IT administrators struggle everyday with the challenge of maintaining security in the Active Directory environment. It can often be difficult to find out critical information about who has modified what, where and when in AD user accounts in order to trap malicious users and track unusual activity in their IT environment.
One thing you can do to help mitigate the risks of malicious changes is ensure that you are constantly monitoring and recording any changes taking place in the Active Directory.
Below are the methods to enable Active Directory auditing:
- Enable Auditing by using Group Policy Management Console (GPMC)
- Enable Auditing by using ADSIEdit.msc
Enable Auditing by using Group Policy Management Console (GPMC)
- Configuration of Group Policy Audit Settings
- The Group Policy Management Console
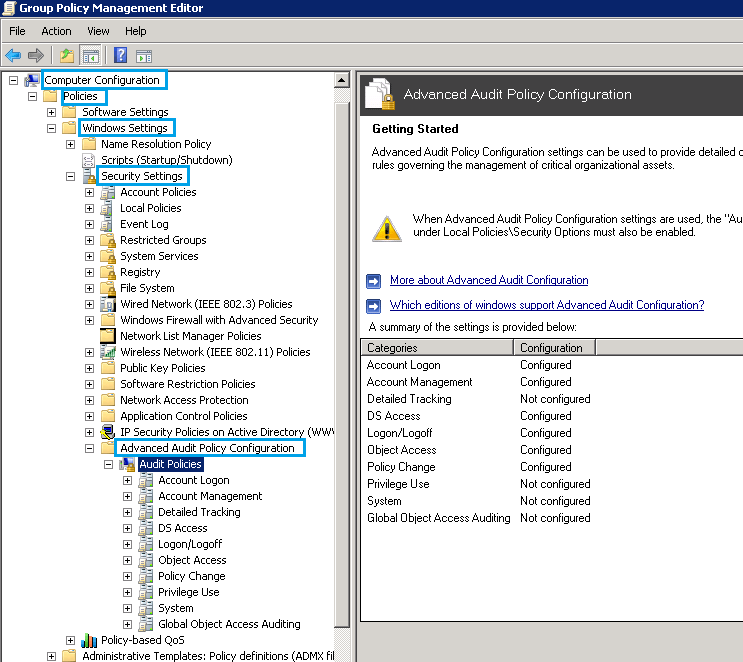
- Advanced Audit Policy Configuration
- Configuring All the Policies
In order to configure all the policies, define the following categories and then configure them one after another:
- Account Logon
- Account Management
- DS Access
- Logon/Logoff
- Object Access
- Policy Change
- Configuring All Policies One by One
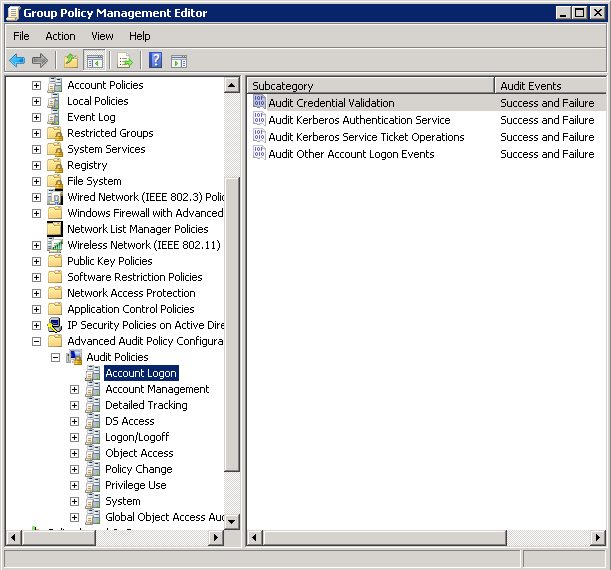
- Check Both Success and Failure
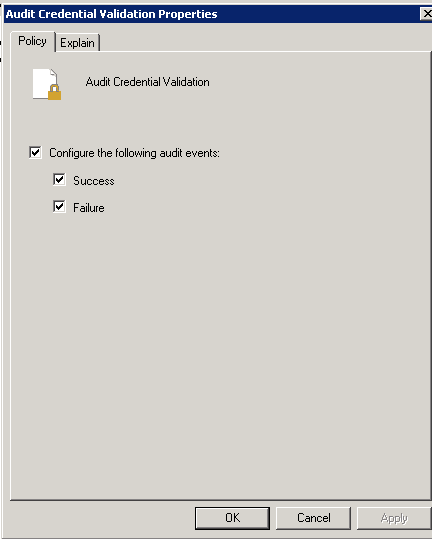
Follow the step 6 for all other Advanced Audit Policies listed above.
