In the Active Directory, privileged accounts have controlling rights and permissions, and they can do all the designated tasks in the Active Directory, on domain controllers, and on client computers. On the flip side, privileged account abuse can result in data breaches, downtime, failed compliance audits, and other worse situations. In this article, the process of tracking activities of privileged user accounts through native method is explained. Towards the end of the article, an easier way of tracking Active Directory is also added.
Steps to Track Privileged Users’ Activities with Native Auditing
Step 1 – Identify the privileged user accounts
Following users, groups and accounts are considered as Privileged Accounts.
- Members of administrative groups. If a group is a member of any administrative group, then all members of this group will also be Privileged Users.
- Users/Groups who have received administrative privileges through their Organizational Unit.
- Local user accounts and service accounts that may have received administrative privileges locally on domain controllers.
- Users who have privileges to reset passwords and unlock accounts of other users.
- Users who can access Service Accounts having administrative privileges.
- Users who have write access to Group Policy Objects related to domain controllers.
- Users who have access to any application that manages Active Directory.
- Users who are administrator of Virtual System Environment.
Majorly, you can use “Active Directory Users and Computers”, “Group Policy Management Console”, and any virtualization application to list all privileged users. You may also have to run customized scripts to find out other privileged user accounts.
For example, you can browse any Administrative Group to view its members. All of them are privileged users.
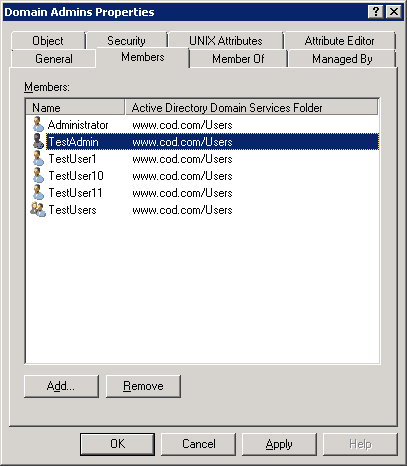
Here, all members (including users and groups) are privileged accounts. As “TestUser” is also a member of “DomainAdmins” group, so all members of “TestUser” are also privileged users.
Step 2: Configuring the required audit policies
Follow the below steps to set up the necessary audit policies:
-
- Go to “Start” ➔ “Administrative Tools” ➔ “Group Policy Management”.
- Go to “Forest” ➔ “Domains” ➔ domain name ➔ “Domain Controllers”. Here, you have to edit default or other group policy object created at domain controller level.
- Right-click on “Default Domain Controllers Policy” or another policy, click “Edit”.
- “Group Policy Management Editor” window opens up.
- Go to “Computer Configuration” ➔ “Policies” ➔ “Windows Settings” ➔ “Security Settings” ➔ “Local Policies”, and select “Audit Policy”. It lists all of its sub-policies in the right panel, which are listed here in the following table.
Table 1: List of Local Audit Policies
| Local Audit Policies | Additional Configuration | Purpose |
|---|---|---|
| Account logon events | Validating account credential by computer. | |
| Account management | Enable this audit to track account name change, account enabling and disabling, account creation and deletion, account password change, and user group change. | |
| Directory service access | Specify SACL for objects | When someone accesses an Active Directory Service object that has its own system access control list (SACL). |
| Logon events | When someone logs on or off a computer (both manual and network logon). | |
| Object access | Specify SACL for objects with types of access | Access non-AD objects such as files, folders, printers, registry keys and other objects. |
| Policy change | Changes to local security policies, user rights assignments, auditing policies, and trust policies. | |
| Privilege use | When someone exercises a user right. | |
| Process tracking | Process creation, termination, handle duplication, and indirect object access. | |
| System events | System generated events. |
-
- You have to select what all policies you want to enable. It is recommended to enable a policy for both its successful and failure events.
