With cloud adoption rates continuing to rise, it would suggest that users are increasingly trusting cloud-based platforms. More and more organizations, including those in finance, healthcare, and education, are storing sensitive information in the cloud and trusting that it is secure. However, security controls and visibility into key changes aren’t always as effective as some comparable on-premise platforms and one way to resolve these issues is to check the Microsoft 365 audit logs on a regular basis.
In this article we will look at what audit logging is in relation to Microsoft 365, why it is important that it is monitored regularly and how it’s done. We will then offer an alternative solution to the native Microsoft 365 approach to make the whole process much easier.
Why Check Office 365 Audit Logs?
Office 365 comprises multiple services, including Microsoft Teams, Exchange Online, Azure AD, SharePoint Online, and OneDrive for Business. Monitoring these Office 365 services can be a challenging task for system administrators who are often managing multiple sub-admins and sometimes thousands of users.
Office 365 audit logs help to track admin and user activity, including who’s accessing, viewing, or moving specific documents and how resources are being used. To be able to investigate security incidents and demonstrate compliance, these logs are crucial. However, the native logs have several limitations, so additional services such as Lepide Auditor for Office 365 are usually needed to monitor activity effectively, keep systems secure, and ensure regulatory compliance.
Download Whitepaper

How to Turn On/Enable Office 365 Auditing?
Before capturing user and admin activity, you must activate audit logging features (they are disabled by default throughout Microsoft 365). Audit log functionality in Microsoft 365 can be activated through two main methods.
1. Enable via Microsoft Purview Portal
- Sign in to the Microsoft Purview portal.
- Select the Audit solution card. If the Audit solution card isn’t displayed, select View all solutions and then select Audit from the Core section.
- If auditing isn’t turned on for your organization, a banner is displayed prompting you to start recording user and admin activity.
- Select the Start recording user and admin activity banner.
2. Enable via PowerShell
Alternatively, you can enable audit logging using PowerShell, which is especially useful for scripting or bulk operations:
- Open PowerShell and connect to your Microsoft 365 tenant.
- Run the following command:
Set-AdminAuditLogConfig -UnifiedAuditLogIngestionEnabled $true
How Long Does it Take to Capture the Events?
Processing takes several hours for the audit logging system after you turn it on by manual deployment or PowerShell scripts. The duration for unified audit log search results depends on the service as well as the activity volume of your tenant, which leads to a search window between 30 minutes to 24 hours.
How to Run an Office 365 Audit Log Search?
Prerequisites
Before you can run an audit log search, an admin must assign the required permissions to your account. The permissions can be either View-Only Audit Logs or Audit Logs.
You may have to wait several hours from the time you enable log auditing before you can run an audit log search. A unified audit log search consolidates data from multiple Microsoft 365 services into a single log report, which requires anywhere from 30 minutes to 24 hours to complete.
To run an audit log search:
- Log In at https://protection.office.com.
- Start a New Search.
In the Security & Compliance Center, click Search, Audit log search. - Configure Your Search Criteria
The main criteria to specify are:- Activities — There are over 100 of these, so they have been grouped into related activities. You will need to narrow this down otherwise your audit report will include all activities performed during the time frame specified.
- Dates — The default time frame is the last seven days, but you can configure your search for any period within the last 90 days.
- Users — Specify which user or group of users you want to include in your report.
- Location — Use this option if you want to limit the search to a particular file, folder, or site. Enter a location or keyword.
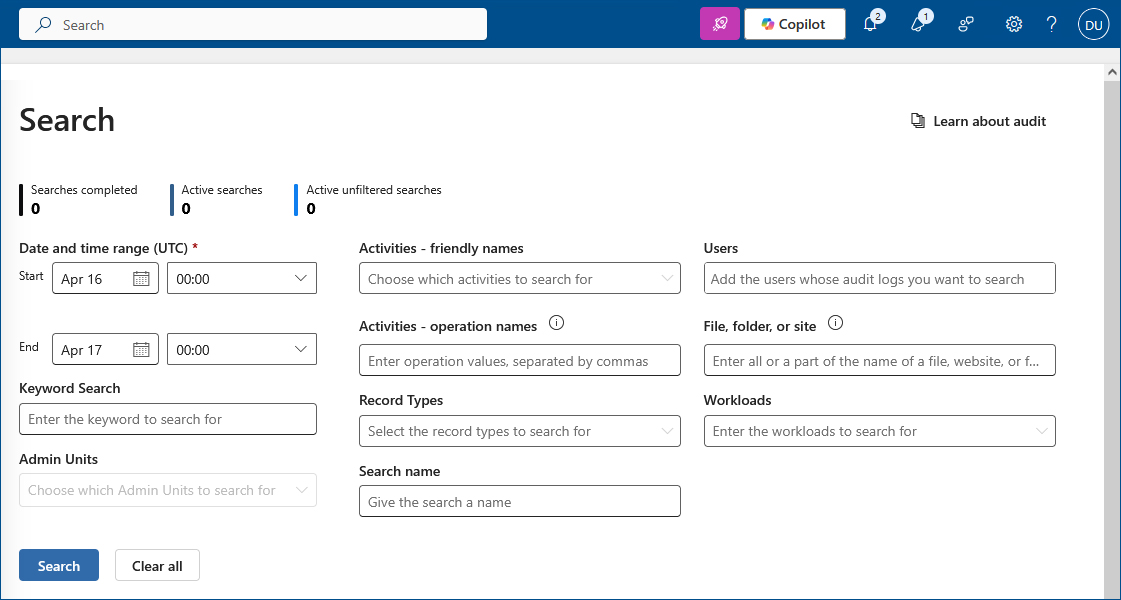
- Filter the Search Results
Filtering the search results will help you analyze the data more effectively. You can enter keywords, specific dates, users, items, or other details.
