Last Updated on January 17, 2025 by Satyendra

Microsoft Exchange Server is a popular email server application that runs exclusively on the Windows Server operating system. However, over the years, Exchange Servers have been subject to a number of vulnerabilities. In 2021, a China-based attacker group called Hafnium targeted over 400,000 unpatched on-premises servers by exploiting multiple zero-day vulnerabilities to access email accounts and then installed malware to obtain long-term access. Microsoft identified the vulnerabilities and released security updates and patches, but the group had already gained access to over 30,000 organizations in the United States.
This recent wave of attacks on Microsoft Exchange Servers highlights the need for companies to prioritize their security best practices. They must reduce their attack surface against unauthorized access, cyber-attacks, viruses, and malware to mitigate risk and reduce damage.
Following guidance from Microsoft to help address these vulnerabilities is a good place to start. However, there are numerous other Exchange Server security best practices that should be followed to adequately protect against future attacks. In this article, we will go through some of those best practices.
Exchange Server Hardening Best Practices
1. Exchange Server Should be Up to Date
The first and most obvious Exchange Server security best practice is to ensure that Exchange Server is always up-to-date. Microsoft frequently publishes patches and bug fixes, which users must install as soon as they become available.
2. Use Exchange Server Security Utilities
Microsoft also provides a number of Exchange security utilities that will help to ensure that you are able to protect yourself from unauthorized access, viruses, malware, and other threats. These utilities include;
-
- Microsoft Exchange On-Premises Mitigation Tool: Microsoft has recently released a new one-click mitigation tool that is designed to make it easier for customers who don’t have a dedicated IT team to install the relevant security updates.
- Exchange Best Practices Analyzer (EBPA): EBPA is a tool that helps administrators gauge the health of their Exchange Server environment. The tool will collect data from the Exchange server, analyze the results, and then offer guidance based on Microsoft’s recommended best practices.
- Microsoft Safety Scanner: This tool will scan for any malware installed on your Windows environment, and remove it accordingly. The tool is also known as the Support Emergency Response Tool. It should also be noted that the Microsoft Safety Scanner is included with the Exchange On-Premises Mitigation Tool, mentioned above.
- Microsoft Defender Antivirus: This is the standard anti-virus/malware solution that comes with recent versions of Windows, and also covers Exchange.
- Microsoft Security Configuration Wizard (SCW): SCW gives administrators the ability to easily change a server’s default security settings. This includes the ability to customize network security policies, audit policies, registry values, and services.
- Microsoft Security Compliance Toolkit (SCT): SCT is a suite of tools that enables enterprise administrators to download, analyze, test, edit, and store recommended security configuration baselines for Windows, including Exchange.
- Exchange Analyzer: This is a PowerShell tool that scans Exchange Server and provides reports on various common configuration issues as well as recommendations for improving Exchange security.
- Microsoft Exchange Online Protection (EOP): EOP, which has now been integrated into the Microsoft 365 Defender portal, is designed to protect Exchange mailboxes. EOP can be used with on-premises, cloud, and hybrid environments.
- Microsoft Exchange antispam and antimalware: Both Exchange Server 2016 and Exchange Server 2019 come with antispam and antimalware protection features, which are enabled by default on Exchange Mailbox servers.
3. Use Allowlists and Blocklists
As with most popular email clients, you can allow/block emails from trusted/untrusted senders. Within Outlook you can find a list of allowed domains via the Safe Senders tab, and a list of blocked domains in the Blocked Senders tab.
4. Restrict Administrative Access
Giving your users remote access to your Exchange servers is a huge security risk. As such, it is imperative that you limit access to Exchange Servers to internal users only. In cases where remote access is genuinely required, implement multi-factor authentication as an additional layer of security.
5. Enable SSL/TSL for External Services
SSL (Secure Sockets Layer) and its successor, Transport Layer Security (TLS), are used to provide an encrypted communication channel between two computers over the Internet. By enabling SSL/TLS encryption for both the incoming and outgoing mail servers, we can ensure that our emails have not been intercepted and tampered with.
6. Audit Exchange Server Changes and Mailbox Access
It’s important to be able to monitor, detect and set alerts for suspicious behavior in Exchange. If you use Exchange Online, you can take advantage of Azure Monitor, which will scan your entire environment including Exchange Server, and deliver performance reports to your inbox.
