Prevent the Misuse of Financial Services Data
Protect your sensitive financial data from insider threats and external attacks through advanced user behavior analytics and visibility into critical changes.














Strengthen your data security posture and get peace of mind that you can comfortably detect and respond to security threats.
Pre-defined, customizable reports, and real time alerts, give you the information you need to make quick, informed decisions in the event of security incidents.
Remove stress, save money, and recover your time by simplifying compliance audits. Get the reports you need to satisfy PCI DSS, GLBA, SOX, and more.
Lepide empowers financial institutions to achieve operational excellence and regulatory compliance through simplified data security identity. Our intuitive platform streamlines security operations, reducing complexity and resource requirements. By safeguarding sensitive data and maintaining compliance with regulatory frameworks, financial institutions can bolster trust, mitigate reputational risks, and focus on innovation and growth in a competitive marketplace.
Reduce the time it takes to produce the detailed reports required to satisfy compliance auditors. Our completely customizable reports are quick to generate, easy-to-understand and enable you to focus on the data that matters the most to your organization.
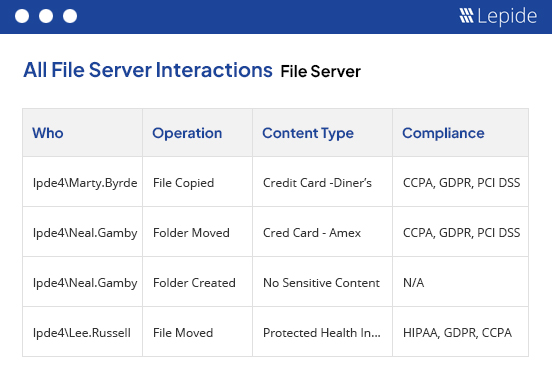
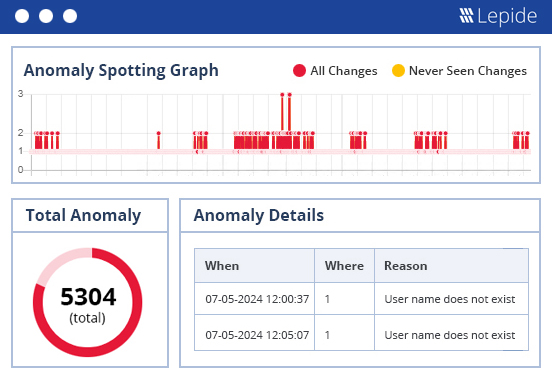
Lepide learns what normal user behavior looks like and will generate alerts in real time when it detects anomalies. Our Al-backed anomaly spotting removes false positives to ensure accurate threat detection. Whenever users are interacting with financial data, or any other type of sensitive information, you’ll know about it.
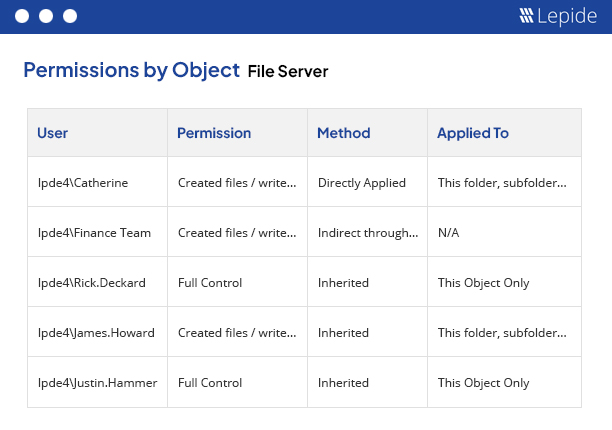
Analyze the permissions structure of your organization and see exactly how users are getting permissions to sensitive data, including through nested groups. Using our AI-powered permissions management tools, easily identify users with excessive permissions and revoke them. Spot changes to permissions that could lead to unwanted access to sensitive data or a larger threat surface.
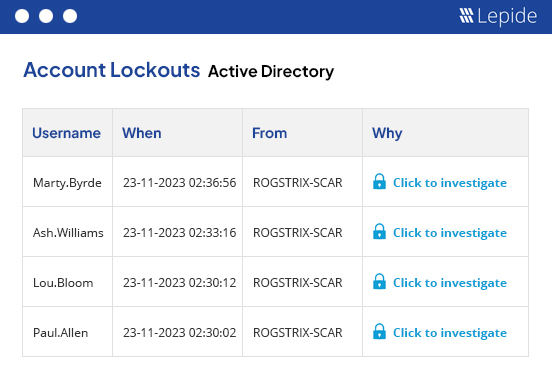
Easily and quickly troubleshoot common IT problems, including account lockouts, restoring deleted objects, and more. By streamlining these tasks, you empower your IT team to spend more time on what matters most; protecting your sensitive data.

“Lepide saved money and time. Their sales rep answered my questions quickly and our examiners really like the solution. The solution itself is really easy to use, manage and configure for our requirements. I’d give it a solid 9/10.”
A guided tour of the Lepide Data Security Platform, your ultimate solution for robust and proactive data and identity protection.
View recording