Last Updated on December 11, 2024 by Satyendra

What is a Data Protection Strategy?
It would not be an overstatement to call data the life and blood of a business. As it flows through multiple systems and apps to drive innovation and decision-making. However, just as blood must be kept safe within the body, your data must be maintained to ensure its integrity, confidentiality, and availability. A data protection plan is a complete framework for managing and securing an organization’s data assets from risks, breaches, and loss.
A data protection strategy caters to the collection, storage, processing, and security of data. It includes not only technical protections, such as encryption and access controls. It also involves organizational rules and procedures that govern how employees handle sensitive information. As organizations increasingly rely on digital platforms, a strong data protection plan has become extremely important for organizations.
Why is a Data Protection Strategy Important?
Since we have learned that cyber threats are improving and constantly targeting businesses and organizations, companies and organisations are at risk if they do not take measures against cyber threats. Business of any size and type including start up ventures and large international corporations are vulnerable to data breaches.
But wait, IT is not only about stopping hackers from getting in. Data privacy and compliance appear strict where the GDPR, CCPA, HIPAA are in practice. If enterprises do not adhere to these standards, they and their officers can face massive penalties and possible legal action, apart from immediate business reputational loss. In addition to the statutory control, customers look for responsibility. People want to know that their data is being processed with as much care as they would like their personal data to be processed with.
In other words, the consequences of the organization having an inadequate or a partial plan for data protection may be dire. Since 2023, more than 60% of the companies face a compliance incident at least once, and the aggregate cost per breach for a company in 2024 is $5.17 million, as per IBM’s
Cost of Data Breach Report Apart from the monetary damage, companies have to rebuild consumers’ confidence and break the negative perception of their partners. This may require few months or few years.
Thus, protective measures are important constituents to building dependable trustworthy brand out of a company’s data. It allows firms to build, grow or scale as they wish without the disturbing factor of a violation or the endangerment of the firm’s reputation.
Important Elements of a Data Protection Strategy
Data protection strategy is created by several factors that are interrelated in their implementation process. All of them are designed to solve one or another aspect of data protection and readiness for use. The following are a few to consider:
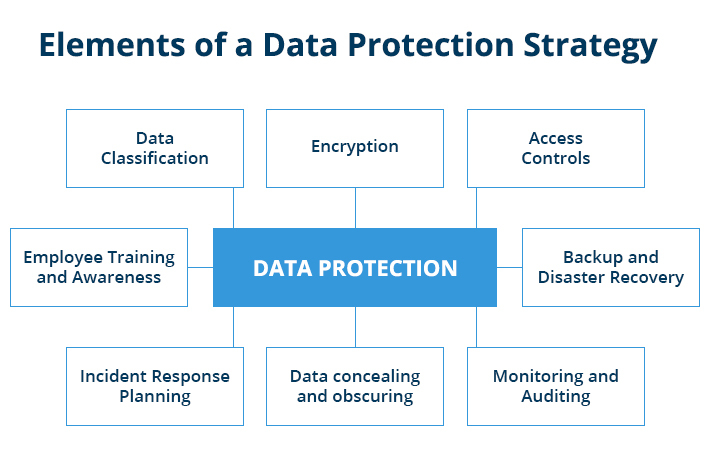
1. Data Classification
First, in order to protect data you need to identify what data is held and its’ classification, or the risk factor. This can be achieved by proper classification of data. Data classification means sorting of the information as a function of relevance, security, and regulatory status. This process enables one to allocate the right security controls, for different types of information. It also assists you to do so using better protection of highly sensitive information.
2. Encryption
Encryption is one of the most crucial strategies in safeguarding information that can be stored and transmitted. It scrambles data and only a few people with the right decryption codes are able to view the actual data. Securing all the important systems, databases and communication is crucial to avoid the compromise of data to unauthorized or unwanted clients or users.
3. Access Controls
Effective and secure approaches to the access control guarantee that only the appropriate persons will have a possibility to read, modify, or provide access to secure information. A few critical inherent components that prevent access based on job descriptions and the principle of MFA are RBAC, least privilege policies.
4. Backup and Disaster Recovery
These spill overs also include regular backups to ensure data can be recovered in case it is deleted by accident, corrupted or in the worst-case scenario, is held hostage by a ransomware program. Disaster recovery mechanism is a component of a robust data protection framework and defines how data can be recovered as well as business operations in case of disruption. This involves having additional backups off-site, and in the cloud.
