Lepide Auditor
Change Auditing and Reporting Solution
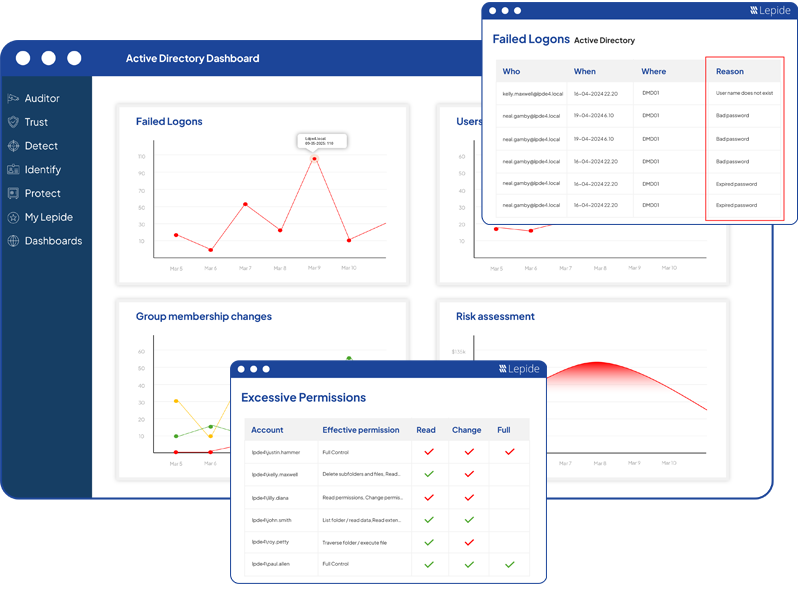
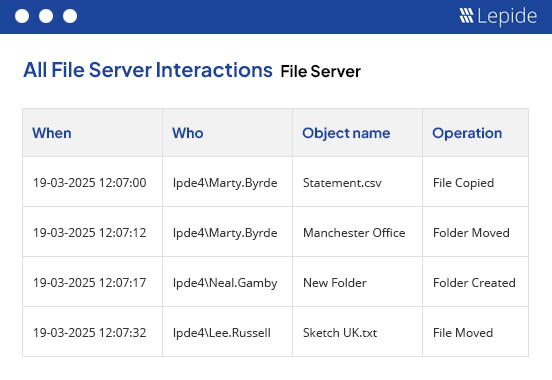
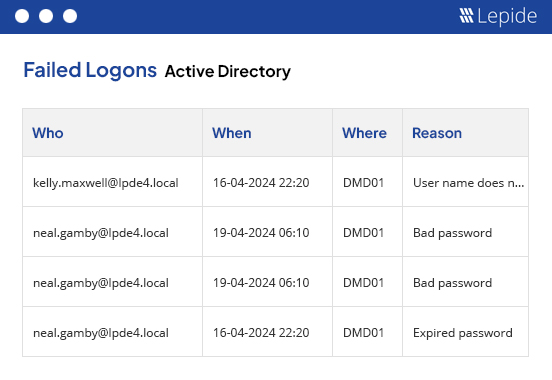
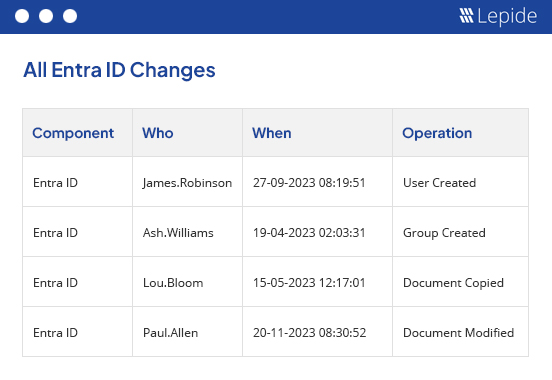
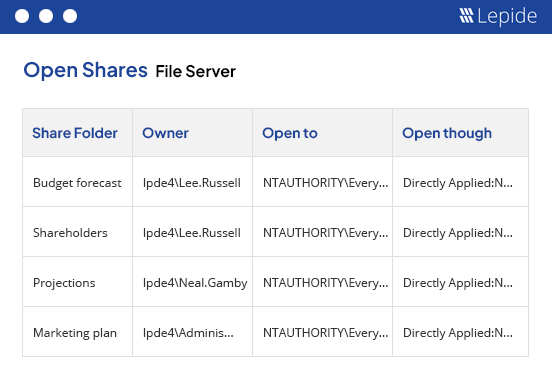
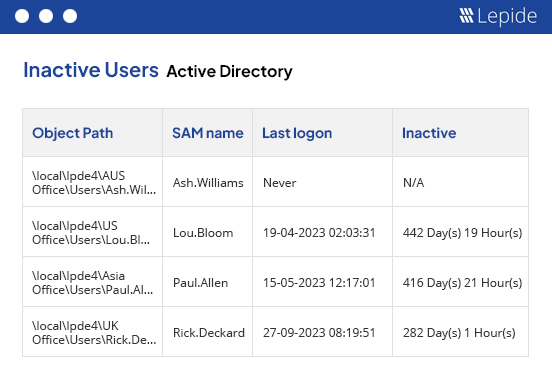
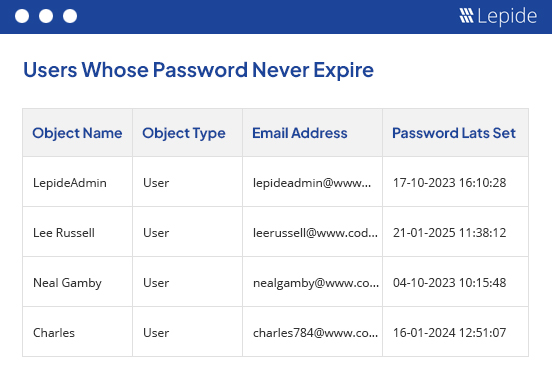