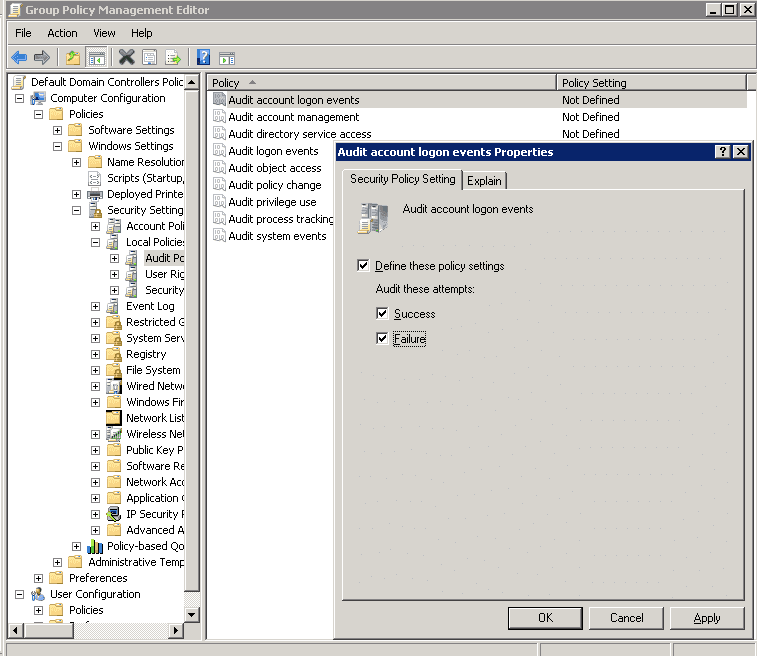
- Repeat the following steps for each policy you want to enable.
- Double-click the necessary policy on the right based on your specific requirement. It displays the policy properties.
- In “Properties” window, click “Define these settings” checkbox.
- Select “Success” or “Failure”, or both.
- Click “Apply” and “OK” to close “Properties” window.
Step 3 – Configuring the advanced audit policy
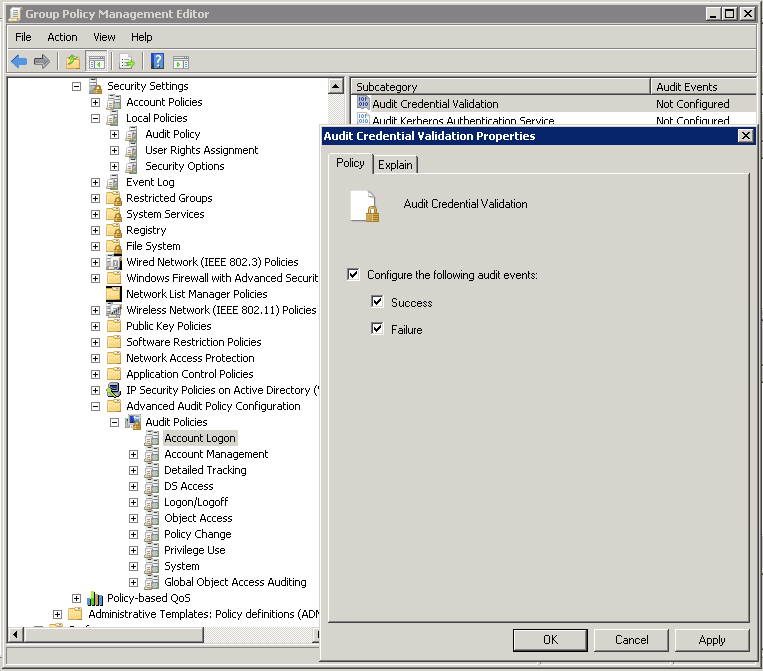
In the same Group Policy Management Editor, go to “Computer Configuration” ➔ “Policies” ➔ “Windows Settings” ➔ “Security Settings” ➔ “Advanced Audit Policy Configuration”. Select “Audit Policies” to list all of its policies in the right panel, which are listed herein below.
