Last Updated on March 5, 2025 by Satyendra

In an IT environment, privileged user accounts are those which are provided comparatively more privileges or permissions than a normal user account. Any malicious activity conducted, either intentionally or mistakenly, by a privileged account can be a threat to IT security. To address this, a systematic way of determining which users have privileged access and tracking their activities is required.
Methods to Identify Privileged Users
Follow these methods to identify privileged user accounts so that you can prepare a strategy to audit their activities more easily.
1. Members of Privileged Groups
Active Directory has built-in privileged groups for privileged accounts; this is an obvious place to start. These groups are; “Administrators”, “Domain Admins”, “Enterprise Admins”, “Schema Admins”, “DnsAdmins” and “Group Policy Creator Owners”. Other places to look are Local Administrator Groups on client systems.
A few of the built-in privileged groups can be located in the “Built-in” container, while others are in the “Users” container. The “DS Restore Mode Administrator” privileged account is not stored in Active Directory.
To identify members of the built-in Active Directory privileged groups, do the following:
- Open “Active Directory Users & Computers” on the Domain Controller.
- Select the “Built-in” container, right-click on any of the above groups in the right pane, and open its “Properties” windows.
- Go to the “Members” tab; there you will see all members of this group. All are privileged users.
Note: If you are looking into a group in the “Users” container, you will have to select that group in the right pane and right-click on it in step 2.
In the following image, you can see privileged user accounts in the “Administrators” group:
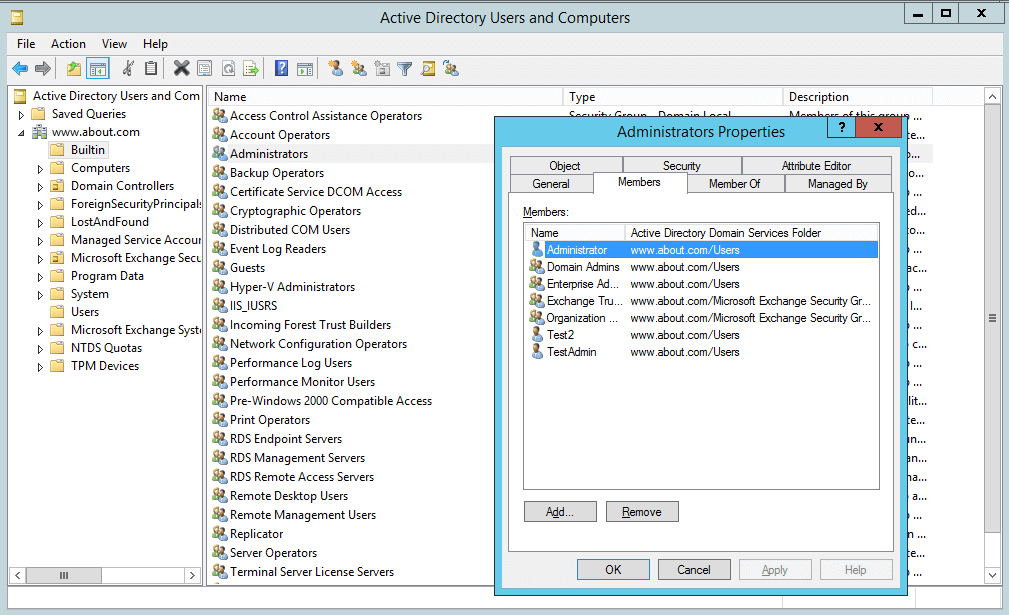 Figure 1: Privileged users in the Administrators group
Figure 1: Privileged users in the Administrators group
In our case, as you can see in the above image (Figure 1), the “Administrators” group has many other groups as members. They, in turn, may have other groups as members and so on. The users who are members of such groups are also privileged users. By navigating through nested members, you will uncover the complete list of group members.
