Last Updated on August 2, 2022 by Satyendra

In 2017 alone, hundreds of thousands of computers across the globe have been affected by ransomware attacks; draining enterprises of millions of dollars. Those who have been affected all offer the same advice; protect yourself before it happens to you! While you may already be using anti-ransomware software, researchers have identified several new ransomware threats that your security software may not be equipped to fight with (Ovidly Stealer, Hackshit, Satan and Cerber, to name a few). So, what can we learn from the most prominent ransomware attacks of 2017?
Recent ransomware attacks
A couple of ransomware attacks that were prominent recently are WannaCry and Petya (or NotPetya).
The WannaCry ransomware worked by encrypting data and threatening to delete records and files from the infected systems. Not long after the WannaCry fallout, Petya hit the US and European markets. This attack was even graver by some accounts because, unlike its predecessor, it did not have a “kill switch.”
What is the solution? Security experts who have experience in dealing with such cases suggest that, as a first step, organizations should apply security patches to their Windows Operating Systems. Without this, it is just a matter of time before another ransomware attack spreads. Based on these recent attacks, I’ve outlines five practical, actionable tips you can take to stop the spread of similar strains of ransomware from crippling your environment.
Five tips to secure your organization from ransomware attacks
1. Have restoration capability
Even with the most advanced security measures in place, you can never completely defend against ransomware. If malware sneaks through your cyber security, your best bet is to have a stringent backup policy in place so that you can restore data (even if it is corrupted, stolen or is under siege). For more sensitive data, have a secondary backup in place (preferably cloud storage).
2. Monitor data flow
Continuously monitor data flow to see how files and folders move around your network or leave the corporate domain. Though this will not prevent an attack, you will be able to respond to it quicker if you can catch it early.
3. Educate users
Train users about the dangers of phishing attacks. In the past, many breaches have happened through phishing emails. Training on this threat must be a regular occurrence. The more you train users about the possibilities of phishing attempts and the ensuing business losses, the smaller the chance that someone will fall prey to one.
4. Use the latest and best-in-class defense utilities
Purchase the latest antivirus solution that goes beyond signature-based detection techniques to incorporate behavior monitoring. Those who have opted for signature-based detection tools must keep updating their software, as a simple rescan after a software update can mitigate many of the threats.
5. Use multi-factor authentication tools
Many ransomware attacks originated from stolen login credentials. Multi-factor authentication software is a security system that uses more than one type of authentication to establish the users’ identity. Used correctly, it can make it near impossible to break into an administrative account.
Using Lepide Data Security Platform to fight ransomware
You can use Lepide Data Security Platform to instantly audit Active Directory, Group Policy, Exchange Server, Windows File Systems and NetApp Filer configuration changes. The solution will enable you to detect the spread of ransomware attacks in your network via real-time and threshold alerts. Here’s a bit more detail about how Lepide Data Security Platform can specifically help you detect and prevent the spread of ransomware:
Secure Group Policies
Lepide Data Security Platform can help you to track important Group Policy changes; such as software restrictions and password policies changes. It can send both real-time and threshold-based alerts when important changes are detected, and allows you to restore the entire Group Policy Object in just a few clicks.
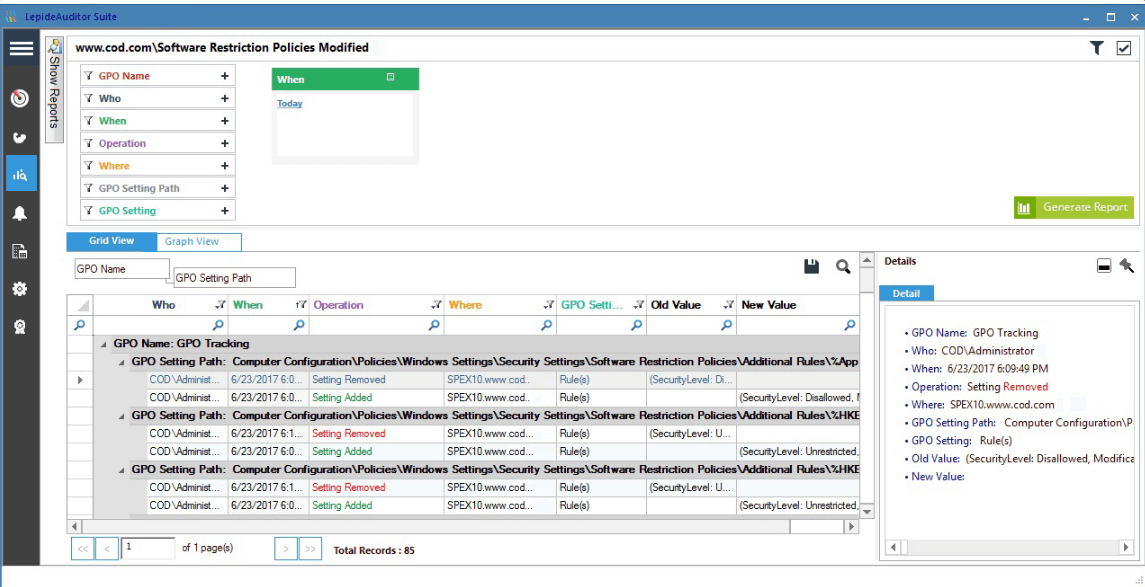 Figure 1: Group policy changes
Figure 1: Group policy changes
Spot unusual changes instantly
Ransomware attacks usually cause suspicious changes, particularly to files and folders. If such changes go undetected, then you’re too late to do anything about it. For example, in the recent WannaCry attack in May of 2017, ransomware encrypted critical files and altered their extensions with a new suffix; causing them to be hidden and encrypted. It scans your entire network for such suspicious changes and sends you real-time alerts. The following image shows the file renamed report of Lepide Data Security Platform, which will allow you to detect such changes.
