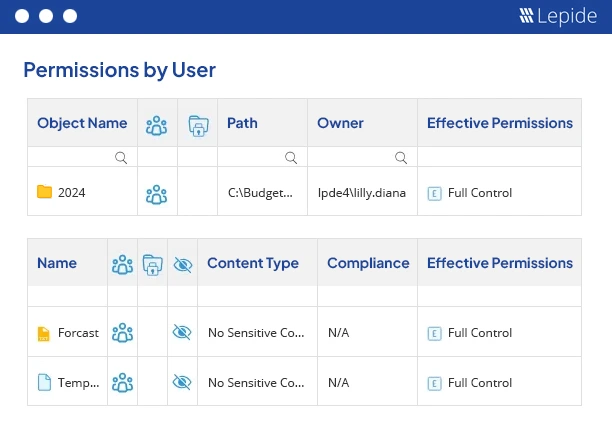
In addition to the permissions reports shown above, you can also remove excessive for an object.
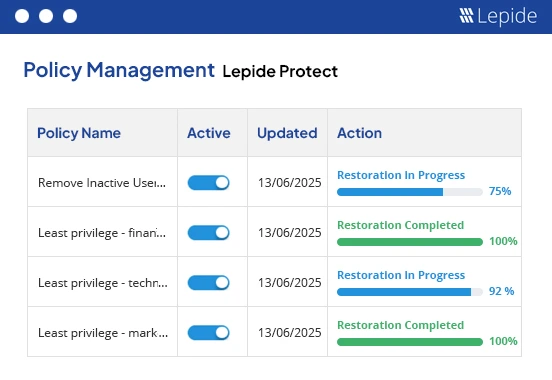
Apart from doing permission analysis, you can also audit changes made to your files and folders in real-time and get detailed audit reports with Lepide File Server Auditor.