Last Updated on April 7, 2025 by Satyendra

Does the thought of keeping your Active Directory secure keep you up at night? If you’re an IT administrator, I can understand your pain. Active Directory controls access to critical systems and data; so it’s the ultimate prize for attackers. Ensuring that your Active Directory is secure should be your number one priority.
What Are the Top 10 Threats to Active Directory Security?
Below is the list of the most common Active Directory security risks.
- Too Many Administrators
- Delegating Too Many Tasks in Active Directory
- Short and Simple Passwords
- Leaving Inactive Accounts
- Increasing Open Access
- Not Knowing Who’s Logging
- Relaxed Password Policies
- Not Knowing the Members of Security Groups
- Unaware of Permission Inheritance
- Not Implementing Least Privilege Policy

1. Too Many Administrators
There’s an old saying you may be familiar with; “too much of anything isn’t good for anyone.” This rings true for Active Directory security. If you have an overly long list of Active Directory users with Administrative rights, it’s likely that you’ve offered excessive levels of privilege to accounts that don’t require them. This has the potential to lead to privilege abuse, which is one of the leading causes of data leakage.
Download 20-Day Free Trial

2. Delegating Too Many Tasks in Active Directory
Delegating tasks to non-administrators is easy to do, and it’s particularly tempting when you realize how much time you can free up. However, delegating too many tasks to non-administrators, without proper evaluation and tracking, could be a risk. Especially if those tasks involve dealing with sensitive data in Active Directory.
3. Short and Simple Passwords
Don’t be tempted by convenience! Short, simple passwords may be easy to remember, but they’re also easy to guess. All it takes to compromise your entire Active Directory database is one weak password on an account with Administrative rights. Ensure that you set a stringent password policy and force your users to adopt it. Changing passwords every 90-180 days also helps to ensure account safety.
4. Leaving Inactive Accounts
Inactive accounts may appear harmless, but in reality, they are an open invitation for anyone looking to compromise Active Directory. Inactive accounts that hold administrative privileges could be used by platform attackers to gain access to your Active Directory and, as it’s technically a legitimate account, this can be incredibly difficult to spot. Inactive accounts should be disabled and then deleted to mitigate these risks.
5. Increasing Open Access
Well-known security Principals (Domain Users, Everyone, Authenticated users, etc.) can provide users with access to a diverse range of network resources. Whilst these principles can be used to grant access to large groups of valid accounts, be careful that your Guest and Anonymous accounts are not granted the same open access. If they are, you could potentially be leaving your organization vulnerable to data theft!
6. Not Knowing Who’s Logging in to Your Domain Controllers
Not knowing who has the ability to log in to your Domain Controller makes it difficult to protect privileged identities and vital information. A blind spot like this within Active Directory can be costly. Instead, ensure that you have a continuous and proactive way of keeping track of such logins, so that you can quickly spot and react to anomalies.
7. Relaxed Password Policies
Your password is essentially the lock that keeps your network secure. It is unwise to compromise when developing your password policies to cater to the laziness of your users. Many IT teams have told us that employees in their organization have the habit of leaving their computers unlocked, writing their passwords down, or even sharing passwords with other users. Your password policies must be stringent and you must have a way of ensuring that they are followed to the letter – even if that means simply educating users about the risks of poor password management.
8. Not Knowing the Members of Sensitive Security Groups
Members of sensitive security groups like Domain, Enterprise, and Schema Administrators have the highest levels of privileges. If the credentials to an account with these privileges are stolen, it can be very damaging to your organization’s security. To mitigate these risks, only grant membership to those accounts that need it, and withdraw group memberships the minute they are no longer required.
9. Unaware of Permission Inheritance in Group Nesting
Active Directory nests groups are based on a parent-child hierarchy. When a group is added as a member of an administrative group, all members of that group will receive administrative privileges. This could potentially mean unauthorized personnel getting access to sensitive data. Don’t forget to track Group Nesting.
10. Not Implementing Least Privilege Policy Models
The principle of least privilege policy states that users should log on with a user account that has the absolute minimum permissions required for their job, nothing more. Whilst most can see the logic in such a policy, you’d be surprised at the number of organizations that do not follow it. You should be consistently tracking changes to privileges to ensure that the right users have the right levels of access to the right data. This will drastically reduce the risk of insider threats.
How Lepide Helps with Active Directory Security
Lepide’s Free Tool for Active Directory Auditing to enable you to disrupt attack paths and secure Active Directory by finding and fixing vulnerable security states, and detecting and responding to threats in real time.
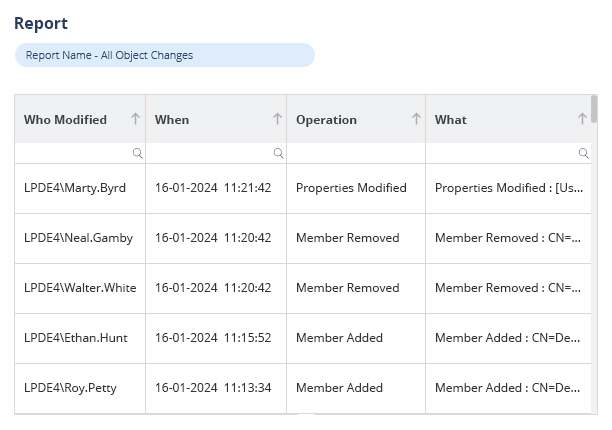
Lepide also maintains a complete history of Active Directory events, with advanced searching, sorting and filtering capabilities to make investigations of any potential security incidents easy and effective. You can also produce compliance-ready reports with all required audit information contained within a single pane of glass.
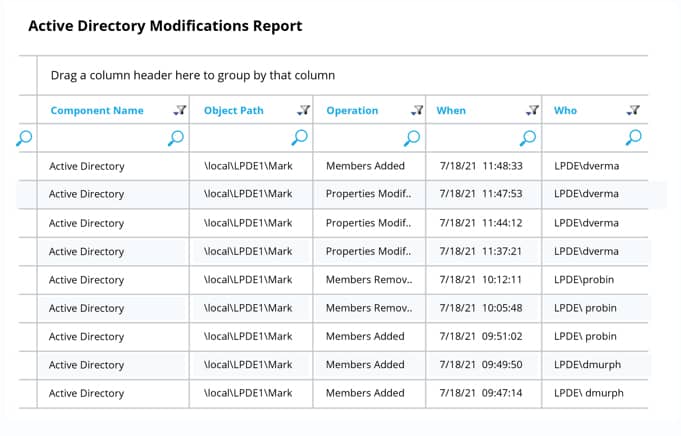
If you want to see how Lepide’s free tool for Active Directory auditing works, download the free tool today.

 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
