Last Updated on January 17, 2025 by Deepanshu Sharma

SQL Server has many security features that you should review and configure according to your needs, as using the default security settings may leave holes in your security posture.
SQL Server Security Best Practices
Below are some of the most notable SQL Server security best practices that you should follow to keep your sensitive data secure:
Harden Your Windows Server Environment
Before reviewing your SQL Server security settings, you will first need to harden your Windows Server OS, as hackers can copy your entire database to their own server, where they can brute-force-guess the passwords and possibly break your encryption methods to gain access to your data.
Only Install the Required SQL Database Components
It is a good idea to minimize your attack surface by removing any components you don’t need, as they may have security vulnerabilities, consume unnecessary resources and increase the administrative burden.
Limit the Permissions of Service Accounts
All service accounts should be granted the least permissions they need to perform their role. You can configure these permissions in the Server Configuration Manager. At a minimum, permissions need to be restricted for the following AD accounts.
- Active Directory managed service account
- Domain user account
- Local user account
- Local system account
- Network service account
- Virtual service account
Disable the SQL Server Browser Service
The SQL Server Browser Service makes it possible for adversaries to obtain knowledge about the available SQL Server resources and should either be disabled or configured to use a different port for communication.
Use Groups and Roles to Simplify Management of Effective Permissions
Effective permissions are the cumulative permissions a user has to a resource based on their individual permissions, group permissions, and group membership, including permissions inherited from a parent resource. In order to simplify the management of effective permissions, the best practice is to create containers, groups, or roles, and assign permissions (and users) to those containers. It is essentially the same principal as Role-Based Access Control (RBAC).
Follow the Principle of Least Privilege When Assigning SQL Server Roles
There are nine default SQL Server roles, each with its own set of permissions. For example, a Sysadmin role allows users to perform any activity within an SQL server, whereas the Dbcreator role only allows users to create, alter or drop databases. It is important to strictly adhere to the Principle of Least Privilege (PoLP) when assigning users to these roles, to ensure that they don’t have more access than what they need. If the default roles are not sufficient, you can create a custom role using either Transact-SQL or the Management console.
Use Strong Passwords for All User Accounts
If using multi-factor authentication is not an option, you must at least ensure that you are using strong passwords for all user accounts, which consist of uppercase and lowercase letters, numbers, and special characters. However, passphrases are generally considered to be a better choice as they are sufficiently complex, yet easy to remember.
Install SQL Server Updates in a Timely Manner
Adversaries and security experts are constantly discovering vulnerabilities in SQL Server. Microsoft frequently publishes updates to fix them, which include Hotfixes, Cumulative updates (CUs), and Service packs (SPs). However, the best way to keep SQL Server up-to-date is to simply enable automatic updates from Microsoft. In some cases, such as with large organizations, it’s might be a good idea to test the updates in a separate environment before applying them to the production server.
Use Windows Authentication Mode
There are three main authentication options available to SQL Server, which are as follows:
- Windows Authentication Mode
- SQL Server Authentication Mode
- SQL Server and Windows Authentication Mode
The Windows Authentication Mode is generally considered to be the safest option as it can leverage Active Directory account, group, and password policies. If you decide to use SQL Server Authentication Mode, make sure you disable the sa account as it is the first account that hackers will try to compromise. As you may have guessed, the third option is a mix between the two, although it is less commonly used.
Configure Password Options for Logins
In Windows Server, administrators can enable policies that control factors such as password complexity and expiration. In SQL Server, administrators can also manage settings for SQL Server logins. The options are as follows:
MUST_CHANGE — This setting will prompt a user to change their password when they logon for the first time.
CHECK_POLICY — This setting should always be enabled as it controls the password policies for the computer on which SQL Server is running.
CHECK_EXPIRATION – This setting requires the user to periodically reset their password
Purge any Unused Logins
It is a good idea to periodically review your logins and delete any that have been disabled for more than one year.
Use a Robust Database Backup Strategy
SQL Server allows for two types of backups: full backups and incremental backups. For small databases, you may as well use full backups every time. However, for large databases, you might want to consider using a file and filegroup backup strategy, which backs up only certain files or filegroups. This method is better if you want to back up and restore a small number of files, although the process is more complicated.
