Last Updated on February 23, 2024 by Satyendra
If you’re reading this, you’ve either already become the victim of a ransomware attack or you’re interested in finding out what your options are should it happen to you. So, in this article we’re going to discuss what a ransomware attack does and how best to react to one.
What does a ransomware attack look like?
Ransomware attacks come in many shapes and sizes, but the ultimate goal is to encrypt your data and provide the decryption key at a cost – effectively holding your files and folders at ransom. If your computer is infected, you may see a message like the following:
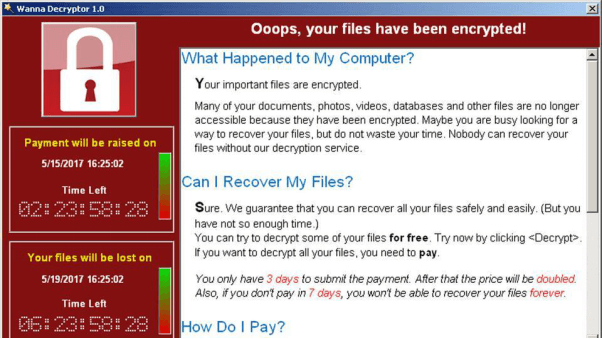
In most cases, decrypting the files yourself is practically impossible. But that doesn’t mean you should pay the ransom. Quite often, paying the ransom won’t lead to recovery of your data at all. In the recent “Petra/NotPetra” ransomware attack, the email address provided to send Bitcoin to was shut down almost immediately. So, what are your options if you encounter a message like this?
If you’ve got back-ups, use them
Firstly, before you do anything else, if you think you’ve become the victim of a ransomware attack you need to disconnect from all wired and wireless networks in order to protect other devices on the networks or any backups you may have.
By far the easiest way to recover from a ransomware attack is to simply restore your files and folders from a backup, assuming you have a recent backup that you have tested to ensure it was unaffected by the attack.
If you have backup software you can use, ensure you go back far enough to a time where you are 100% confident that you were not infected.
What to do if you haven’t got backups
If you’re in this position you may feel like your only option is to pay the ransom. However, as mentioned earlier, do not do this. Many individuals have done this before to no effect. At the end of the day, you’re dealing with criminals so don’t trust anything.
If you’re lucky, there may already be a decryptor available for the particular strand of ransomware you have been infected with. You can check www.nomoreransom.org for a list of established decryptors available.
If this isn’t an option for you, the only one you have left is to completely wipe your device and re-install from scratch.
Protect yourself against future attacks
There are many solutions on the market that help you detect and prevent the spread of ransomware in your systems and enable you to take faster action to mitigate the damages. One such solution is Lepide Data Security Platform.
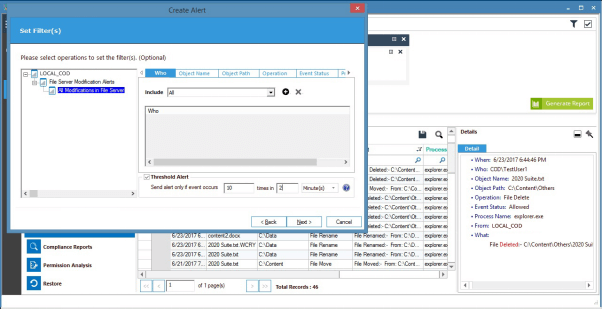
Continuous and pro-active auditing solutions like this allow you to detect when a large number of changes are taking place over a short space of time using threshold alerts, as illustrated in the image below:
Is also allows you to detect whether ransomware is attempting to change permissions to your files, highlights when your sensitive files and folders are being accessed/modified in any way and allows you to reverse AD and GPO changes in a matter of clicks.
If you want to learn more about how Lepide Data Security Platform helps you deal with ransomware, click here.