Last Updated on September 29, 2022 by Akhilesh Shivhare

Security teams across the globe are grappling with a seemingly insurmountable problem, and that is, people make mistakes! We all have moments of weakness, and we all have the potential of being manipulated by malicious actors.
And yes!
Even those who are responsible for maintaining the security of our critical systems, will sometimes fall victim to a social engineering scam.
With this in mind, it’s hardly surprising that cyber-criminals seek to exploit our naivety in order to trick us into handing over money, or sensitive information which they can use to further their agenda.
While it is true that we all make mistakes, we also wise up to the various tricks and scams that come our way.
To compensate, social engineering attack vectors are becoming increasingly more sophisticated, as well as more threatening.
It’s a game of cat and mouse, and we must always endeavour to stay ahead of the curve to make sure that we can quickly identify social engineering attempts, as and when they arise.
What is Social Engineering?
The purpose of social engineering is to trick unsuspecting victims into handing over sensitive data or violating security protocols to allow the attacker to gain access to sensitive data, through other means.
Naturally, our employees are our first line of defence, yet they also tend to be the weakest link. And all it takes is one moment of weakness, which might involve downloading an email attachment or clicking on a link to an unknown website, to wreak havoc on our systems and data.
Earlier social engineering attempts were fairly primitive, and typically involved sending the same email to many recipients, however, these days, they are becoming increasingly more targeted, and the attackers are willing to put in a lot of time and effort into gaining the trust of their victims.
For example, they might add the victim on Facebook, like and comment on their posts, send the occasional message, and then, after some time, convince them to hand over sensitive data, and sometimes even their bank details.
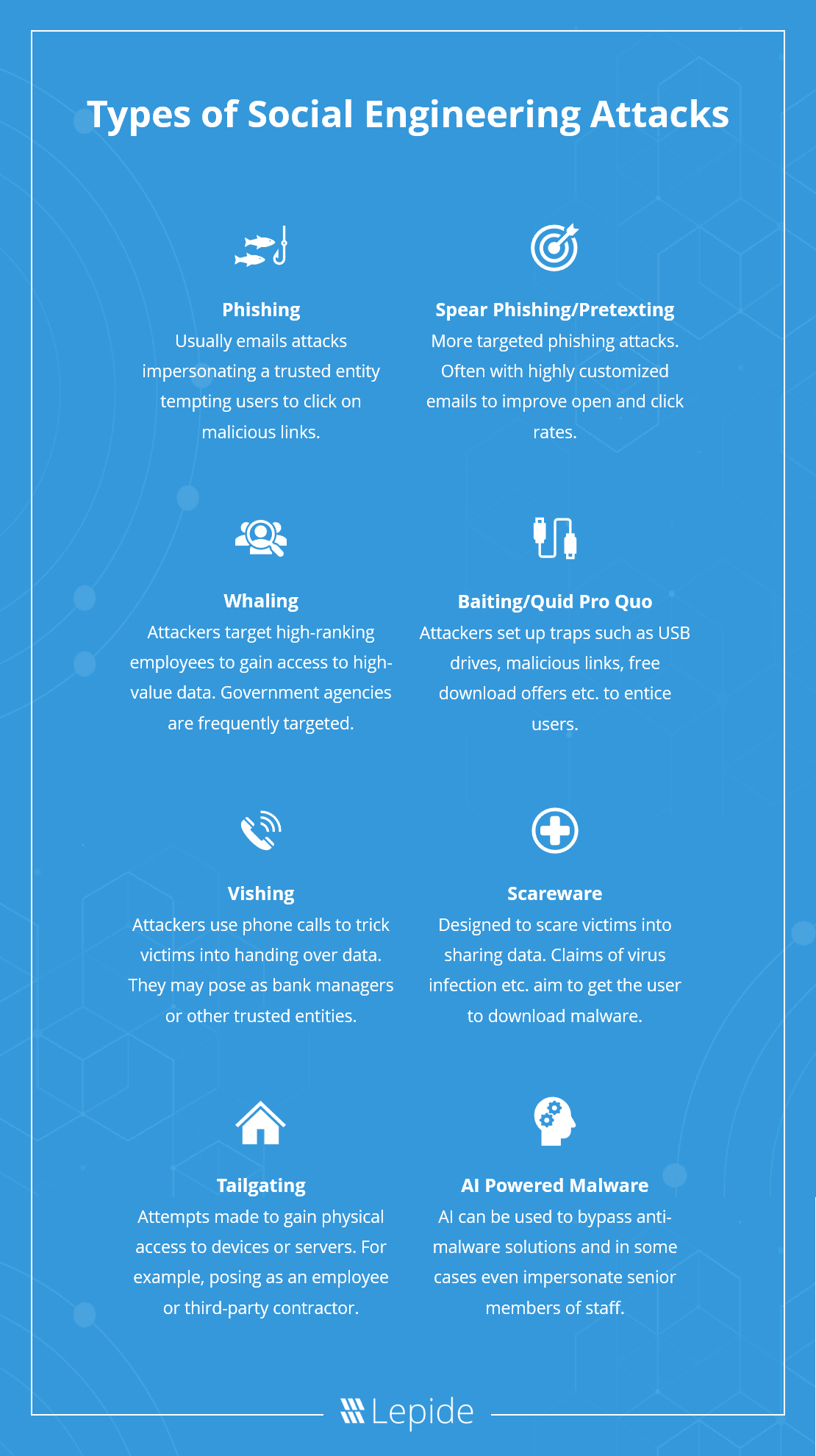 A summary of the types of social engineering attacks
A summary of the types of social engineering attacks
Types of Social Engineering Attacks
There are a variety of different techniques that attackers will use to trick employees and individuals into handing over valuable information, although the differences between them can be subtle. Below are the most commonly used terms to describe these different methods.