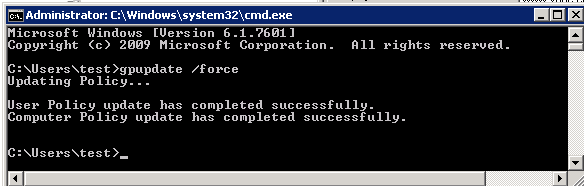
- Updating the Group Policy
Enable Auditing by using ADSIEdit.msc
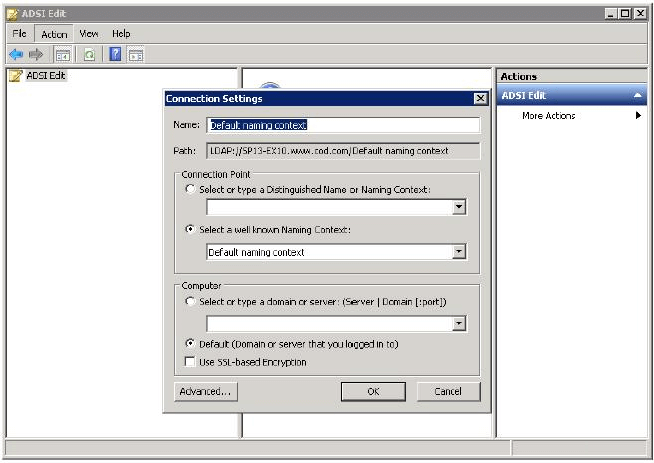
- Open ADSI Edit Console and select “Connect to” in order to view the Connection Settings.
- Next, establish connections with all four available naming contexts to turn on their auditing for:
- Default Naming Context
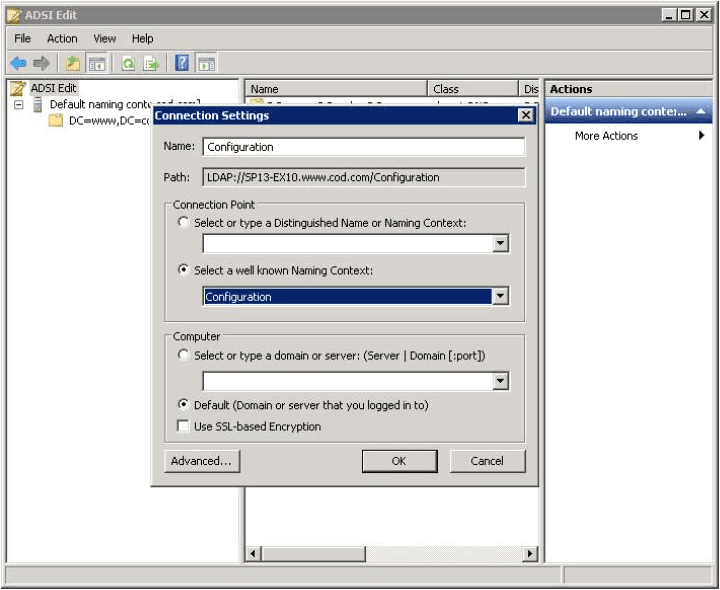
- Configuration
- RootDSE
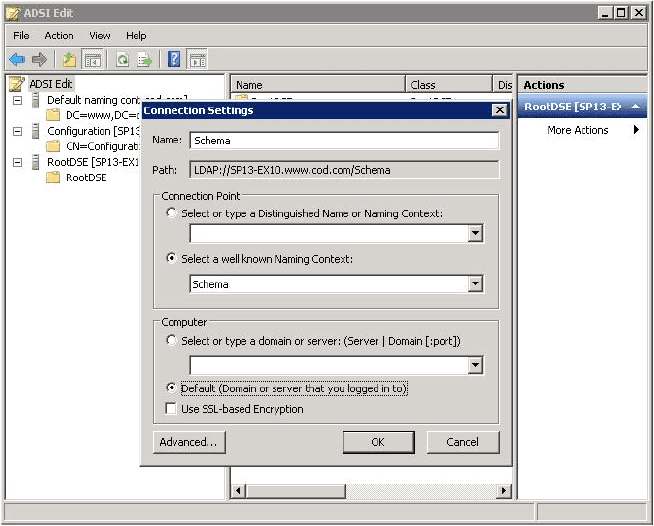
- Schema
Configuring Default Naming Context
Configuring Connection Settings
Establishing connection with Root DSE
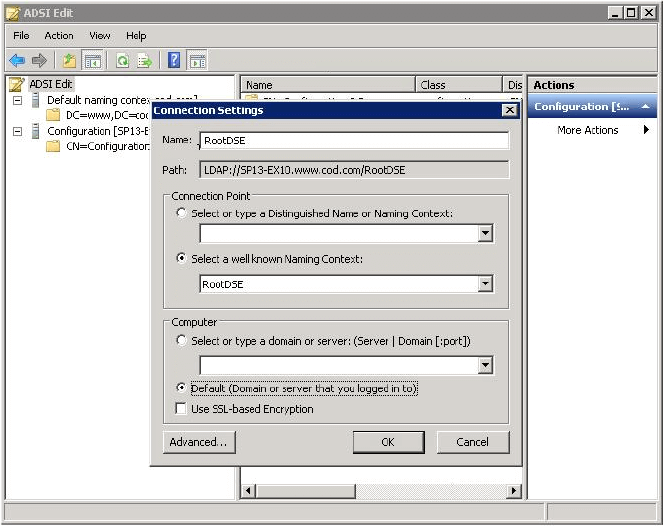
Connection Settings for Schema
- Enabling the Audit Settings for All the Four Root Nodes
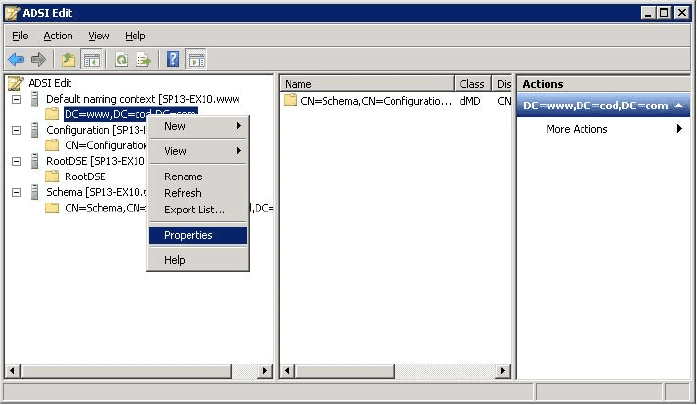
