Data Access Governance solution.
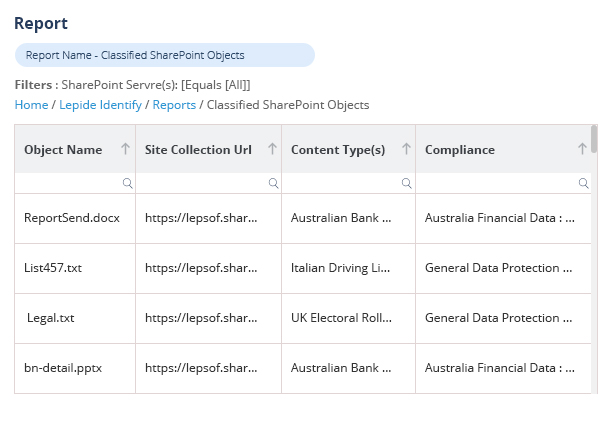
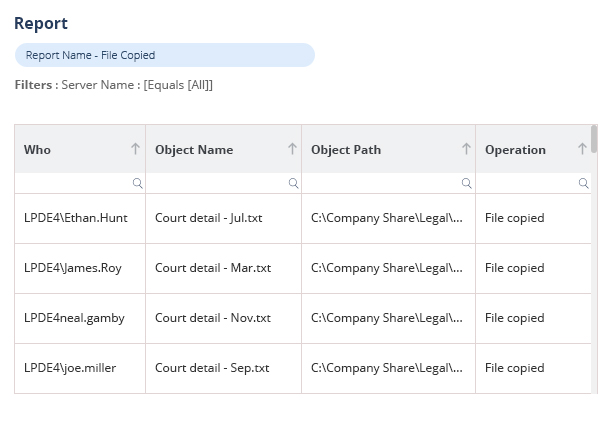
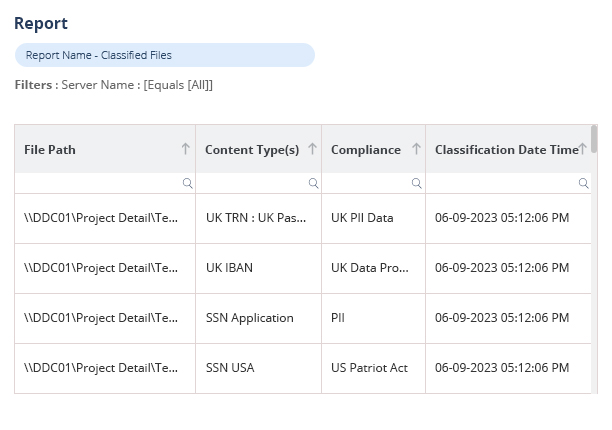
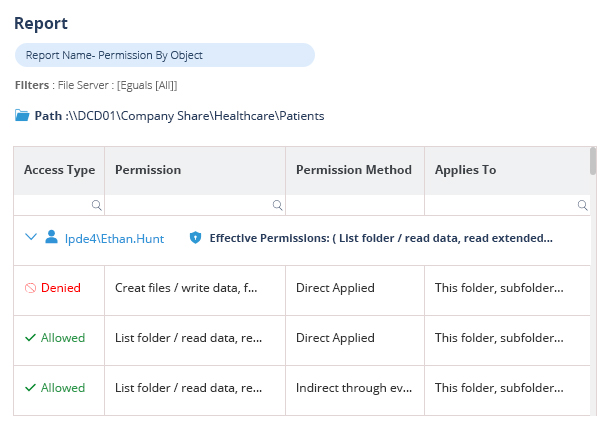
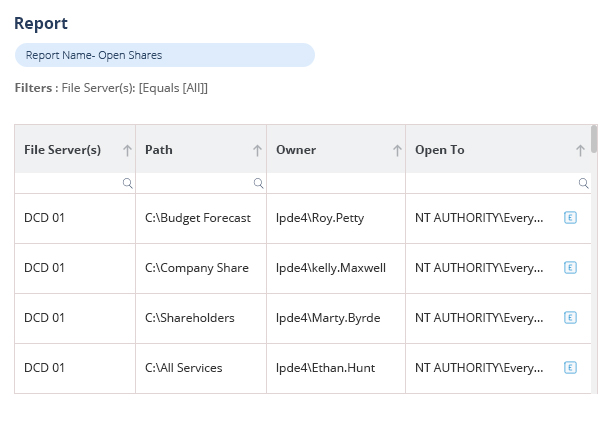
The modern attack surface is expanding every day as employees join, leave, and move roles within the business. This often causes access rights to sprawl out of control, leading to increased risk. Our Data Access Governance software enables you to identify where your sensitive data is, see who has access to it, how access is being granted, spot users with excessive permissions, and monitor user behavior.
