Analyze Historic Permission Changes with Lepide Data Security Platform
Compare and analyze historic permission changes made to Active Directory, Exchange and File Servers.














Ensuring that your users only have permissions to the data that they need to do their job, and nothing more, is a fundamental part of ensuring a policy of least privilege. To maintain such a policy, you will need to be aware of any unwanted or unauthorized changes taking place to your most critical systems, including Active Directory, File Server and Exchange Server.
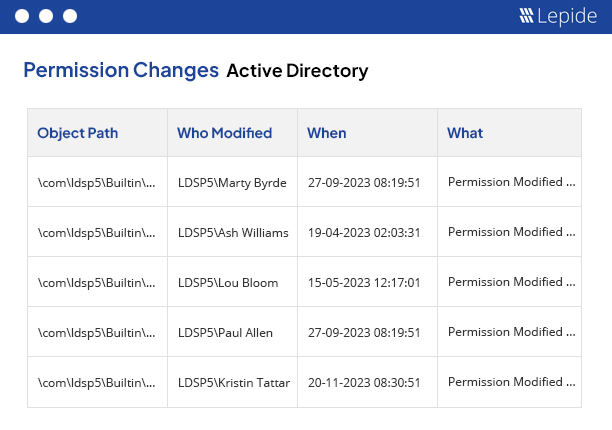
Active Directory permission analysis is a simple way to see what changes have been made in the permissions of your Active Directory objects. It displays historical changes by letting you compare the permissions for selected objects between two specified date and time intervals. These reports can be archived and you can also save separate reports on “Permission History” and “Compare Permission” in PDF, MHT or CSV formats on the disk.
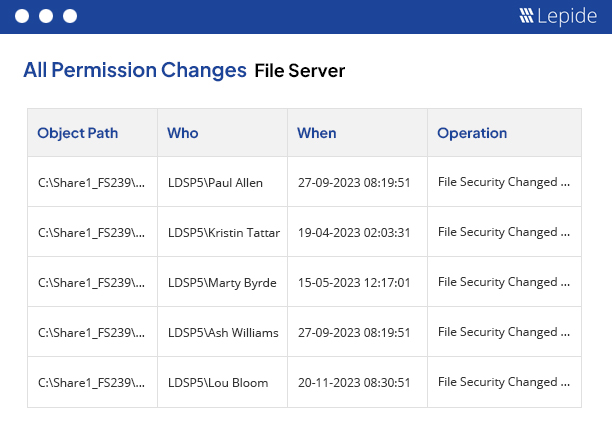
File Server permission analysis is a useful solution to help you keep track of changes made in the permissions of your files and folders. It displays the historical changes in the permissions and also lets you compare the permissions of files and folders between two date and time intervals. These reports can be archived and you can also save separate reports on “Permission History” and “Compare Permission” in PDF, MHT or CSV formats on the disk. It is also able to display whether the current permissions of parent folders are applicable to the respective subfolders and files.
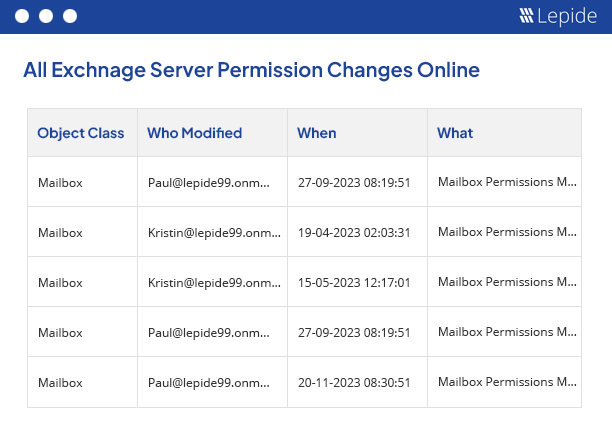
Exchange Server permission analysis displays the historical changes made in the permissions of Exchange Server objects. Our solution allows you to compare the permissions for the selected objects between two date and time intervals. You can also save separate reports on “Permission History” and “Compare Permission” in PDF, MHT or CSV formats on the disk and archive the permission analysis records in their respective databases.
By following the guidelines outlined in this paper, your organization can establish a robust data access governance program that supports its business objectives and protects your valuable data assets.
Get the free guide now!