Monitor Activity on Your SQL Server
It is a good idea to monitor your SQL Server environment for suspicious activity. Such activity might include unauthorized access to privileged accounts and sensitive data, as well as changes to SQL Server configurations and permissions. Your chosen auditing solution should use machine learning techniques to establish a baseline of “normal” activity. If one or more events occur which deviate too far from this baseline, the administrator should be alerted so that they can launch a prompt investigation. This can be done using a third-party auditing solution such as the Lepide Data Security Platform.
Protect Against SQL Injection Attacks
An SQL injection attack is where an adversary injects malicious code into an unsecured web form in an attempt to extract data by executing SQL queries on the database. All database queries should be properly sanitized for malicious code, or even better, only allow pre-defined commands to query the database.
Use Encryption Whenever Possible
Encryption is an effective way to prevent unauthorized access to your data. SQL Server allows for three main types of encryption, which include:
Transparent data encryption (TDE): Encrypts the physical files in a way that is transparent to the applications accessing the data. With TDE, the information stored in memory is not encrypted.
Column level encryption: Encrypts specific columns in a database, such as credit card details or Social Security numbers.
Always encrypted: Encrypts data both at rest and in transit, including data stored in memory. Of the three methods, this is the most secure as it protects the data from rogue administrators, man-in-the-middle attacks, and more.
How Lepide Auditor Ensures SQL Server Security
Lepide Auditor for SQL Server provides a range of features and functionalities that enhance the security posture of SQL Server environments.
One of the primary ways Lepide SQL Auditor ensures SQL Server security is through real-time monitoring and alerting. It continuously tracks and records all activities and changes made within the SQL Server environment, including logins, user activities, schema modifications, and configuration changes. This real-time monitoring allows administrators to quickly identify any unauthorized or suspicious activities and take appropriate actions to mitigate potential security risks.
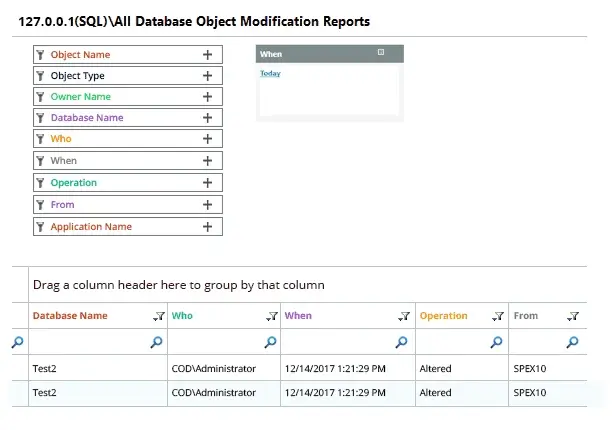
Lepide’s SQL Server Auditing tool also provides detailed audit trails and comprehensive reports. These reports include information about user activities, failed login attempts, permission changes, and other critical events. By having a complete record of all activities, administrators can analyze the audit trails to detect security breaches, identify vulnerabilities, and comply with regulatory requirements.
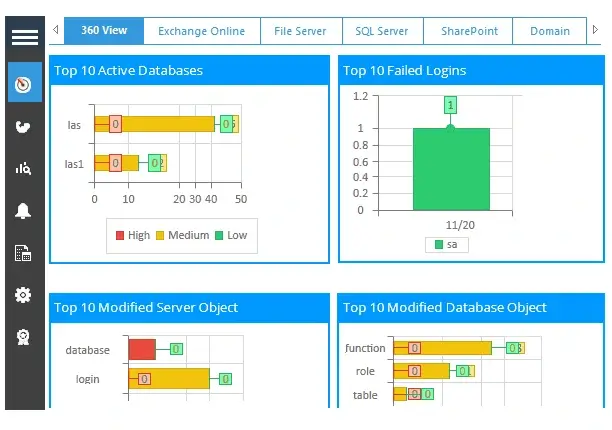
Lepide SQL Auditor offers built-in threat intelligence and anomaly detection capabilities. It uses machine learning algorithms to identify patterns and behaviors that deviate from the normal usage patterns. This enables it to detect potential insider threats, unusual data access patterns, and suspicious activities, allowing administrators to take proactive measures to prevent security incidents.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