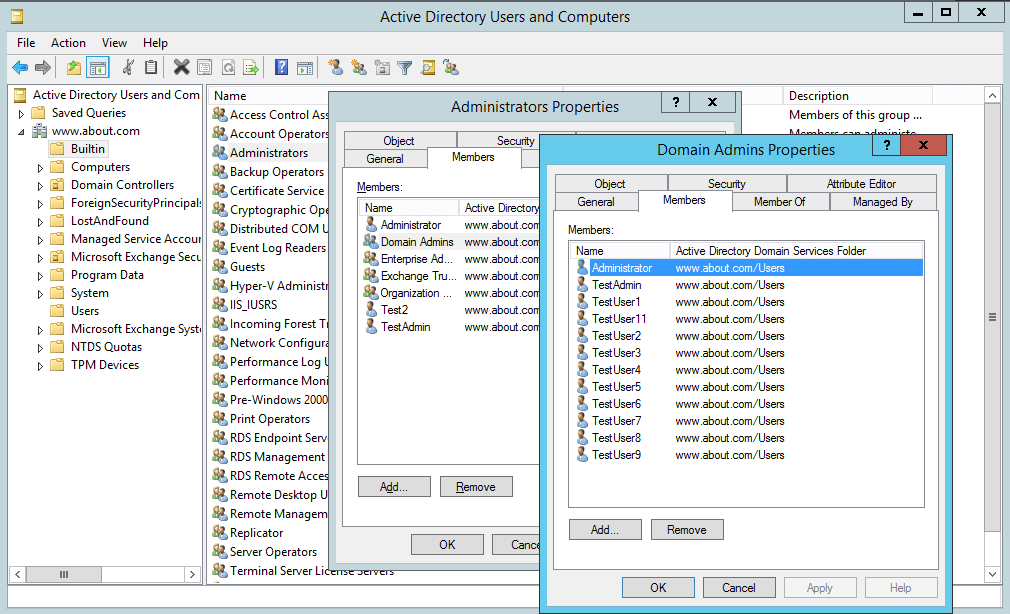 Figure 2: Privileged users in nested groups
Figure 2: Privileged users in nested groups
2. Privileges to Administer Organizational Units
Permissions in parent OUs spread down to child organizational units, groups, users, and other objects. So, if a user has been provided full control on an organizational unit, that user has privileges equal to an administrator. For example, if User1 is given “Full Control” on “Users” (a default Organizational Unit), then User1 has more privileges than a Domain Administrator.
If “Everyone” has full control of the root “Built-in”, it means that every user in your IT infrastructure has domain administrative privileges.
To see permissions on an Organizational Unit, do the following:
- Open “Active Directory Users and Computers”.
- Go to any Organizational Units whose permissions want to see.
- Right-click to open the “Properties” window, and select the “Security” tab.
- Click “Advanced” to see all the permissions in detail.
The following image shows the list of users and objects who have delegated permissions on the “Users” object:
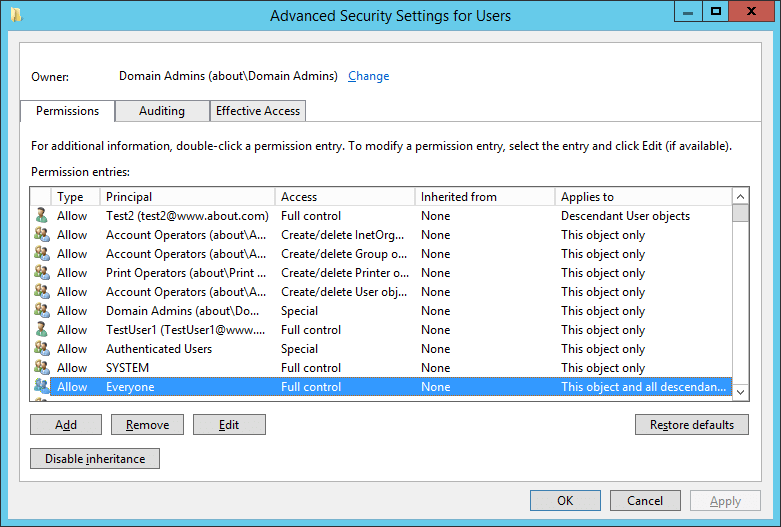 Figure 3: Users with Delegated Permissions on OU
Figure 3: Users with Delegated Permissions on OU
In this image, the “Test2” user and “Everyone’ has full control of the “Users” Organizational Unit, the default container. Similarly, you can check permissions on all organizational units and prepare a list of users who have delegated permissions to them.
3. Local Admin or other Users with privileges assigned from GPO
Instead of having direct privileged access within Active Directory, there are some accounts that receive administrative privileges. If a user has access to the Local Administrator account of a Domain Controller then that user has rights equivalent to a Domain Administrator.
Outside Active Directory, there can be users who have been provided Admin-like privileges through Group Policy Objects. Any privileged user or administrator can modify “Computer Configuration” “Policies” “Windows Settings” “Security Settings” “Local Policies” and “User Rights Assignment” to provide administrative privileges to other users.
There are third-party PowerShell scripts available on Technet and other Websites, which can provide you with a list of users with their rights. It is recommended to use a script only from a trusted source.
4. Users who have password reset authority over other users
Another type of privileged user is one that has the authority to reset other users’ passwords. There are some applications that let a user delegate password resets to another user. If the password reset permission is delegated through Active Directory, you have to browse the permissions of a user account to check which other users have the permission to reset the password.
