



















































As environments grow more complex, answering even simple security questions can require multiple reports, filters, and manual investigation. Lepide AI removes that friction. It enables security and IT teams to query their directory and data environment in plain language — surfacing structured, contextual answers in seconds so that you can move from visibility to insight.
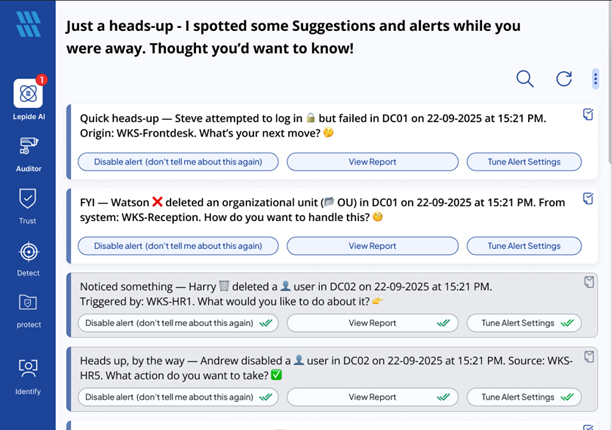
Lepide AI transforms security alerts and audit events into clear, contextual insight — helping you quickly identify misconfigurations, over-privileged access, and risky behavior before they turn into incidents. Lepide AI eliminates alert fatigue, allowing you to focus on the alerts that matter most to the security of your identities and data.
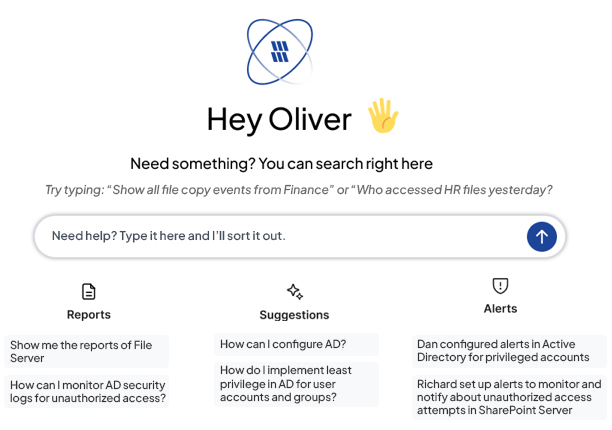
Use natural language searches to query your audit data directory. Lepide AI returns structured, contextual answers – helping you surface relevant activity, changes, and access events – without manually building reports or navigating complex dashboards. Your team becomes more efficient, and more effective.
A guided tour of the Lepide Data Security Platform, your ultimate solution for robust and proactive data and identity protection.
View recording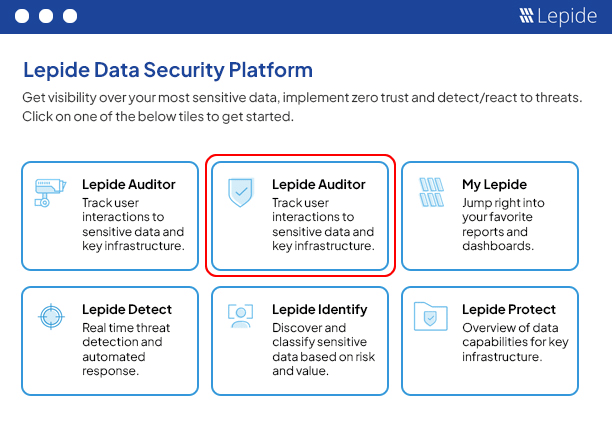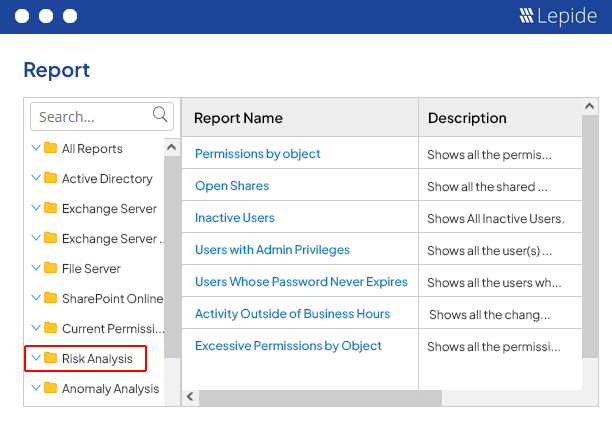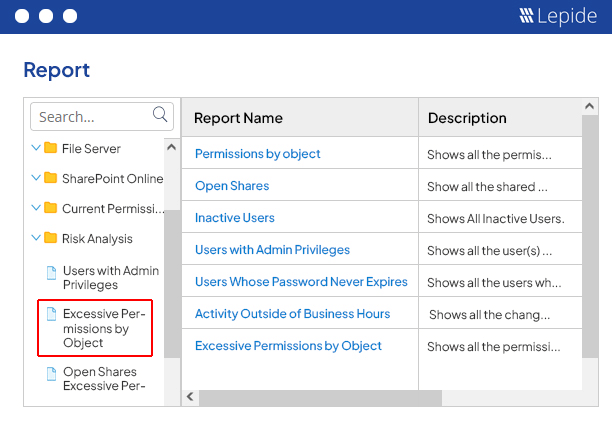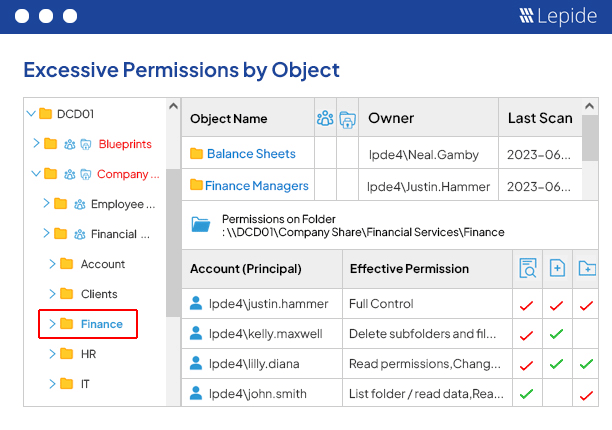
Reduce your threat surface by identifying over-exposed data, spotting misconfigurations, and auditing changes with
Lepide Auditor 🠂 Access GovernanceSee who has access to sensitive data, spot users with excessive permissions and govern access to data with
Lepide Trust 🠂 Threat DetectionDetect and react to threats with AI-led anomaly detection, alerts, threat models, and automated threat response with
Lepide Detect 🠂