Why are enterprises still vulnerable despite decades of experience with Active Directory? The answer to this is that many organizations are still grappling with the basics.
According to the State of Active Directory Security in 2026 report from Lepide, companies continue to struggle with properly securing Active Directory (AD).
Admins face ongoing challenges with stale accounts, misconfigurations, privilege creep, and inadequate monitoring gaps that leave organizations dangerously exposed to internal and external threats.
Top 10 Warning Signs of Active Directory Risk
The 2025 State of Active Directory Security Report notes that attempts are still underway to fortify AD systems against attacks, but there is much more work to do. Below are ten important findings that indicate how “at risk” your Active Directory may be:
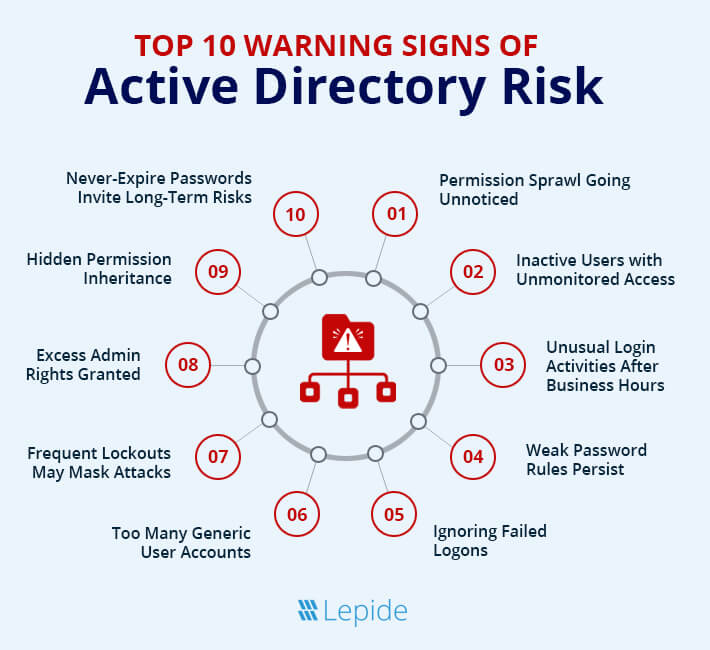
- Permission Sprawl Going Unnoticed: Unapproved or inadequately controlled changes in permissions can lead to sensitive data exposure through permission sprawl. Companies should apply least privilege, reduce nested groups, and discourage delegation without a justifiable cause to halt more privilege escalation and horizontal movement. They should also build a role-based system restricting access.
- Inactive Users with Unmonitored Access: A study by Varonis revealed that 21% of Active Directory accounts within organizations were either inactive or had been abandoned. This highlights the prevalence of unused or forgotten accounts.
Employees’ accounts often remain active after they depart, providing hackers opportunities to deploy techniques like brute force assaults or credential stuffing. If the accounts of former employees or contractors are not handled correctly, hackers could potentially get access to sensitive data. Businesses can use identity and access management (IAM) solutions to set policies to automatically suspend dormant accounts after 30 or 60 days. Quarterly or yearly automatic account audits might also assist in fast spotting and deactivation of any inactive accounts.
Is your Active Directory secure? Find out where your AD vulnerabilities and risks are, and where you compare to your peers in 2 minutes with our free self-assessment. Start your assessment now - Unusual Login Activities After Business Hours: According to a 2024 study by FireEye, approximately 25% of organizations report detecting suspicious activity outside of regular business hours – and those are the ones that are looking for it! Access of data outside of normal business hours by employees or contractors, whether deliberately or by accident, presents an insider threat risk. During these times, privileged accounts and sensitive information are especially vulnerable.To mitigate risk, businesses should monitor user behavior in real-time and have mechanisms to respond to unwanted or unusual activity outside of business hours. SIEM systems may sort log data and detect strange login patterns in order to detect anomalies such as unproven devices, unusual locations, or major system changes.It might also be worth considering time-based access controls that restrict access to vulnerable systems outside of peak hours.
- Weak Password Rules Persist: According to a 2024 survey by Ponemon Institute, 65% of organizations update their password policies at least once a year to improve security and align with changing best practices. However, 45% of organizations are still found to have outdated or weak password policies, which could leave them vulnerable to common attack methods like brute force or credential stuffing. Being ineffective with password policies might really put you at danger. Poor password habits can cause major issues if multi-factor authentication (MFA) is not in place and passwords are not updated frequently enough.One increasing concern is with credential stuffing attacks, where hackers take stolen passwords particularly given that many people tend to reuse passwords over many sites. Though it might cause user tiredness if the standards are too rigid or frequent, regular password changes can improve security.Use Multi-Factor Authentication for sensitive systems and regularly update passwords every 60 to 90 days. Continuously train employees on safe password habits and security hazards.
