Secure PII and Pass Strict Government Compliance Audits
Lepide empowers Government agencies to achieve robust cybersecurity and regulatory compliance through simplified data security solutions.















Pre-set reports and alerts tailored specifically to meet compliance, including FISMA, NIST, CJIS and more.
Monitor and alert on all user behavior relating to sensitive data to ensure you can detect and prevent data breaches.
A complete audit trail of all changes being made help spot and prevent inappropriate interaction with data.
Lepide offers a tailored solution to address the unique data security challenges faced by US government agencies. With Lepide, agencies gain enhanced visibility, actionable insights, and accelerated incident response capabilities. By safeguarding sensitive data and meeting regulatory obligations, government entities can bolster national security, protect citizen privacy, and optimize operational efficiencies. We ensure that data security is cost-effective and straightforward, delivering measurable ROI and enduring value to federal stakeholders.
Lepide learns what normal user behavior looks like and will generate alerts in real time when it detects anomalies. Our Al-backed anomaly spotting removes false positives to ensure accurate threat detection. Whenever users are interacting with financial data, or any other type of sensitive information, you’ll know about it.
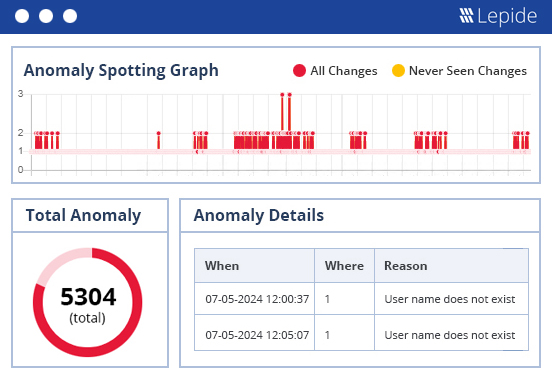
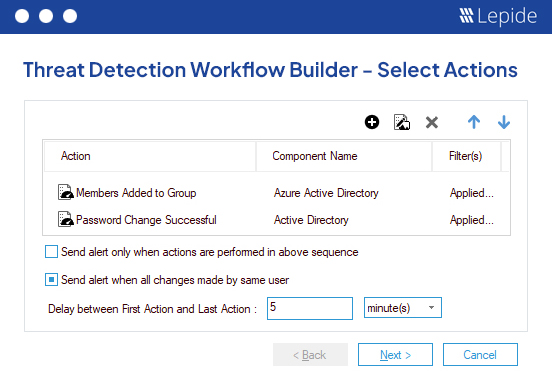
Ensure you can spot threats to regulated data in real time, including ransomware and unauthorized data access, with always-on threat detection workflows and real time alerting. Automate your threat response to detect threats to mitigate risks and maintain compliance.
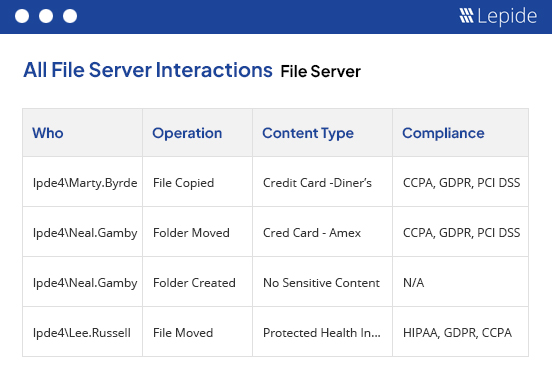
Within seconds, produce compliance-ready reports to satisfy detailed audit requirements. Demonstrate the effectiveness of your security policies and practices in order to meet FISMA, GDPR, CCPS, and align with the NIST CSF.
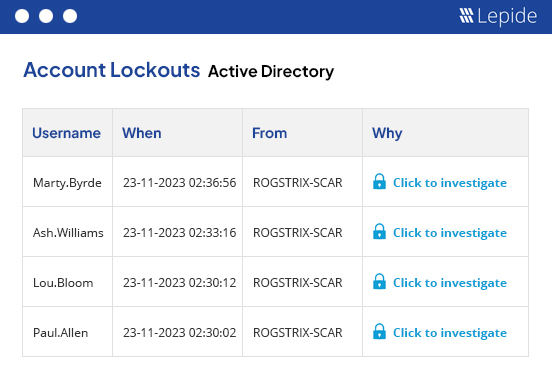
Easily and quickly troubleshoot common IT problems, including account lockouts, restoring deleted objects, and more. By streamlining these tasks, you empower your IT team to spend more time on what matters most; protecting your sensitive data.

“Lepide is a perfect fit for our needs. It helps us cut out a lot of wasted time. But chiefly, we know we can be compliant with industry standards, and that we have a good handle on data security.”

A guided tour of the Lepide Data Security Platform, your ultimate solution for robust and proactive data and identity protection.
View recording