Protect PHI and Meet Compliance
Ensure that you are safeguarding sensitive personal health information and patient data against misuse and meeting HIPAA compliance through advanced user behavior analytics and visibility.














Strengthen your data security posture and get peace of mind that you can comfortably detect and response to security threats.
Pre-defined, customizable reports, and real time alerts, give you the information you need to make quick, informed decisions in the event of security incidents.
Remove stress, save money, and recover your time by simplifying compliance audits. Get the reports you need to satisfy HIPAA, CCPA, GDPR, and more.
Lepide empowers healthcare organizations in the UK to achieve operational efficiency and regulatory compliance through simplified data and identity security. By safeguarding sensitive data and maintaining compliance with regulatory frameworks, healthcare providers can enhance patient trust, mitigate reputational risks, and focus on delivering high-quality care.
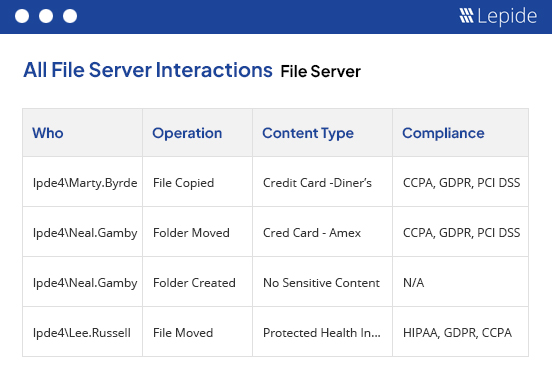
Lepide learns what normal user behavior looks like and will generate alerts in real time when it detects anomalies. Our Al-backed anomaly spotting removes false positives to ensure accurate threat detection. Whenever users are interacting with financial data, or any other type of sensitive information, you’ll know about it.
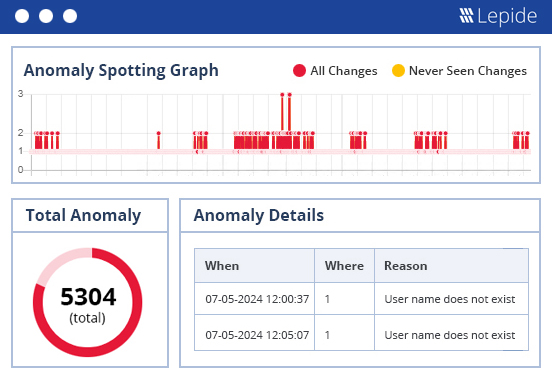
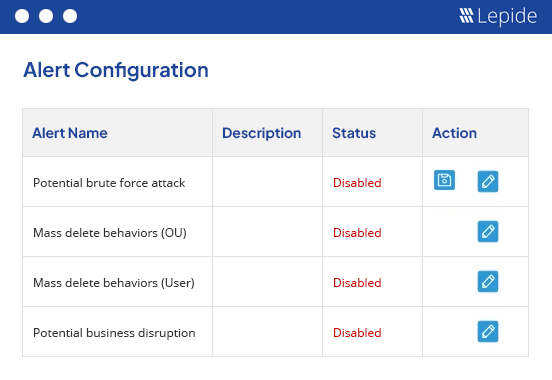
Ensure you can spot threats to PHI in real time, including ransomware and unauthorized data access, with always-on threat detection workflows and real time alerting. Automate your threat response to detect threats to mitigate risks and maintain compliance.
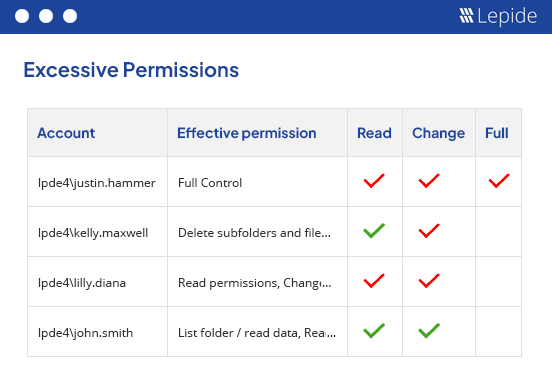
Analyze the permissions structure of your organization and see exactly how users are getting permissions to access PHI. Use in-built AI to identify users with excessive permissions and revoke them. Spot changes to permissions that could lead to unwanted access to sensitive data or a larger threat surface.
Within seconds, produce compliance-ready reports to satisfy detailed audit requirements. Demonstrate the effectiveness of your security policies and practices in order to meet HIPAA, GDPR, SOX, PCI DSS, FISMA and more.

“Lepide is straightforward to use and effective right off the bat. Plus, the level of patience, attentiveness and technical knowhow is far beyond most support and sales teams I’ve seen before.”

A guided tour of the Lepide Data Security Platform, your ultimate solution for robust and proactive data and identity protection.
View recording