- Ignoring Failed Logons: Failed logons may look like strong password practices on the surface, but they can potentially be indicators of brute force attacks and credential stuffing.The 2023 Verizon Data Breach Investigations Report (DBIR) revealed that failed logon attempts are linked to nearly 40% of data breaches involving external actors. Often, these failed attempts signal attempts to crack user passwords or gain access through unauthorized means, such as exploiting weak or compromised credentials.That is where real-time monitoring and alerts help. For example, a solution like Lepide Auditor can detect and respond when large numbers of failed logons occur over a short space of time, a typical sign of a brute force attack. To prevent unwanted access, businesses should deploy multi-factor authentication (MFA) and implement account lockout policies following a predetermined number of failed attempts. SIEM solutions can also gather, study, and track failed login attempts to improve security.
Want to discover your AD security posture in 2 minutes? Run our free Active Directory Self‑Assessment and get a personalized risk report instantly. Start your assessment now - Too Many Generic User Accounts: According to Statista and Microsoft estimates, over 95% of Fortune 1,000 companies use Active Directory for identity and access management.An attacker may find a way in more easily the more user accounts you have in Active Directory. While security teams mostly concentrate their efforts on privileged accounts, normal accounts can be a gateway for first access, lateral movement, and privilege escalation. As user numbers rise, the dangers connected with misconfigurations like forgotten group memberships or poorly run service accounts grow.Automating user provisioning and deprovisioning helps lower these risks by guaranteeing a consistent approach to account setup and access management. Furthermore, reducing human error and accelerating onboarding and offboarding processes are thereby reduced. Regular audits and cleaning up inactive users and groups further improve AD security.
- Frequent Lockouts May Mask Attacks: A 2024 study by CyberArk found that 55% of organizations have experienced account lockouts at some point, with many of these lockouts being triggered by failed login attempts.Account lockouts are sometimes seen as good security practices, preventing things like brute force attacks. However, not being on top of when, how, and why accounts are being locked out will lead to business disruption and further riskCompanies should implement suitable account lockout policies and educate consumers on safe password behaviors such as avoiding common words and routinely changing their passwords in order to address this danger and lower the frequency of failed login attempts.
- Excess Admin Rights Granted: The proliferation of admin rights has been identified as a catalyst for business disruptions. Our study highlighted that such practices have cost organizations over £4 million in the last two years due to incidents like ransomware attacks exploiting admin accounts.Companies need to determine exactly how many admin users they have and how those users are receiving admin access. Limiting these users will greatly reduce the chances of both an insider threat, and data breaches through the use of a compromised admin user account.
- Hidden Permission Inheritance: According to the state of Active Directory Security Report, improper permission settings or unauthorized permission changes were responsible for 25% of data breaches.Administrators might not always understand how permissions descend from parent to child goods or how nested groups operate. This oversight ignorance could cause you one to unintentionally grant excessively wide permissions, therefore establishing hidden access routes. Access might wind up too broad if they do not grasp the mechanism of inheritance. Controlling permissions gets more difficult when inheritance is disabled or set up improperly, which causes erratic security and uninvited access.Regular inspections and close observation of group nesting are essential to keep a robust and dependable security posture.
- Never-Expire Passwords Invite Long-Term Risks: According to a report by Verizon, organizations with over 10,000 employees are more likely to use “never expire” settings for certain accounts, particularly for service or system accounts, which can be a security concern due to lack of frequent password updates.When passwords are set to never expire, attackers can potentially gain uninterrupted access to your Active Directory (especially when coupled with poor password policy hygiene)Regularly rotating passwords also shortens the window for exploiting compromised credentials by establishing policies such as password expiration every 30 to 90 days. Additionally, multi-factor authentication (MFA) adds an additional layer of security even when non-expiring passwords are often used for service accounts with challenging dependencies.If you have to use passwords that don’t expire, enforcing demanding password requirements and employing MFA on important accounts will significantly improve corporate security.
What Can Organizations Do to Strengthen Their AD Security Posture?
When undertaking a full audit of Active Directory, most IT departments find weak password policies, excessive admin users, and more. By tackling these issues with MFA, automated cleanup, threat identification, and frequent audits, you may significantly reduce your AD attack surface and improve your security in general.
No install. No commitment. Instant results. Our free AD Self Assessment Tool evaluates your surroundings and compares your risk score to get instant results.
Run your Free AD Health Check Today!
Take charge right away since visibility is essential when Active Directory is being attacked.
How Does Lepide Help?
Lepide Auditor for Active Directory provides detailed audit trails with the critical “who, what, where, and when” audit information for all Active Directory changes and events. Lepide provides detailed state-in-time Active Directory security audit reporting so admins can fully understand what their AD looks like. Lepide also tracks user behavior, including logon/logoff behavior and account lockouts.
Want to see the state of your Active Directory? Schedule a demo with one of our engineers or download a free trial.