Phishing
Phishing is the most common type of social engineering attack and is usually delivered in the form of an email. However, attackers may also use social media, SMS, or some other media. The attacker will impersonate a trusted entity, such as a work colleague, bank or reputed organization, in an attempt to trick the victim into clicking on a malicious link or downloading an email attachment containing malware.
Spear-phishing & pretexting
Traditionally, attackers would compile a large list of potential targets, and send each one a “copy and paste” email, in the hope that one would bite. However, as users became savvier, and spam filters became more sophisticated, the attacks had to evolve and become more targeted. Such attacks are commonly referred to as “spear-phishing”.
The attacker may choose to target a specific employee within an organization – especially newer employees as they’re easier to trick, or they may broaden their horizons and focus on all employees within that organization.
Given that their primary motive is likely to be financial gain, they will often target financial departments. Of course, spear-phishing requires a lot more time and effort to execute, compared to traditional phishing techniques.
After all, the attacker will need to find out as much as they can about the target. They will also need to customize their emails to make them seem more legitimate. Another term you might come across is “pretexting”.
However, pretexting is really just another word that describes the act of deceiving the victim into handing over-privileged data.
Whaling
Whaling, as you might be able to guess, is where the attacker targets high-ranking employees within an organization. These might be CEOs, CFOs or other senior executives, and the goal is to gain access to high-value data. Attackers will also target Government agencies, in an attempt to obtain classified information.
Baiting and quid pro quo
Baiting, as the name suggests, is where the attacker sets up traps in order to entice victims into handing over credentials or installing a malicious program. The “bait” can be either a physical object, such as a USB drive, or a link to a malicious website/application, which offers free movie downloads or some other service that users might be interested in.
Another term that is often used is “quid pro quo” – a Latin phrase that means an exchange of goods or services. It is actually very similar to baiting, in that, the attacker will offer something to the victim, in exchange for their data.
Of course, the victim is unaware that the attacker is trying to cheat them out of their data. An example of a “quid pro quo” attack is where an attacker poses as a legitimate technical support engineer, who offers to help the victim with a real problem.
The attacker will ask the user for their login credentials, or other valuable data. Alternatively, they may provide the user with a “free” security update, which they claim will solve their problem. Instead, the program will infect their computer with malware.
Vishing
Vishing is where the attacker uses phone calls to trick the victim into handing over valuable data. The attacker will setup a fake phone number, and call the victim claiming to be their bank, or some other trusted entity, asking them for their account details.
Scareware
Scareware, as you might expect, is designed to scare victims into handing over sensitive information. It often presents itself in the form of a pop-up, informing the victim that they have been infected with a virus, and they need to install their software to fix the problem. Of course, the software they install with be malware.
Tailgating
Tailgating, also referred to as “piggybacking”, is a technique used by the attacker to gain physical access to an employee’s device, or the company’s server. The attacker may gain access to the physical premises by pretending to be an employee, claiming they have lost their ID card, or a similar excuse. Naturally, tailgating is more effective in organizations where there are large number of employees.
AI-Powered Malware
AI and social engineering are not an obvious combination. However, attackers are starting to realize that AI can be used to bypass even the most sophisticated anti-malware solutions, and even impersonate the voices of senior executives.
Some AI-powered malware is able to insert itself into existing emails and use machine learning algorithms to mimic both the tone and topic of the conversation. AI can be used to identify users who are more susceptible to phishing scams, and a whole lot more.
It is a likely that “smart phishing”, as it is becoming known, will be major headache for IT teams and anti-malware software vendors in the years to come.
Tips to Prevent Social Engineering Attacks
Social engineering may be impossible to complete prevent, but as it relies in part to the gullibility of your users, there are things you can do to protect yourself.
Mainly, you should educate your users to slow down and not hastily react to messages. Scammers will send out phishing emails that seem like their urgent follow-up require. Take stock, and don’t let this influence you.
You should be sure to research where an email comes from if it looks dodgy. Make sure the company is real and the senders email address is legitimate.
Instead of clicking on links in the email or opening attachments, try and use search engines to get to the page directed by the email.
Never reply to emails that request financial information or passwords. Ensure that all your spam filters are set to the strictest possible settings and secure your computing devices.