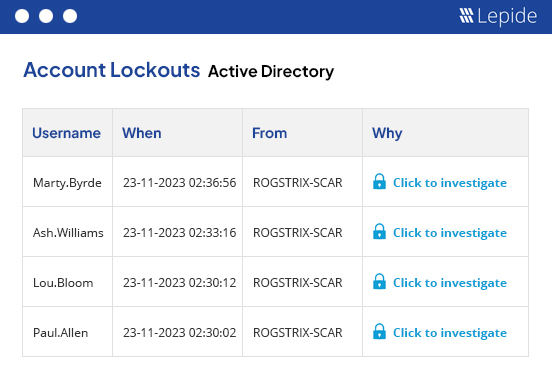
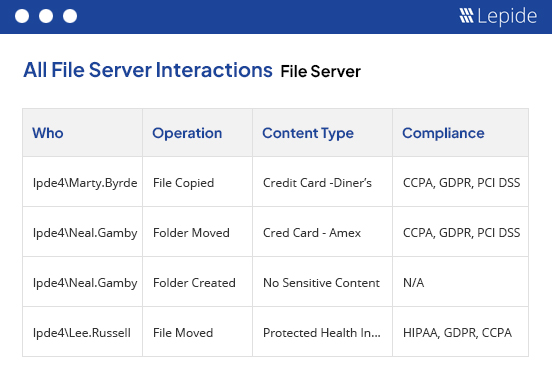
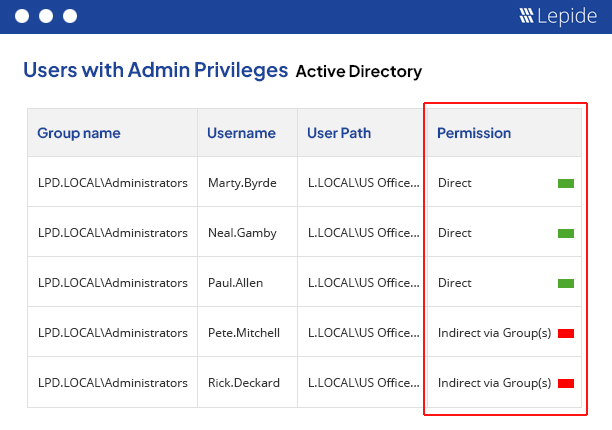
Audit and report on changes taking place to your key systems and data to help reduce your threat surface area, detect threats and meet compliance demands.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x