- Managing Auditing Entry for Your Domain
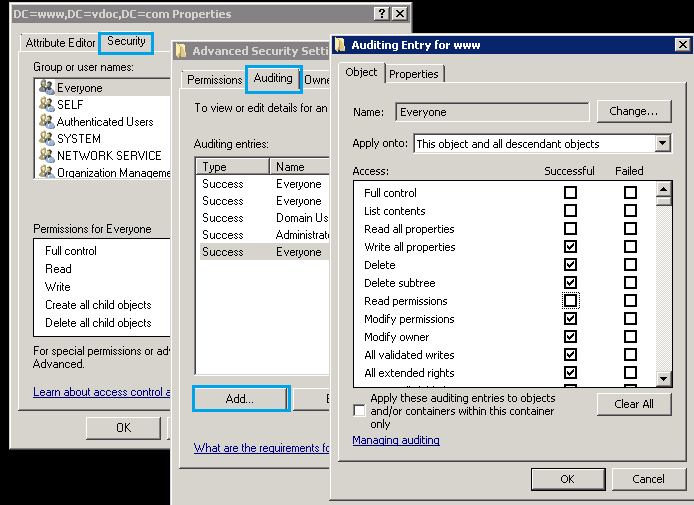
In the Domain Controller properties, navigate to the security tab and click Advanced. This will open the Advanced Security Settings. Now, quickly navigate to the Auditing tab and click Add to open the Auditing Entry window. In the field “Name”- type “Everyone” and in the “Access” section, check all the boxes except the following four options:
- Full Control
- List contents
- Read all properties
- Read permissions
Track Changes Using Event IDs
View audit logs in event viewer to track AD changes by searching relevant event ids
- Filtering the Security Event Log
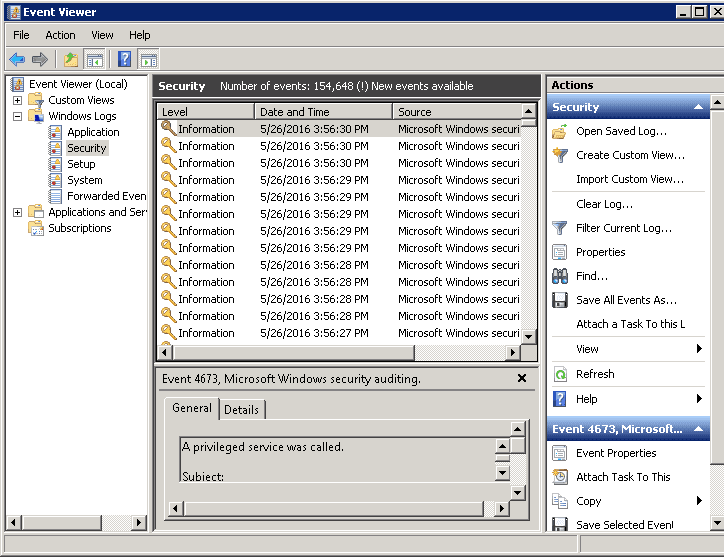
In the Event Viewer, navigate to Windows Logs and select Security. Then, simply click Filter Current Log.
