Group Policy is a powerful tool that empowers organizations to exert a high degree of control over their IT infrastructure. It is essential to follow best practices for Group Policy, which include recommendations for specific settings and guidelines for troubleshooting issues that may arise when working with Group Policy Objects (GPOs).
What are the Group Policy Best Practices?
Below is a list of best practices for group policies that will improve corporate productivity, IT efficiency, and security.
- Clear Naming Policy: Group Policy Objects (GPOs) must have a uniform and unambiguous naming system in order to be administered effectively in any Active Directory environment. For administrators to understand the objective, target group, and scope of each policy without having to open it, GPO names must be explicit. Whether a GPO is for users, computers, or a department, its name should clearly state its purpose and the people to whom it relates. When analyzing or making changes, this avoids misunderstandings, reduces mistakes, and saves time.
- Maintain Separate Organizational Units (OUs): An Organizational Unit (OU) is a container in which computers, users, and groups of the Microsoft Active Directory domain may reside. Group Policy deployment and troubleshooting are eased by having an effective OU infrastructure. Deployment of computer policy to all computers and user policy to all users becomes simple by organizing Active Directory users and machines into individual OUs. If an unknown individual or computer equipment appears in these folders, relocate it immediately to the proper OU.
- Setting GPOs at the OU Level: All objects within Active Directory in the domain will be governed by the GPOs defined at the domain level, so some settings will be applied to computers and users that are unauthorized. The Default Domain Policy is the only one that should be configured at the domain level. Rather, the OU level is where the GPOs should be deployed. There is no need to associate the policies with each sub OU since a sub OU will inherit the policies that were set on its parent OU.
- ‘Deny’ Permission to be avoided: An individual or group can be specifically excluded from a certain GPO by the administrators. This option can sometimes be applied in certain conditions, which can lead to unexpected outcomes since it is not necessarily clear that a GPO isn’t being applied to certain objects. To see which individuals or groups are blocked would require administrators to examine every GPO separately.
- Knowledge of GPO precedence: GPO Precedence determines what settings are applied in case of conflict and the order in which GPOs are applied. Since more recent policies might override earlier ones, how GPOs are dealt with in sequence is very significant. Domain (Group Policy settings that apply to all OUs within the domain), Site (Active Directory site settings are applied second), Local (Group Policy settings applied locally at the computer level have the lowest priority), and Organizational Unit (OU which last applied GPO settings) are the sequence in which GPOs are applied.
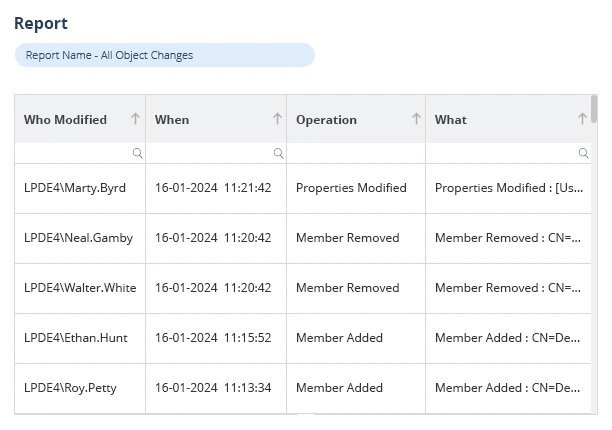
- Monitor and Auditing Group Policy changes: All changes should be carefully thought out and documented because GPO alterations have a significant impact on security, productivity, and compliance. Any significant changes to the group policy must be reported, and any changes must be monitored. To track Group policy changes, auditing should be enabled. Additionally, audit logs should be examined frequently to make sure modifications are approved and compliant with security guidelines.
- Avoid WMI Filters: Windows Active Directory employs a mechanism known as a WMI (Windows Management Instrumentation) filter to restrict the scope of Group Policy Objects (GPOs). It allows managers to address specific machines based on attributes like installed software, hardware type, or operating system version. Administrators can ensure that GPOs are applied only to the right machines and not to all computers within a domain using WMI searches. There are a number of WMI classes where you can define virtually any machine or user configuration. Applying too many WMI filters, however, will slow down logins by users and create a bad user experience. Since security filters consume less resources, use them wherever you can. Attempt to utilize GPO security filters instead of WMI filters. The groups, computers, or users who are targeted for GPO settings are controlled through security filters. Authenticated Users is the default scope of every policy, covering all authenticated users within the OU.