You can also generate a report of raw data that meets your search criteria by exporting the data into CSV. This lets you download up to 50,000 events instead of the usual maximum of 5,000. To generate even more than 50,000 events, work in batches of smaller date ranges and combine the results manually.
- Save your Results.
To save your results, click Export results and choose to Save loaded results to generate a CSV file with your data. You can then use Microsoft Excel to access the file.
There is a column called AuditData, which consists of a JSON object that contains multiple properties from the audit log record. To enable sorting and filtering on those properties, use the JSON transform tool in Excel’s Power Query Editor to split up the AuditData column and give each property its own column.
What are the Limitations of Native Searches in Microsoft 365 Audit Logging?
The essential tracking function of native audit logging creates multiple challenges for security and compliance because of these key restrictions:
- Limited and complex search capabilities affect event detection because the interface options restrict users from performing efficient and timely investigations through proper event searches.
- The system requires users to configure search filters each time they run reports, and there is no automated reporting option.
- Each search through the interface returns only up to 5,000 events, which limits the ability to examine frequent system operations in extensive monitoring areas.
- Audit data becomes available with a considerable delay between 60 to 90 minutes for core services and spans beyond this period for different services.
- The tracking of audit events requires manual configuration because default tracking does not include all possible audit events
- Slowdowns and unresponsiveness occur within the compliance center when it serves environments with over 5,000 users.
- Auditors struggle with analyzing exported audit data because of its challenging nature to handle security, while native tools lack efficient anomaly detection capabilities.
How Long Should You Retain Your Office 365 Audit Logs?
Audit logs must be retained by organizations according to three fundamental factors, i.e., security requirements, compliance guidelines, and investigative demands. The default Microsoft 365 retention policies include 180 days for general users, and E5-licensed users benefit from extended retention of up to one year. Nonetheless, many regulatory guidelines and industry best practices recommend retaining logs for periods exceeding these defaults. Audit logs according to HIPAA must be preserved for at least six years, but certain organizations need to store their logs up to ten years to fulfill their legal and industry standards.
The extended log retention duration helps forensic investigators conduct better post-breach investigations while presenting crucial audit trails to compliance auditors. Organizations should evaluate their regulatory protocols together with risk assessment and incident response needs to find the appropriate retention duration for their audit logs.
How to Create Audit Log Retention Policies?
For organizations with an Office 365 E5 license or Microsoft 365 Advanced Compliance add-on, you can create custom audit log retention policies to define how long specific audit logs are retained:
- Go to the Microsoft Purview Portal and log in.
- In the left navigation panel, click Show All, then click Audit.
- When the audit page is displayed, click “Create an audit retention policy.”
- Complete the fields on the “New audit retention policy” page:
- Name: A unique name to identify the log retention policy.
- Description: Optional, but can provide useful information about the policy
- Users: List the names of users the policy applies to. This is optional, but if left blank, the policy will apply to all users, and the Record Type cannot be left blank.
- Record Type: Identify the record type the policy applies to. This can be left blank only if users are identified.
- Duration: Identify the amount of time to retain the audit logs within the policy.
- Priority: Assign a priority value to determine the order in which audit log retention policies are processed. A higher value indicates a higher priority.
- Click Save to create the new audit log retention policy.
How Lepide Helps
All these limitations are removed when you use the Lepide Auditor for Office 365 to check Microsoft 365 Audit Logs.
Lepide Auditor stores audit trails for years with no limitations regarding how long the logs are retained, and they are easily searchable, sortable, and filterable so that you can get all the information you need whenever you need it.
Reports can be generated, and alerts configured giving answers in real-time to the who, what, when, and where auditing questions in a simple, friendly, easy-to-use dashboard.
Lepide’s Office 365 auditing software includes a large number of pre-defined reports to choose from, which can be generated at the click of a button. These reports include but are not limited to:
- External Data Sharing
- Permission Modification
- User Modification
- Document Modification
- Policy Modification
- Group Modification
Along with the reports, you can use our Office 365 auditing tool to set up real-time alerts to be activated when specific events take place, and these can be sent to your inbox or mobile app. In addition, automated threat responses can be triggered if immediate action is required. For example, an automated response might involve running a script to carry out remedial action like shutting down a server.
If you’d like to see how Lepide can help check your Microsoft 365 Audit Logs, schedule a demo with one of our engineers.




