Flexible Single Master Operations (FSMO) originated from Microsoft’s work to move towards a Single Master Model in Active Directory. This meant that just one Domain Controller (DC) could make changes to the domain. However, this became a problem as if the master DC went down, as no changes could be made at all until it was back up again.
The solution was to separate the responsibilities of the DC into several roles. This meant that if one of the DCs went down, another one could take over the missing role. This is known as Flexible Single Master Operation (also known as FSMO or FSMO Roles).
There are five FSMO roles. By default, when you create an Active Directory domain, all FSMO roles are assigned to the first domain controller in the forest. However, domain admins can reassign FSMO roles to other domain controllers if required.
There are 5 Flexible Single Master Operations (FSMO) roles:
- 2 forest-wide roles:
- Domain Naming Master
- Schema Master
- 3 domain-wide roles:
- PDC Emulator
- RID Master
- Infrastructure Master
It is essential to regularly monitor FSMO roles as if a compromised user transfers the FSMO role from one domain controller to another, this could cause a huge security risk in the network. This transfer of FSMO role could be misused by users with admin access to that DC.
This document explains four different native ways to check FSMO roles before looking at a more straightforward method of using the Lepide Data Security Platform to list all Domain Controller changes
How to List Current FSMO Role
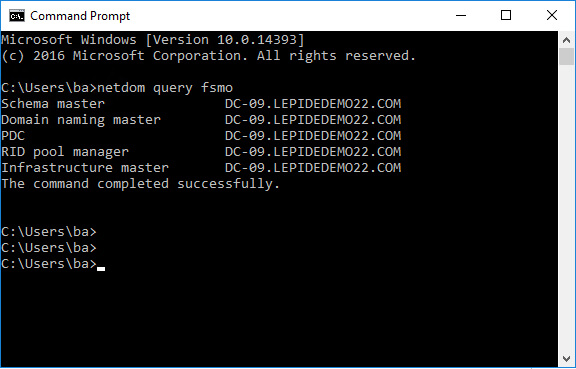
1. List Current FSMO Role Holders using netdom
netdom query fsmo
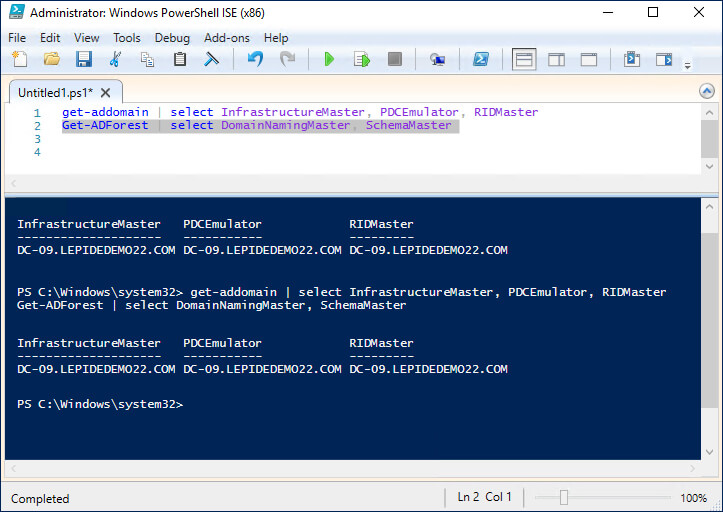
2. List Current FSMO Role Holders using PowerShell
You can list which domain controllers hold FSMO roles with these two PowerShell commands:
To get domain level FSMO roles:
get-addomain | select InfrastructureMaster, PDCEmulator, RIDMaster
To get forest level FSMO roles:
Get-ADForest | select DomainNamingMaster, SchemaMaster
How to Check FSMO Roles Changes?
1. Enbale Auditing using GPMC
The following actions need to be carried out on the domain controller (DC):
- Open the Group Policy Management Console
- In the Group Policy Management Console, browse to the OU, right click and select Create a GPO in this domain, and Link it here. Name the GPO and then link it to an OU
- Right-click on the GPO, and choose Edit
- From the left pane of the Group Policy Management Editor, navigate to Computer Configuration, Policies, Windows Settings, Security Settings, Local Policies, Audit Policy, DS Access
- In the right pane, you will see the following policies that are under DS Access:
- Audit Detailed Directory Service Replication
- Audit Directory Service Access
- Audit Directory Service Changes
- Audit Directory Service Replication
- Double-click each of the audit policies and check the boxes under Configure the following audit events, Success and Failure
- Click Apply and then OK
2. View FSMO role change events using Event Viewer
Perform the following actions on the Domain Controller:
- Click Start, search for Event Viewer, right-click it, and select Run as administrator
- On the left pane in the Event Viewer window, navigate to Applications and Services Logs, Directory Service
- On the right pane under Actions, click Filter Current Log….
- In the pop-up window, enter Event ID 1458 in the field labeled
- Click OK
This will give you a list of where Event ID 1458 has occurred. Double-click on the Event ID to view its properties.
3. View FSMO role Using Active Directory Users and Computers (ADUC)
- Open Active Directory Users and Computers on a computer with the Active Directory tools installed.
- Right-click on the root of the console (usually “Active Directory Users and Computers” at the top).
- Select Operations Masters…
- This will open a dialog box showing the three FSMO roles for the domain. You can switch between tabs to view forest-level FSMO roles as well.
Though native auditing allows you to look for changes in the FSMO roles, it can be a complex and time-consuming task and can be difficult to manually analyze and investigate changes on a large scale. An alternative, more straightforward solution is to use the Lepide Data Security Platform to monitor Domain Controller activity.
How Lepide Helps
Among the many pre-defined reports which are including within the Lepide Auditor for Active Directory, there are several Domain Controller Reports. These reports are easily generated and require no knowledge of PowerShell scripting. An example of the Domain Controller Logon/Logoffs Report is shown below:
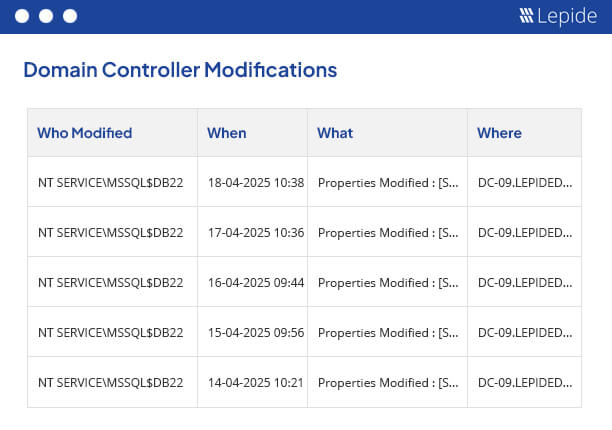
To run this report:
- Select Lepide Auditor, Reports
- From here, expand Active Directory from the tree structure on the left-hand side
- Select Domain Controller Logon/Logoffs
- Specify a Date Range or leave it as the default of today
- Select Generate Report