- Search by Event ID
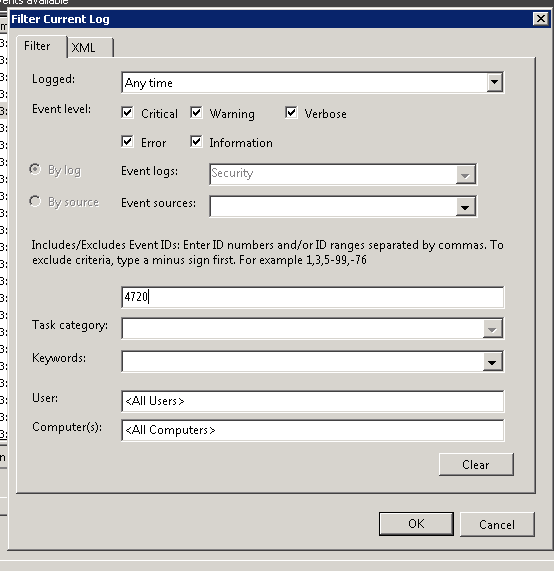
In the “Filter Current Log” window, simply enter the particular Event ID and carry out the search operation. In above image event id 4720 refers to ‘User Account Creation’. have
- Open Event Properties to See Further Details
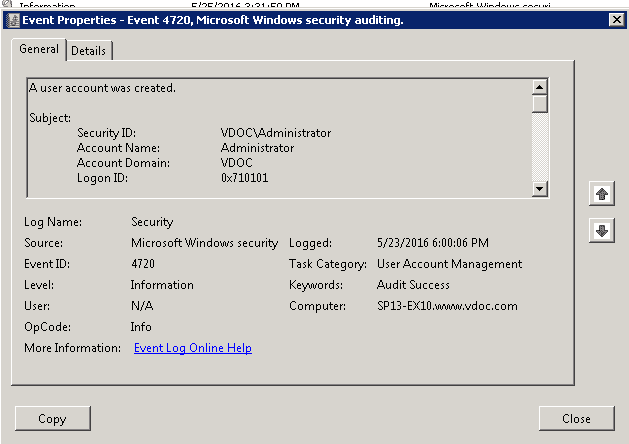
To know more about any particular event, simply double click on it to see further details.
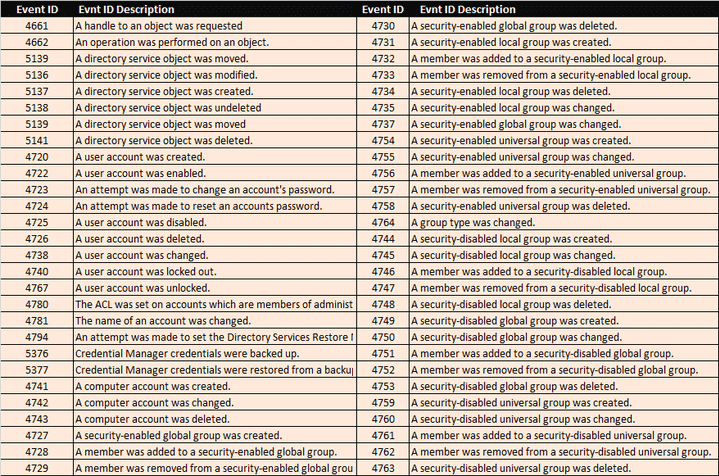
List of Other Relevant Event IDs
How Lepide Active Directory Auditor Tracks Changes Made in AD
For many users, manual auditing can be both time consuming and unreliable, as you have to search lots of audit logs in event viewer, it does not generate instant alerts and reports for Active Directory changes.
