


























The Lepide Data Security Platform gives you full visibility and control across Active Directory, Entra ID, file servers, and Microsoft 365 — all from one console. Detect risks, respond to threats, and prove compliance in minutes.
Don’t stay in the dark. Get complete visibility over what’s happening in your directories and to your data. Every event and change across your environment is pulled into simple, powerful reports that are customizable, filterable, searchable, and sortable – with the critical who, what, when, and where information.
Explore auditing →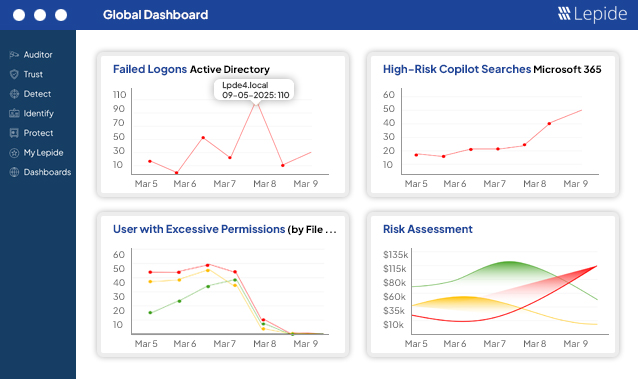
Always-on AI learns user behavior and generates real time alerts when threats are detected. Pre-defined threat models and workflows enable you to detect the symptoms of threats in real time and trigger automated responses to maintain the security and integrity of your sensitive data.
See how the threat detection works →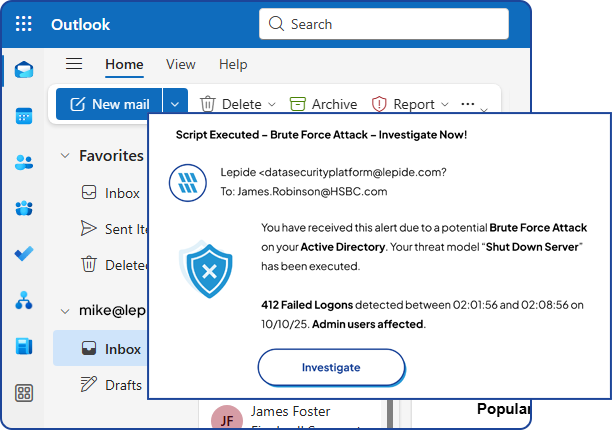
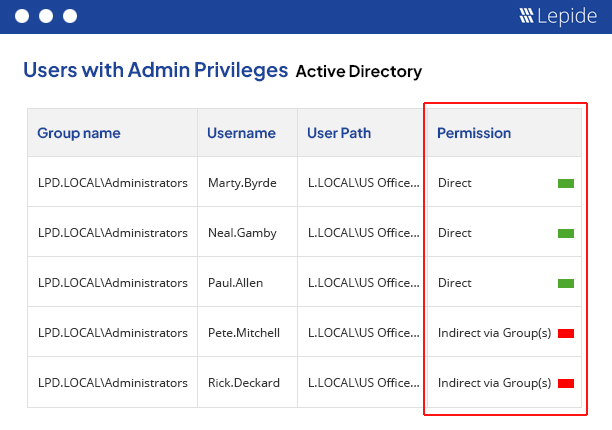
Excessive permissions are a leading cause of data breaches. With Lepide, you can spot when permissions are no longer required and automatically revoke them using custom policies applied on files and folders. Take the guesswork out of zero trust.
See how Lepide is changing permissions management →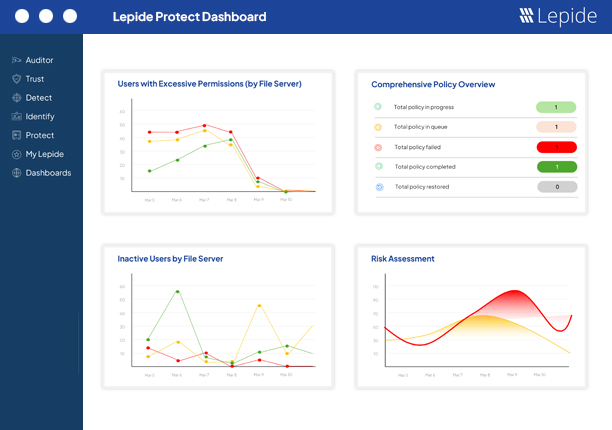
Simplify access governance with instant visibility over your current permissions and permission changes. Spot excessive access, determine real effective permissions, and make sure that permissions don’t spiral out of control.