Table 2: List of Advanced Audit Policies
| Advanced Security Audit Policies (Categories) | Purpose |
|---|---|
| Account logon | To track domain attempts to authenticate account data, either to a domain controller (DC) or a local Security Accounts Manager (SAM). |
| Account management | To audit changes to user and computer accounts and groups. |
| Detailed tracking | To track activities of applications, how a computer is being used, and the activities of users on that computer. |
| Directory service access | To monitor attempts to access and modify objects in Active Directory Domain Services (AD DS). These audit events are logged only on DCs. |
| Logon/Logoff events | To audit attempts to log on to a computer interactively or over a network. This auditing is very useful for tracking user activity and identifying potential attacks on network resources. |
| Object access | To track attempts to access specific objects or types of objects on a network or computer. |
| Policy change | To audit changes to important security policies on a local system or network. |
| Privilege use | To track privilege use security policy settings and audit events allow you to track the use of certain privileges on one or more systems. |
| System | To monitor system-level changes to a computer that are not included in other categories and that have potential security implications. |
| Global Object Access Auditing | Global Object Access Auditing policy settings allow administrators to define computer system access control lists (SACLs) per object type for either the file system or registry. |
Here, you have to decide what all policies you want to enable. Double-click a policy under any subcategory (listed above). Configure it for both “Success” and “Failure” options.
Step 4 – View events using Windows Event Viewer
After you have enabled the auditing, you can use Event Viewer to see the logs and investigate events. Perform the following steps.
- Go to “Start” ➔ “Administrative Tools” ➔ “Event Viewer”.
- Expand “Windows Logs” and select “Security”. Event Viewer shows you all the events logged in security logs.
- To see events for a specific privileged account, you can either make a search using “Find” option or create a custom view to show the events generated by a particular user only. For our example, we have created a custom view “User Modifications” to see modifications in user accounts made by Privileged Users. Following is a screenshot of deleting a user account by “TestAdmin” – a privileged user.
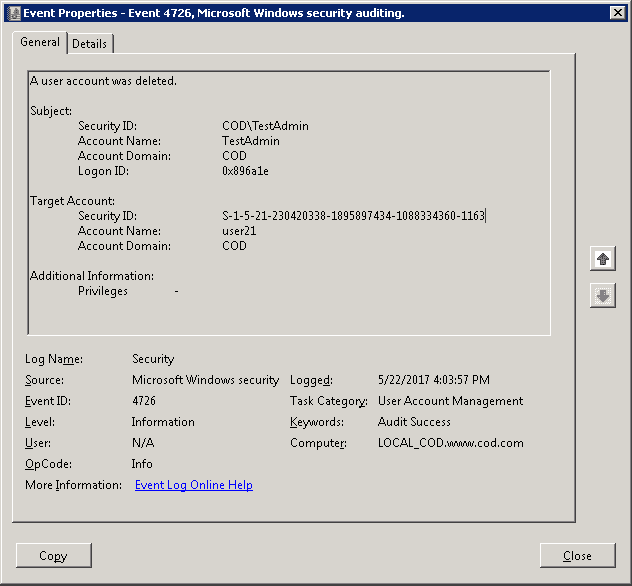
Figure 4: User Account deleted by TestAdmin – a Privileged User
Native methods to audit the domain are complex in nature. There can be more than two events for a particular task like creation or deletion of a user. It increases noise in the audit data and consumes the important time of IT Auditor.
The Administrator may also have to run PowerShell Scripts (downloaded from Internet) to create a handy report. Such reports are more than necessary to track all activities performed by privileged user accounts.
How Lepide Active Directory Auditor Tracks Activities of Privileged Users
Lepide Active Directory Auditor (part of Lepide Data Security Platform) overcomes the drawbacks of native auditing and provides a better way to audit user activities performed in Active Directory.
In the following image, “Object Modification” report has been shown that displays all changes made by “Administrator” (a privileged account).
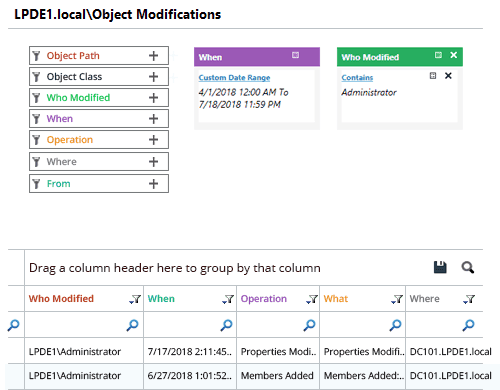
Conclusion
In this article, the native method to monitor privileged users’ activity has been explained. However, sometimes you may find the process as reactive, noisy and not very user-friendly. Therefore, Lepide’s Active Directory audit software can be preferred to audit privilege users easily.