



























Lepide delivers the industry's most effective and affordable data security and governance solution - simple to implement, but powerful in protection. Unlike other vendors, our AI-driven audit reports, permissions analysis, and real-time threat remediation provides enterprise-grade security - without the enterprise price. Trusted by over 1,000 companies worldwide, Lepide combines cutting-edge technology with intuitive usability, keeping you ahead of risks and regulations with ease.
Learn more →


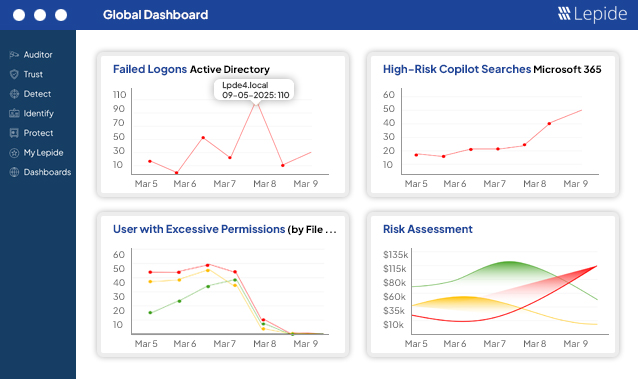
Combining unstructured data and Active Directory security across on-premises and cloud environments allows Lepide to address major security use cases. Take a look at some common ways our customers are using Lepide in our interactive demonstration.

Get a complete list of your admin users in Active Directory in a clean and easy report.
Download free tool
Quickly scan your Active Directory environment to spot disabled, locked, and inactive users.
Download free tool
Understand how much of your data is stale and how many open shares there are on each File Server.
Download free tool
Our competitors make solving the problem very expensive. We don’t. There are also no hidden costs and no need for pro services.

Our solution is simple to deploy and fast to get up and running. If you have a problem to solve right now, we’ll solve it fast.

We win on functionality. Our reports are the easiest to use and the most flexible, and our alerts are actually delivered in real-time.

Lepide’s AI engine continuously learns from user behavior to respond to threats, eliminate excessive privilege, and enforce zero trust at scale.