
Account lockouts are a common problem experienced by Active Directory users. They arise because of Account Lockout Policies configured in the default domain policy for the Active Directory domain. In this article, we will go through some of the root causes of account lockouts and the way to simplify the troubleshooting process.
Why do Active Directory Account Lockouts Happen?
Account lockouts occur when incorrect login credentials are used, resulting in a user account becoming locked. Active Directory has a threshold in place for logon attempts and when that threshold has been met, the user is locked out by Active Directory.
The threshold can have a duration limit, where it can lock the user account for a specified time period. Attacks such as brute force password guessing, password spraying, and Denial of Service (DoS) can all cause lockouts. This then affects the user’s ability to access resources, resulting in more help desk tickets and decreased productivity for the entire organization.
Common Causes of Account Lockouts
There are various reasons why account lockouts may occur, and identifying the root cause is an essential first step in resolving the issue. Here are some of the common causes for Active Directory account lockouts:
1. Hackers and Password Guessing Attacks
An attempt to hack an Active Directory account can lead to account lockout. If the attacker repeatedly tries to guess the password, it will trigger the account lockout policy. Common methods are brute-force attacks where numerous password combinations are systematically tried, or dictionary attacks where a list of commonly used passwords are tried. These repeated failed login attempts can trigger the account lockout threshold and temporarily or permanently lock the targeted account.
To mitigate password guessing attacks, it is essential to enforce strong password policies which require users to create complex passwords and to change them frequently.
2. Outdated Windows Cached Credentials
Another common cause of Active Directory account lockouts is using outdated windows cached credentials. When a user logs in to their account, their credentials are stored in the local cache. If the user changes their password, the cached credentials could become outdated, and therefore any attempt to use these outdated credentials will result in an account lockout. This can also occur if the user logs in to their account from a different device, and the cached credentials on the original device become outdated.
To prevent account lockouts caused by outdated cached credentials, the cached credentials can be cleared on the user’s device. This can be done by opening the Credential Manager on the user’s device and deleting any stored credentials. An alternative approach is to disable the local cache on the user’s device, which then forces them to enter their credentials each time they log in.
3. Mobile Devices and Disconnected Sessions
Mobile devices and disconnected sessions are another cause of account lockouts. When a user logs in on a mobile device and the device stores the user’s credentials, there can be an account lockout when the user attempts to use those same credentials on another device. Disconnected sessions can also be a problem if a user logs in to their account from one device and then logs in again using another device before logging out from the first device.
To prevent account lockouts caused by mobile devices and disconnected sessions, you can configure your AD policies to specify the number of concurrent logins for each user account. Also, you can enforce logoff policies that automatically log out users who have been inactive for a specified period of time.
4. Scheduled Tasks
The Windows task scheduler requires credentials to run a task whether or not the user is logged in. Different tasks can be created with user-specified credentials which can be domain credentials. These user-specified credentials may expire but the Windows tasks will continue to use the old credentials.
5. Services Using Expired Passwords
Many organizations use services that require user accounts to have passwords that expire after a certain period of time. However, if the user does not update their password before it expires, any services using that password will cause an account lockout.
To stop the problem of Active Directory account lockouts caused by expired passwords, you can configure your AD policies to send notifications to users when their password is about to expire. Another option is to enforce password policies requiring users to change their passwords before they expire.
6. Users Forgetting Their Passwords
When a user forgets their password in an AD environment, it can lead to them being locked out of their account with their repeated password attempts.
If a user attempts to reset their password, they may encounter security measures such as security questions or multifactor authentication (MFA). If they are unable to give the correct answers or complete the additional authentication steps, the password reset process may fail, which will result in a locked account.
How to Avoid Account Lockouts
A proactive approach to security is needed to prevent account lockouts. The following best practices will help to avoid account lockouts:
- Implement strong password policies so that users must create complex passwords and change them regularly.
- Apply strict password policies for shared accounts.
- The number of concurrent logins should be limited for each user account.
- Apply logoff policies so that users are automatically logged out after they have been inactive for a specified period.
- Configure Active Directory to send notifications to users when their password is about to expire.
- Enforce a limit on the number of devices that can use a single account.
- Have a requirement that users must log in to their accounts from dedicated workstations.
- Educate users on the importance of security and the risks of malware and password guessing attacks.
Related Articles:
Troubleshoot Account Lockouts with Lepide Auditor
If you’re experiencing a high number of account lockouts in a secure environment it would indicate an imbalance between security and convenience. Every organization needs to determine an appropriate compromise between security and convenience. To do this, they will need to consider the sensitivity of the information in their settings, the risks they can bear, and their users’ interests.
Third-party solutions, such as Lepide Active Directory Auditor, can help navigate to the source and root cause of account lockouts faster and fix them easily.
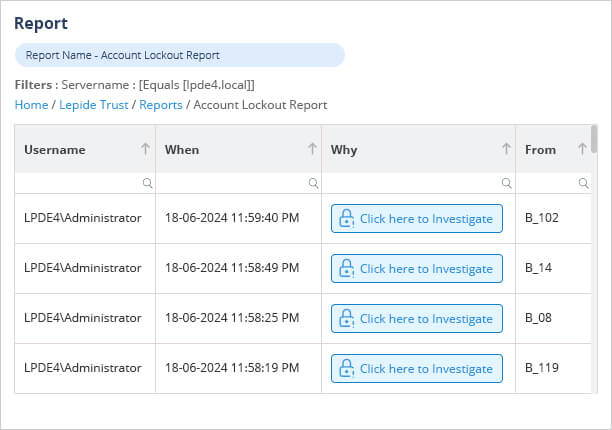
As you can see in the above screenshot, Lepide AD Auditor can quickly generate the report of all locked accounts, you can investigate the reason for the lockout of each account individually and resolve it.

 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them