However, if you want more comprehensive auditing with customizable reports and real-time alerting capabilities, then a third-party solution, for example, the Lepide Data Security Platform, may be a preferred option.
Third party solutions will also provide permissions analysis delivering visibility on who is accessing which mailbox accounts and this includes when they were accessed, from where, and the activities that were performed. Permission changes can be monitored across on-premise, cloud, or hybrid environments and a real-time alert can be sent to the administrator when a user tries to access a mailbox that they are unauthorized to access. Configuration changes can also be tracked making it easy to investigate who made the changes and why they were made.
A third-party solution will also deliver alerts when sensitive data is sent via email, even if the recipient is a member of your organization. Most sophisticated solutions use machine learning algorithms to establish typical usage patterns and will send an alert whenever user activity deviates from these patterns.
7. Deploy firewalls
Installing Exchange server will automatically add rules to Windows Firewall, a Microsoft component which is installed by default in most recent versions of Windows. However, there are times when Windows Firewall can cause problems and it may seem like a good idea to disable it and assume that your network firewall is enough. But, doing this is a security risk and should be avoided at all costs, in particular for on-premises servers.
There are also third-party firewalls available which are designed for Exchange but when evaluating these, check that they support the Exchange Server version being used..
8. Enable role-based access control (RBAC) and require strong passwords
Organizations should enable role-based access control, which configures, and grants permissions based on employees’ roles within the organization and their need to perform specific actions. It grants access based on the principle of least privilege, whereby users have access to the bare minimum of functionality necessary to do their job.
The use of strong passwords is an important complement to RBAC and other authentication measures. Easy passwords make it easy to gain access. Enforcing both a minimum password length and the use of unique characters are the best ways to prevent brute force and password spraying attacks.
9. Enable Multi-factor Authentication for OWA
Outlook Web Access (OWA) is a feature in Exchange that enables users to access their email from a web browser which can be a more convenient option for them. By default, this only requires a username and password to login and gain access. However, this makes it easy for hackers as they can use brute force or steal credentials via phishing attacks to access these mailboxes that are openly running on the internet. To prevent this, multi-factor authentication (MFA) should be enabled for users logging into OWA.
10. Using OS hardening tools
Finally, consider using OS hardening tools, such as Microsoft Attack Surface Analyzer, which will help you configure your OS security settings, install patches, set up security rules and remove any unnecessary or unused applications and services.
How Lepide Helps with Exchange Server Security
The Lepide Exchange Auditing Solution provides a simple, cost-effective way of seeing who, what, where and when changes are made to your Exchange environment. Through a combination of real-time monitoring, pre-defined reports, and powerful alerting capabilities, it enables you to get increased visibility into mailbox access, permissions, and the overall health of your Exchange Server.
An example of one of the pre-defined reports from the Lepide Solution is the All Modifications in Exchange Server Permission Report:
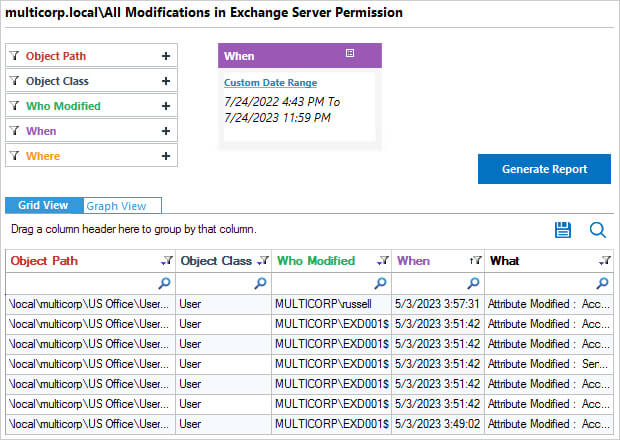
This report shows all modifications made to Exchange Server within a specified time period. The information includes who made the modification, what the modification was and when it was made.
This Is one of a number of pre-defined reports available within Lepide Auditor and together with real time alerting, it gives you full visibility of changes taking place on your Exchange Server. The Lepide Solution is straightforward to use, it’s scalable, and allows you to address a wide range of security, operations, and compliance challenges – all from a single console.
If you’d like to see how Lepide Auditor for Exchange can help keep your Exchange Server secure, schedule a demo with one of our engineers.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