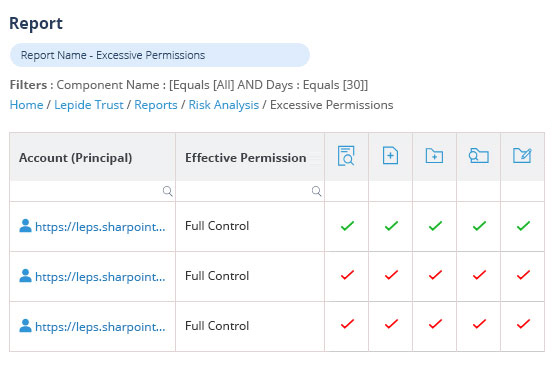
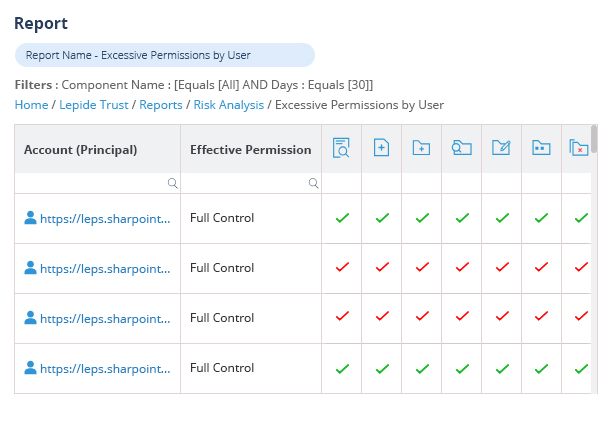
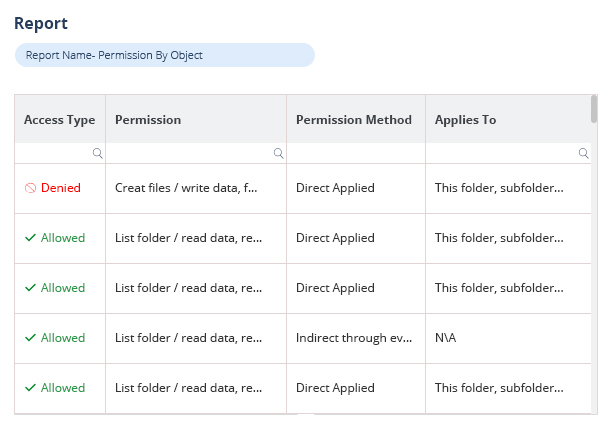
Spot and remediate excessive permissions.
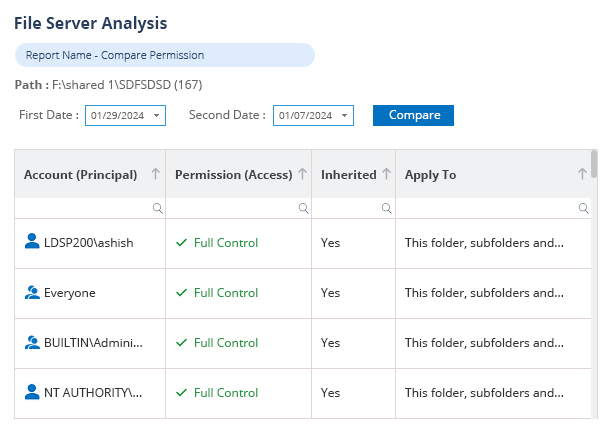
When permission changes are made that could lead to unauthorized or unnecessary access to sensitive data, your potential attack surface and risk of data breaches increases. With Lepide, you can spot these permission changes and reverse the change from within the solution itself.
Lepide also automatically detects users with excessive permissions to help you speed up and streamline remediation.
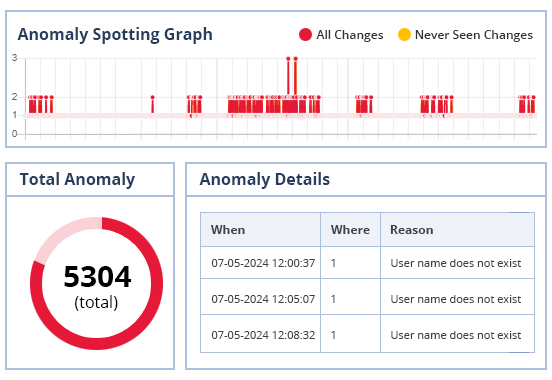
Get visibility over anomalous user behavior.
With our intelligent anomaly spotting you can detect and react to user behavior that may be putting you at risk of security breaches. Lepide can detect single point anomalies and enables you to action automated threat response templates to help shut down threats before they cause irreparable damage.