Organizations typically focus on securing their networks by purchasing firewalls, SIEMs, and advanced endpoint security solutions. Unfortunately, far too often we see that companies neglect basic Active Directory (AD) security when it comes to their accounts. Forgetting to remove outdated or dormant accounts in Active Directory provides the perfect target for hackers to get undetected access to your critical data.
Why Inactive Users in AD Are a Hidden Threat?
A Free Pass into the Network
Often, even when inactive, an account still has all the privileges it had before. When these accounts are accessed, it means the attacker can immediately access sensitive systems; there is no need to penetrate the system through a weak point.
After that, attackers can travel around the network, increase their permissions, and hide among normal traffic.
In fact, according to The State of Active Directory Security by Lepide, 21% of Active Directory accounts within organizations were either inactive or had been abandoned, each one a possible entry point.
No One’s Watching
Since these accounts are not linked to people or their devices, they are often not noticed. Nobody is accessing the platform. No alerts are being created. This is why they are the ideal way for anyone trying to spread malware. Hackers realize this and try to find these gaps.
Real-World Examples of Inactive Account Exploitation
U.S. State Government Breach (2024)
An official report explains that unauthorized access to the network of a U.S. State Government organization happened via a former employee’s administrator account. The attacker managed to get into an internal virtual private network (VPN) with the help of the ex-employee’s credentials. The incident shows that inactive users can be dangerous because they stay active even when no one uses them. Because of this unauthorized access, host and user data previously considered secret were posted to the dark web.
The Marriott Data Breach (2020)
The attackers used the logins of two old employees from a franchised property to get through the data breach at Marriott. Even though the accounts weren’t being used, they weren’t shut down, and attackers could still get in unnoticed.
Why Do Organizations Fail to Clean Up Inactive Users in AD?
- Outdated Processes: It is common for IT teams to use traditional methods for removing employee access to resources. When someone in the company leaves or a machine is retired, handling account access isn’t always thought of first.
- Fear of Breaking Things: Several accounts are left alone, mainly service accounts, as non-experts can’t identify what functions they handle. Deactivate the wrong account, and you may see the loss of important services.
- Lack of Visibility: In most cases, companies simply do not know how many AD users are inactive. This comes down to a lack of proactive auditing, and an over-reliance on event logs and PowerShell (both of which are reactive).
How to Detect Inactive Users in AD?
Proactively identifying stale accounts doesn’t have to be overly complex. Here’s how you can start:
- Use LDAP Queries– You can identify inactive accounts using LDAP queries based on the lastLogonTimestamp attribute.Here’s an example LDAP filter to find user accounts inactive for 90+ days:
(&(objectCategory=person)(objectClass=user)(!userAccountControl:1.2.840.113556.1.4.803:=2)(lastLogonTimestamp<=))Note: You’ll need to convert your target date to the correct timestamp format. - PowerShell Scripts– PowerShell offers a more flexible and scriptable option. For example, this command lists user accounts that haven’t logged in for the past 90 days:
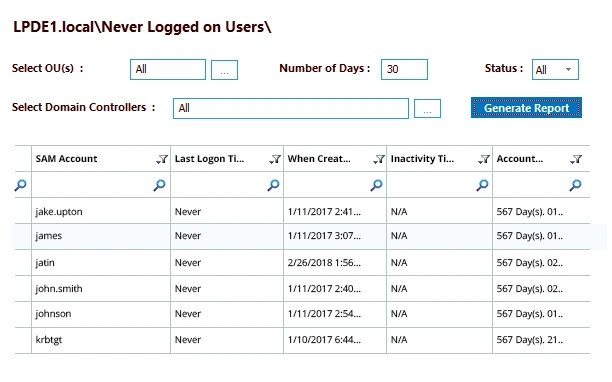
Search-ADAccount -UsersOnly -AccountInactive -TimeSpan 90.00:00:00 | FT Name,LastLogonDateYou can also target computers:Search-ADAccount -ComputersOnly -AccountInactive -TimeSpan 90.00:00:00 | FT Name,LastLogonDateAutomating these scripts and regularly reviewing the output should be part of your AD hygiene routine. - Use a Dedicated AD Cleanup Solution– Manual scripting works, but lacks the efficiency, visibility, and safety net required at scale. That’s why many organizations turn to the Lepide Active Directory Cleanup tool.Unlike basic tools or scripts, Lepide provides real-time insights into account activity, detailed reports on stale user and machine accounts, and intelligent filters to streamline cleanup. It also allows IT teams to identify accounts based on last login, group memberships, permissions, and risk, so decisions aren’t made blindly.
What to Do Once You Detect Them?
- Disable, Don’t Delete Immediately: Always remember to disable first. Check for any sudden malfunctions before you remove the accounts.
- Remove Group Memberships: If an account is disabled, it can still show up in access reviews and create problems in the configuration.
- Set Expiry Policies: Assign expiration dates to temporary users or contractors, so that their accounts shut down automatically after the fixed period
- Use Role-Based Access Controls: Even if someone accesses an old account, roles can limit the amount of harm done.
- Document Everything: Monitor the activity of users and note when a user turns something off, why and the time it occurred. Records that are good save confusion and show you were careful when doing work.
How Lepide Helps
The Lepide Active Directory Cleanup solution helps organizations effectively detect, manage, and clean up inactive user and computer accounts that pose a serious security risk. It continuously monitors AD environments to identify inactive accounts based on customizable inactivity thresholds, like users or devices that haven’t logged in for 30, 60, or 90+ days. Once identified, it provides detailed reports showing last logon times, account status, group memberships, and permission levels, allowing IT teams to prioritize which accounts to disable, review, or remove. This visibility removes the guesswork from AD clean-up and ensures that inactive accounts no longer go unnoticed or unmanaged.
Besides spotting threats, the solution helps follow best security practices by setting up policies for automatic clean-up tasks. For instance, it can automatically deactivate inactive accounts, remove users from additional groups, or set dates when temporary users will be cleared out, thus helping to avoid account overload. It sends you alerts when there is an unexpected change in activity, giving you a heads-up about possible threats. By using the platform’s built-in features for reporting, auditing, and automation, the chances of old accounts being exploited are much lower, and IT workloads are significantly reduced.
And if you’re just starting to evaluate your AD hygiene posture, we highly recommend reading The State of Active Directory Security. It’s a free guide packed with insights on common AD risks, including inactive users, and how to fix them.