Explore our permissions functionality →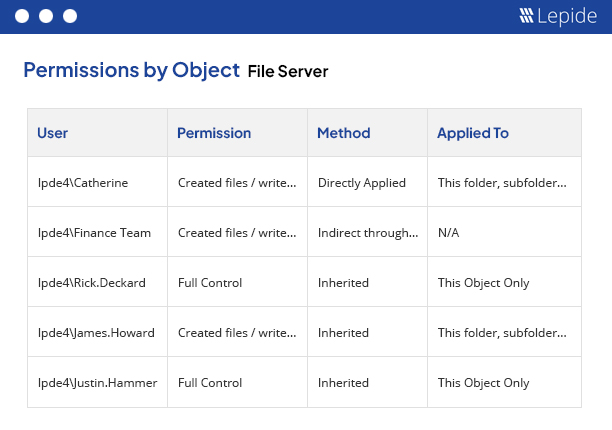
Discover and classify sensitive data at the point of creation across your on-prem and cloud data stores. Persistent data classification helps to add meaningful context to your data security efforts – helping you focus on what matters most.
See how data classification adds context →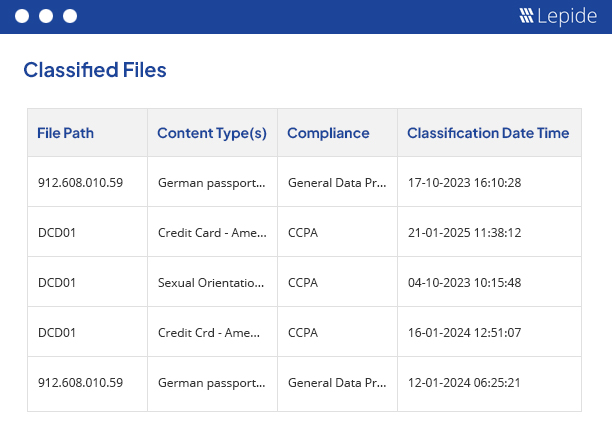
Lepide replaces multiple point solutions for auditing, permissions, and data governance — helping you cut costs, simplify operations, and stay ahead of threats.
See the unified platform in action.
I have used Lepide for a long time and have always been happy with the product. The last time we did a penetration test, the vendor was very annoyed because the way I have Lepide configured caught a lot of things most people miss. Senior IT Admin/Cyber Security specialist/Azure Architect Manufacturing, 250M-500M USD
 Drayke Jackson
Security Engineer
Drayke Jackson
Security Engineer

“Lepide is straightforward to use and effective right off the bat. Plus, the level of patience, attentiveness and technical knowhow is far beyond most support and sales teams I’ve seen before.”
 Kevin Gallagher Systems Administrator
Kevin Gallagher Systems Administrator
“Lepide gave as almost instant insight into changes into our AD environment. For auditing Group Policy, its reports are hands down the most intuitive.”
 Agnel Dsilva IT Administrator
Agnel Dsilva IT Administrator
We chose Lepide as they were able to offer us threat detection and response, and a way of separating out reporting duties to a web console – all from one platform.”
 Johnnie Ferguson Network Administrator
Johnnie Ferguson Network Administrator
Lepide saved money and time. Their sales rep answered my questions quickly, and our examiners really like the solution. The solution itself is really easy to use, manage, and configure for our requirements. ”
 Ricardo Lopez Director of Compliance
Ricardo Lopez Director of Compliance
Lepide allowed us to capture forensic-level data without requiring high-volume storage or additional systems. Auditing began on day one. Immediate value. ”
Lepide can detect all manner of threats to your sensitive data, including insider threats, ransomware, permissions sprawl, compromised user accounts, and more. Lepide monitors user behavior, highlights anomalies, and provides real-time alerts to help you take preventative action.
Yes, the Lepide Data Security Platform integrates with various SIEM solutions, including Splunk and IBM QRadar, and supports both cloud and on-premises environments. It also works alongside identity management systems and other security tools.
Lepide supports a wide range of platforms, including Active Directory, Azure AD, Office 365, SharePoint, Exchange, SQL Server, and File Servers. It also supports cloud environments like AWS and Google Cloud.
Yes, Lepide offers a 20-day free trial of the Data Security Platform. The best way to evaluate the platform, is to request a personalized demo. Some critical use cases can be explored in an in-browser demo.
Lepide can be deployed quickly in both on-premises and cloud environments. It has flexible deployment options, and the support team provides guidance to ensure a smooth and successful implementation.
The Lepide platform is designed to scale with your organization’s needs. Whether you are a small business or a large enterprise, the platform can be tailored to monitor and protect data across multiple locations and domains.
Lepide provides 24/7 customer support, as well as detailed documentation, tutorials, and best practice guides to ensure users can maximize the value of the Data Security Platform.
The Lepide Data Security Platform is incredibly lightweight. It is a single Windows application that uses SQL to store all of its collected log data and information. There are full scalability options to support even the largest enterprise deployment.
We only use agents where absolutely necessary, mainly to remove gaps in an audit trail that are quite often found in native log sources. Depending on the data sources and systems you want to monitor will determine whether or not you require an agent. For example, for Active Directory, an agent is not required. For Windows File Servers an agent is required but this is purely because native auditing lacks critical information such as when files are copied.
No, admin credentials are not required for the Lepide Data Security Platform. Being a security platform, the solution operates on a least privilege model ensuring our service accounts only require the necessary privileges to operate optimally.