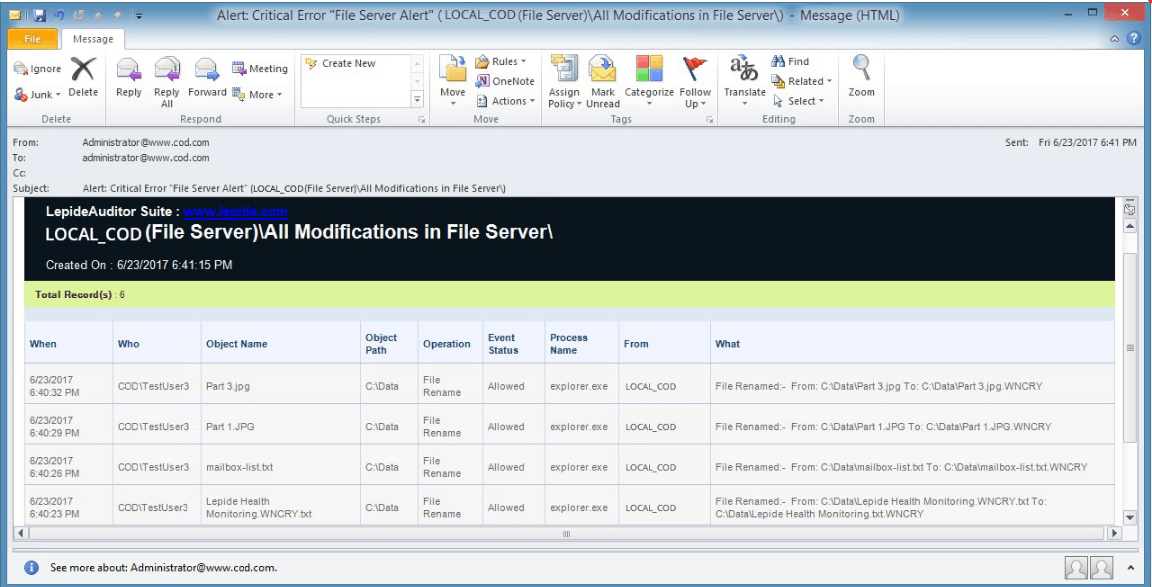 Figure 2: Real-time alerts for important changes
Figure 2: Real-time alerts for important changes
Ability to restore unwanted changes
Once you’ve detected the ransomware attack, the next target should be to have the ability to restore the unwanted IT configuration changes. With Lepide Data Security Platform, you can capture both Active Directory Objects and Group Policy Objects’ state snapshots. Use Lepide Object Restore Wizard to restore the objects’ state to a previously dated snapshot.
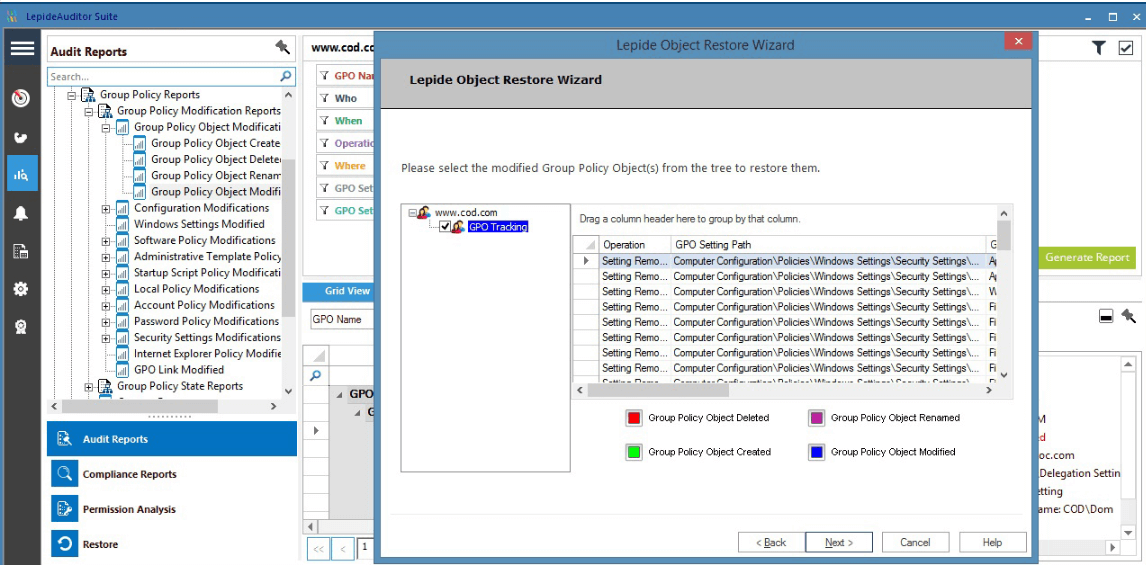 Figure 3: Lepide Object Restore Wizard
Figure 3: Lepide Object Restore Wizard
If you’re one of the many organizations that are looking into ransomware protection options after the WannaCry and Petya attacks, then the best place to start is by strengthening your network.
If your security measures already include plans for fighting off ransomware attacks, then you must do a risk exposure analysis, strengthen defense measures, enhance detection capabilities and do some additional threat modelling. Cloud security is another option that you can consider.
If you use Active Directory, Group Policy, Exchange, File Server or NetApp Filers, then you can start with Lepide Data Security Platform.

