Data Access Governance Software
Continuously discover, review, and control access to sensitive data across cloud and on-prem, before it becomes a breach or an audit failure.














Billions of records are exposed every year, not by advanced exploits, but by attackers abusing excessive access. Access sprawl has become one of the most overlooked and dangerous security gaps.
Most users have more access than they need, and no one’s watching. Permissions pile up quietly as roles change and projects shift, leaving over-permissioned accounts that attackers can easily exploit.
Sensitive data gets created, shared, and forgotten with no oversight. The result? Orphaned files and open folders scattered across your environment, waiting to be misused.
Stolen passwords keep working because access rarely gets reviewed. Legacy access models fail to keep pace, letting attackers use valid credentials long after they should’ve been revoked.
Lepide enables you to identify where your sensitive data is, see who has access to it, how access is being granted, spot users with excessive permissions, and monitor user behavior – all from one simple, scalable, and affordable Data Security Platform.
Lepide’s discovery process adds valuable context to the raw, scattered permission data provided by native tools like Microsoft’s ACLs:
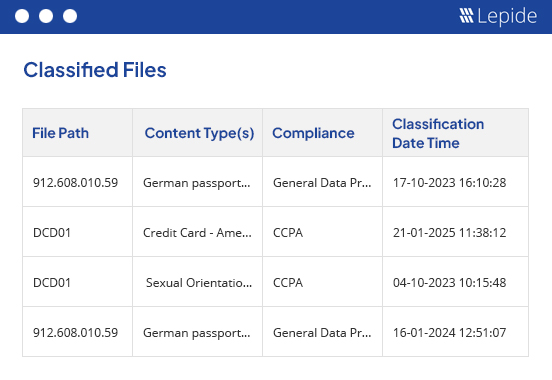
Lepide gives you full visibility into who has access to what and how that access is granted.
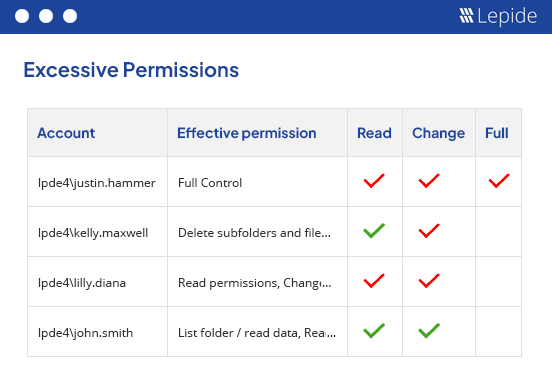
Lepide helps you detect and remediate over-permissioned users with automation, visibility, and control:
Access governance doesn’t end with remediation. Lepide continuously tracks changes to permissions, file access, group memberships, and user activity across your environment.
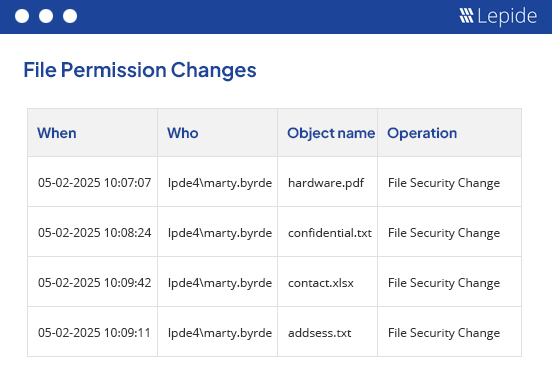
Managing permissions manually across thousands of files is time-consuming and error prone. Lepide helps IT and security teams quickly identify excessive access, automate remediation, and detect risky behavior in real time, all from a single dashboard.
Get rid of the stress of preparing for detailed compliance audits. Lepide gives compliance teams instant visibility into who has access to what, tracks all access changes, and generates detailed reports to meet GDPR, HIPAA, SOX, ISO, and more.
With sensitive data spread across on-premises and cloud platforms, getting the required level of visibility that regulated industries need can be difficult. Lepide helps protect PHI, PII, student data, and other forms of regulated data by enforcing least privilege, monitoring access, and simplifying compliance.

Impressive Varonis Competitor At A Fraction Of The Cost.
The product is very impressive, captures all the information as advertised and performs well. The implementation engineer assigned to our account was knowledgeable and readily available.
Global Security Manager, USAIn this webinar, we’ll demystify the principle of least privilege and demonstrate how to implement it effectively to protect your sensitive data.
View recording
Identity governance focuses on managing user identities and roles, while data access governance zeroes in on what those identities can access. Think of identity governance as setting the rules, and access governance as enforcing them at the data level. Both are essential, but data access governance often gets overlooked, and that’s usually where breaches begin.
Best practice is to run access reviews quarterly, but high-risk departments or sensitive data stores may need monthly reviews. With Lepide, you can automate the remediation of excessive permissions, and schedule regular reports to help you increase the frequency of reviews whilst keeping them time and cost effective.
Yes. While multiple users may access the same data, Lepide helps you identify the most permissioned and possibly responsible individuals, typically the ones with full control or modification rights. Instead of assuming ownership based on usage, Lepide analyzes permission structures to flag users who are most likely accountable for managing that data. From there, you can assign responsibility, initiate access reviews, and reduce the risk of orphaned or exposed data.
Lepide tracks permission changes over time and alerts you when access begins to exceed normal boundaries. It also flags stale or unused permissions, so you can safely revoke them. This is a core part of effective data access governance, helping fast-growing companies prevent temporary access from becoming a permanent risk.