- Loopback Processing to be used specifically: Group Policy’s loopback processing configuration setting allows machines to receive user-specific settings from Group Policy Objects (GPOs) applied to them regardless of the signed-in user. This means that, instead of utilizing their own user settings, any user who logs into a particular computer will receive the same user settings applied based on the GPOs linked to that computer. User settings are limited by loopback processing to the computer on which the GPO is implemented. Loopback processing is commonly used when there are certain settings that need to be enforced when users log onto particular terminal servers. The OU with the servers will need a GPO established, loopback processing enabled, and the GPO applied.
- Utilizing Advanced Group Policy Management: Microsoft’s Advanced Group Policy Management (AGPM) provides for much closer management of GPOs. Moreover, it provides the option of reverting back to a previous version of GPO if the change is causing problems.AGPM, a component of the Microsoft desktop optimization pack, expands the usefulness of native Group Policy Object (GPO) management by adding features like version control, change tracking, role-based administration, and approval workflows. Businesses who use AGPM should evaluate the risks, weigh their options, and make plans for the future of Group Policy management in the quickly changing IT environment.
What are Common GPO Settings Best Practices?
The recommended practices listed below will assist in configuring GPOs to guarantee robust security and efficiency.
- Don’t change Default Domain Policy: It is one of GPO settings’ best practices. The default Domain Policy is to be used only for account, password, and Kerberos policy settings since it affects all computers and users within the domain. The Audit Policy and the User Rights Assignment Policy alone must use the default Domain Controller policy. It is recommended that even in the case of the above policies, separate GPOs be utilized even more efficiently.
- No Removable Media: Removable devices are called storage devices because they are easy to put in and remove from a running computer. Enabling users to connect removable devices to their PCs exposes your whole network to viruses and malware. Hackers may also easily extract plenty of data from removable devices.These devices are designed to be carried around and facilitate the sharing of data among different systems or devices. Malware spreads over the network when an infected drive is plugged into your computer. Such disks also provide a channel for data exfiltration. Removable drives can be prevented from being used through the “Prevention installation of removable devices” policy.
- Preventing Access to Command Prompt: Windows’ command prompt is where you execute commands that perform complex administrative functions. But if the command prompt falls into the hands of evil users, it can be used to compromise system integrity. A text-based user interface for an operating system’s input box is referred to as a command prompt. Though it is found to be an extremely useful resource for system administrators, allowing users to run commands may adversely affect your network. It is hence recommended to disable the control panel access for general users. The “Prevent access to the Command Prompt” policy is one method to do this.
- Group Policy Settings Reinforcement: Passwords are not required for users to access a Windows system with an integrated guest account. Using this login, malicious actors can gain access to your resources by pretending to be visitors to your domain controllers and servers. By default, guest account settings are deactivated, but hackers can easily change them to cause havoc on your network. Attempts by malevolent actors are prevented by the Guest Account status policy.
- Enforcing Password Best Practices: Standards organizations like NIST offer guidelines for password policy settings that reduce the vulnerability for credential reuse and password-based attacks. These can be applied in the environment through the Group Policy. Confirm that the stringent requirements for items like password length and complexity enhance security. In order to circumvent the hassle of account lockout, users can instead resort to the use of insecure measures like writing down their passwords due to such policies.
- Renaming Local Administrator Account: A local administrator account is a highly privileged account that has total control over a computer. It can install software, view system settings, and use other local resources. Because this account grants privileged access to the computer, attackers are particularly interested in it. It is advised to rename the Local Administrator account to reduce their danger. Additionally, only utilize the account when necessary; for routine chores, use reduced-privilege administrative accounts.
- PowerShell to be Blocked: The cross-platform task automation and configuration management tool called Powershell consists of a command-line shell and associated scripting language. Business users do not require Powershell, thus denying them access to it can prevent harmful scripts from executing. On domain-joined computers, Powershell use can be blocked by using Group Policy. It is possible to exempt the administrators who need to use Powershell from the policy. For added protection, the powershell scripts can also be limited to execution on a particular computer.
- Restricting Membership: Members of the Local Administrators group can change security settings, remove system files, and install software. Increased risk of malware infection, inadvertent and deliberate data loss, system instability, and performance deterioration are all possible outcomes of these accesses. Unwanted accounts may be removed from the Local Administrators Group on all PCs by restricting group membership in the group policy.
How Does Lepide Change Reporter (Free Tool) Help?
Lepide Change Reporter for Active Directory (Free Tool) provides cutting-edge Active Directory and Group policy monitoring and auditing features that support organizations in tracking changes and identifying unauthorized changes in addition to security policy compliance breaches. It facilitates IT teams to impose Group Policy control while avoiding security attacks.