It is therefore recommended that you opt for an automated Active Directory auditing solution. One such solution, Lepide Active Directory Auditor (part of Lepide Data Security Platform), that enables users to pro-actively track, alert and report on changes being made to Active Directory.
Lepide’s Active Directory audit solution for records the details of every change made in the configuration of Active Directory and generates 90 reports in three different categories – Active Directory Modification Reports, Active Directory Security Reports, and Active Directory State Reports.
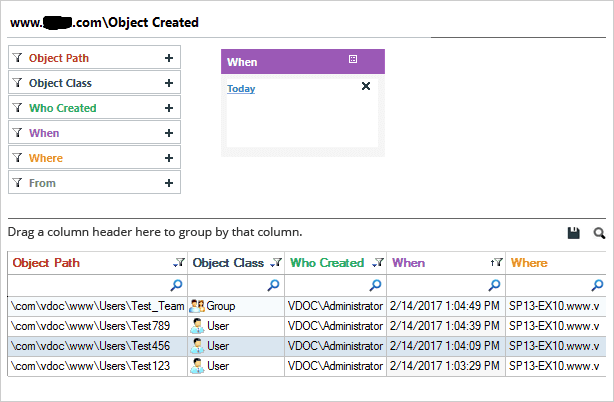
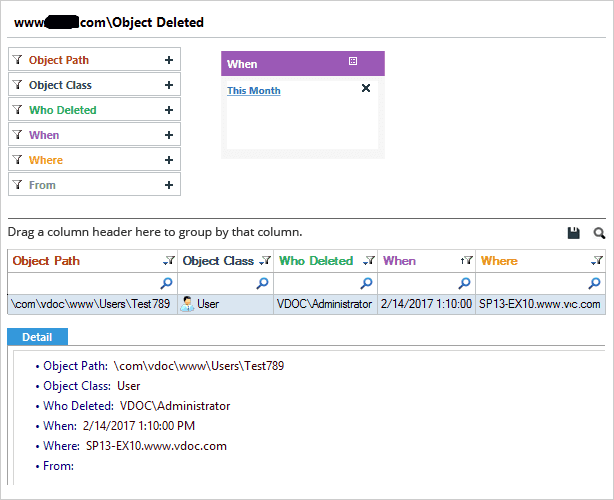
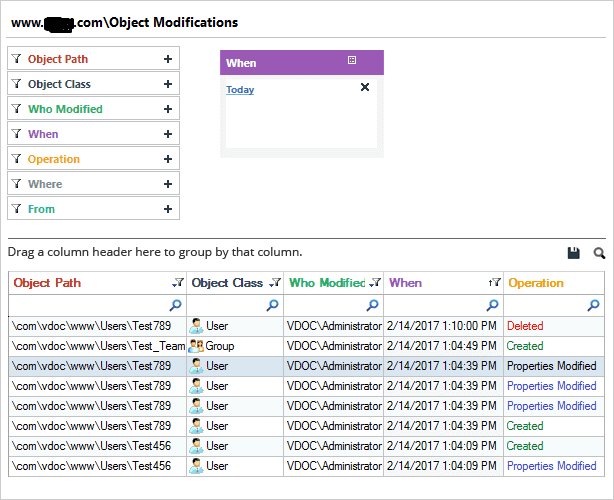
Below are some screenshots that show how our Active Directory auditing solution helps IT administrators track changes in Active Directory objects. Three reports are shown below; a report for objects created, objects deleted and objects modified.
- Object Created Report
- Object Deleted Report
- Object Modifications Report
You can also track other activities like successful and failed logon attempts, account lockouts, permissions changes, privilege user activities etc. easily with our solution.
The Final Note
Lepide Active Directory Auditor for can actually make the whole Active Directory auditing process simpler through its intuitive user interface and sending real-time alerts as emails to desired recipients, as updates to LiveFeed widget, and as push-notifications to Lepide Mobile App to ensure the security of your Active Directory environment.