5. Monitoring and Auditing
The use of a data access and utilization audit and surveillance approach is critical to identifying potential risks continually and appropriately managing them. Besides, any specific access pattern or data transfer that is rarely observed should also send an alert so that the security team can acts immediately.
6. Data concealing and obscuring
Personal data protection at organizations involve data masking, anonymization and encryption of PII and other sensitive data. The process of data masking hides actual information while making it still functional to the analyst or the tester. Deidentification completely removes identifiers from data sets and their removal cannot be reversed to point to specific identity figures.
7. Incident Response Planning
It remains still to be agreed that among all the risks to information assurance, human error is probably one of the biggest. Every employee must be periodically refreshed on data protection and security protocols, phishing, and secure data processing. Cybersecurity begins with an informed staff because the average member of a company can remind management of it at any given time.
8. Employee Training and Awareness
It might sound silly but there is almost always a chance to breach something even if it has A+ security for example. Thus, it is crucial to have an incident response plan on board since such incidents are not renovated to happen. It prescribes the actions to be taken once there has been a security incident. For example, managing the anger, dealing with the cause and recovery from the anger. Strategic response plan can effectively reduce the magnitude at which a breach impacts your company.
Best Practices for an Effective Data Protection Strategy
Providing a data protection plan meets the need that is over and above just using the best available security solution, it requires a well thought out plan. An approach that establishes its framework on the existing standards in the industry.
1. Take a zero-trust approach
Zero trust security requires that threats are inside and outside your organization’s network, so nothing is trusted. The user access requests are carefully examined through a number of control checks to ensure the least probability of internal threats and illegitimate access.
2. Consider risk assessments at least annually
A word of advice is that cybersecurity is not a one-time area to specialize in, after that, you are set for life; that means, it is always important to assess the efficiency of your data protection strategy. Continuous risk evaluations help you identify new risks as well as vulnerabilities and make changes to your policies and technologies.
3. Automate Data Protection Tasks
As many activities as possible of the administrative tasks for the backups, the patching, and monitoring should be done in an automated way to minimize changes made by a human touch. This is because you can be able to respond to possible security incidents much faster and with so much precision.
4. Capitalize on fresh software and systems
Most cyber-attacks occur as a result of a flawed application in an outdated system. Constant patching and updates also limit the impact of threats already in your technology systems because there is a reduced chance of being exploited.
5. Implement Strong Data Access Governance
Data access governance is a framework of rules together with procedures that determine how the access to the data should be managed and protected through its life cycle. Strong data access governance then guarantees full control over the access rights to its data from the time it is gathered to the time it is disposed of.
6. Frequently Test your backup and recovery plan
Merely retaining a backup is not sufficient, which is why the backup should be tested often so you can be sure that the disaster recovery process will occur as quickly as possible when a breach or some other calamity occurs. The process also shows you any weaknesses that you may be having in your recovery methods, hence solve them before they become a problem.
How Lepide Helps
Lepide Data Security Platform enhances data protection by providing solutions for data classification, real-time monitoring, access control, and compliance reporting. It helps classify sensitive data across file servers, databases, and the cloud to ensure necessary safeguards. The platform monitors file changes and user activities in real-time, raising alerts for any suspicious actions. Lepide also manages access control by tracking who has access to what data and enforcing role-based restrictions. Additionally, it generates comprehensive audit and compliance reports to support organizations in meeting regulatory requirements like GDPR, HIPAA, and SOX.
Conclusion
Implementing an ideal data protection strategy is about keeping the organizational culture accountable and trustworthy within your company. A preventive and strategic approach may achieve more than keeping your business away from threats. It can give you the comfort of knowing that your most valuable asset, i.e., data, is secure. When security becomes part and parcel of your operations, security becomes an ingrained culture that fosters security awareness whereby each individual is aware of his or her security responsibilities.
Business development is founded in trust. When you are building on your data protection plan, remember it is not just about being safe; it is about building a lead, about turning security into an Edge that defines your business.
To learn more about how Lepide can assist you in enhancing your Data Protection Strategy, schedule a demo with one of our engineers, today.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
