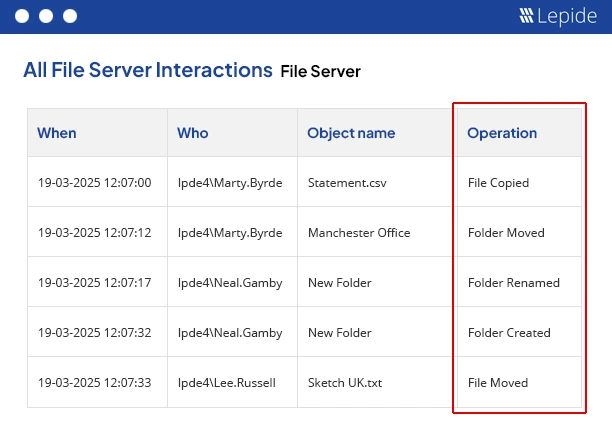
Open shares are among the simplest paths that attackers and insiders can use to gain access to your sensitive data. However, the majority of organizations are not even aware of how many open shares they have and what they are giving users access to.
What Is the Open Share Problem?
An open share is a shared folder or directory that has been configured to allow access to anyone with network access to the server, or to a broad group of users. These shares may contain sensitive documents, payroll files, legal records, and customer data. This means that users may have full access to sensitive data without specific permissions. Often, the number of open shares a company has can grow unchecked (as they may be created for convenience or accidentally) and regular auditing without dedicated solutions is very difficult.
Why Open Shares Are Dangerous
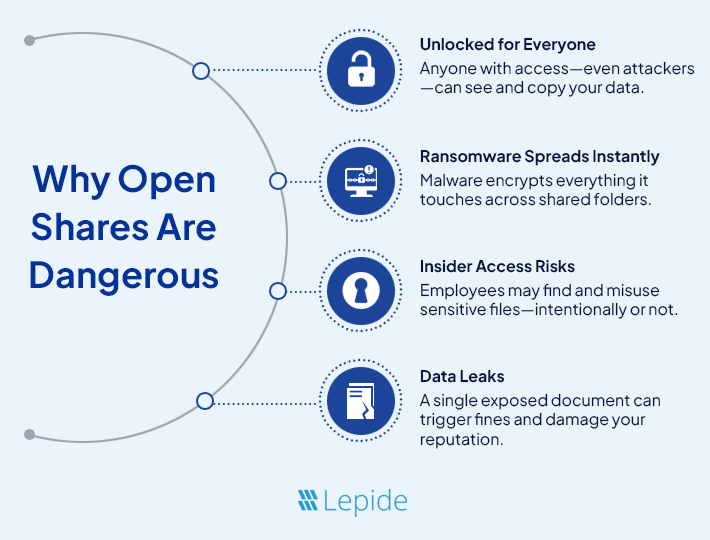
If an attacker compromises a user’s account, they gain access to everything the user can access. If that includes open shares, the attacker now has a way to steal or encrypt huge amounts of data, without raising alarms.
This is how ransomware spreads fast. Once it hits a user with access to many folders, it starts locking every file it can reach. Suddenly, a simple folder becomes the reason your business is offline.
Insiders can also cause damage. An employee might find sensitive documents by accident or on purpose. A single exported spreadsheet could break trust, expose customers, or lead to regulatory fines.
Why This Keeps Happening
Giving access is easy. Revoking it takes time. That’s the root of the problem.
Most open shares started as quick fixes. A team needed fast access. The project moved quickly. A manager wanted to avoid support tickets. So, someone gave broad access, just for now.
Then everyone forgot about it.
Without tools to track and review file share permissions, no one goes back to fix what’s already working. And as new people join teams, old access stays in place. The share lives on, growing bigger, more exposed, and more forgotten.
Eventually, it holds critical data. And too many people can see it.
What Can Go Wrong
Open shares may seem harmless on their own, but become a major risk when paired with a breach or even a curious employee. Once an intruder finds itself in your network, open shares are the first to be sought after. Open shares often contain documents like configuration files or internal documentation that can help attackers move laterally or escalate privileges.
What is worse, they are ideal for ransomware. Malware only needs access to a single user account. If that account has access to open shares, the malware can quickly spread and encrypt thousands of files.
In cases where data contained in open shares is regulated–such as financial information or health information–you may be subjected to major penalties. And when the internal personnel come across personal information in areas where it should not be found, this raises suspicion and human resource issues that cannot be easily resolved.
How Lepide Helps
The Lepide File Server Auditor is built to solve this exact problem by giving you visibility, control, and real-time protection over your file shares. It scans your file servers to detect open shares and tells you exactly who has access, how they got it, and when permissions were changed. You can pinpoint over-permissioned users and correct them before they become a threat.
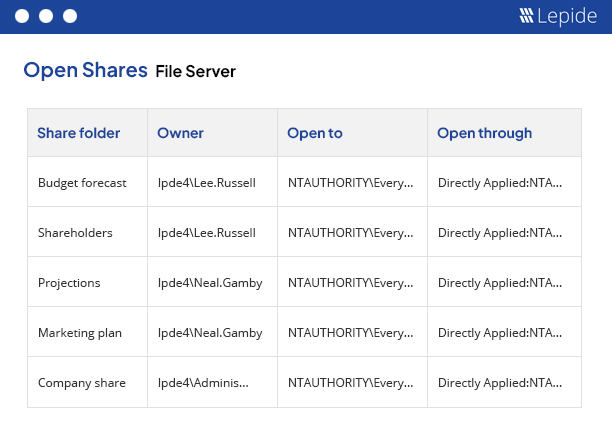
But Lepide doesn’t stop at detection. It helps you fix the problem. You can automate access reviews, assign data owners, and track permission changes as they happen. That means no more waiting for logs to catch up, and no more blind spots when incidents occur. It fits seamlessly into your existing environment. You don’t need to rip and replace. You don’t need to become a file system expert. You just need the right information at the right time, so you can act with confidence.
And because it works in real time, you’re notified the moment something changes. That gives you the power to stop threats before they spread, and to prove to auditors that your access controls are under control.
Open shares feel harmless until they aren’t. Until the wrong person gets access. Until a malware strain finds its way into an exposed folder. Until a compliance auditor asks, ‘Who else could see this?’
When you’re ready to fix the problem for good, Lepide is here to help. Sign up for the free trial or schedule a demo with one of our engineers today.