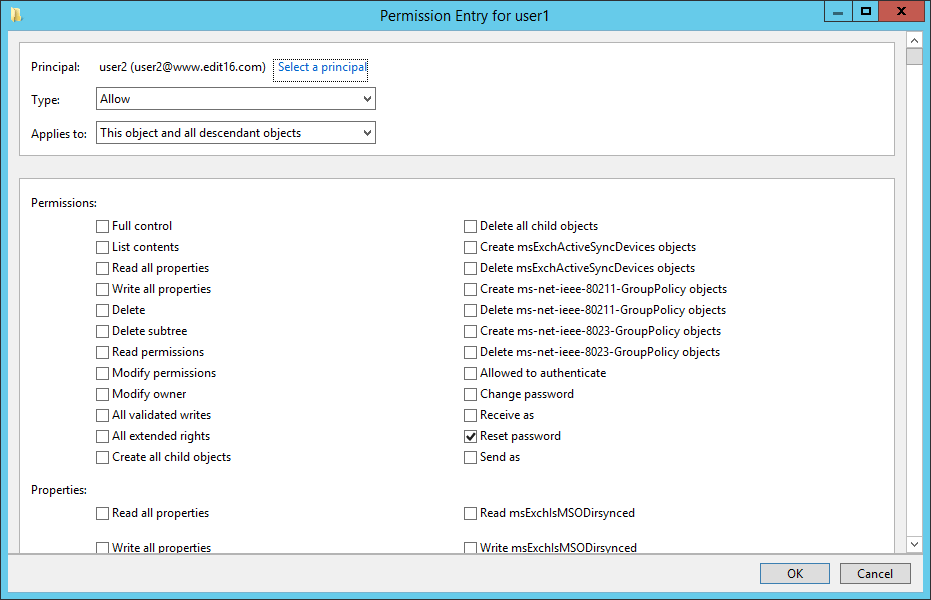 Figure 4: User with “Reset Password Permission”
Figure 4: User with “Reset Password Permission”
In this image, “User2” has “Reset Password” permission on “User1”. It means “User2” can reset a password on behalf of “User1”.
If you are using a software program to reset passwords, generate periodical reports to show which users have permission to reset passwords.
5. Users who have knowledge of any privileged service account
Privileged service accounts, including those used for Exchange Server, SQL Server, and for creating backups, have some level of elevated privileges on the computers on which those accounts are used. So, if someone has knowledge of a privileged account’s credentials, that service account can be used maliciously. Domain controllers are at even more of a risk as an unauthorized user can get administrative access to a domain. To know if someone is misusing a service account you will have to audit the logon of each service account.
6. Users with write access to GPOs applied to Important Computers
Specific group policies can be created for any computer in the network. Such computer-related Group Policy Objects are crucial only for the domain controllers and for those computers that host server applications with domain-privileged access. If a user has privileges to write to such important GPOs, then that user account is also a privileged user.
Perform the following steps to list these users:
- Open the “Group Policy Management” console.
- Go to GPOs in the left pane.
- Select a GPO whose privileged users you want to see.
- Click on the “Delegation” tab in the right pane.
- There you can see all the privileged users who have to write access to GPOs with different permissions levels.
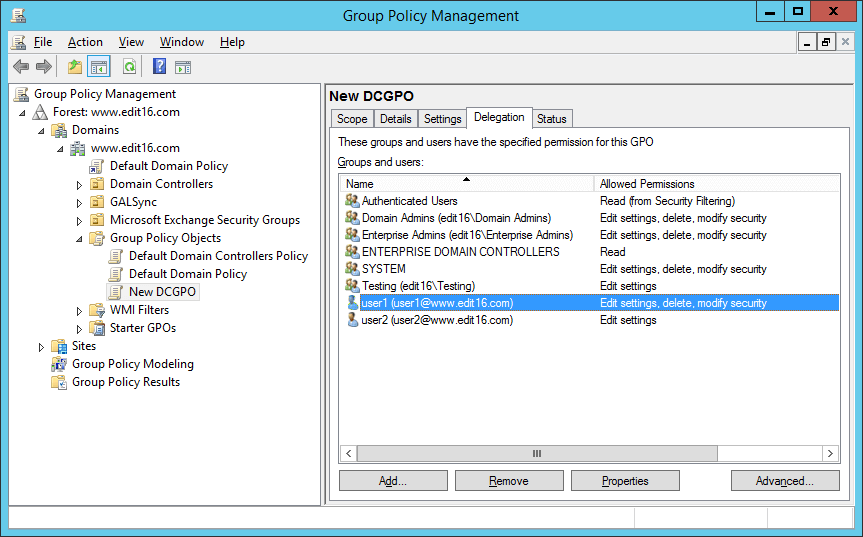 Figure 5: Users with write access to GPOs
Figure 5: Users with write access to GPOs
In this image, “User1” has “Edit settings, delete, modify security” rights and “User2” has “Edit settings” rights.
7. A user who have access to Active Directory Management Applications
Many organizations use third-party Active Directory management solutions to simplify and improve management tasks. These solutions either use a service or proxy account with privileged access to manage Active Directory or user accounts that are granted elevated privileges by some other means (such as membership in a built-in privileged group or OU-based permissions). Depending on the level of delegation, gaining control over an account like this one is just as good as being a Domain Admin.
To find out who has access to such accounts, you will have to enlist all relevant applications in the network, then identify all service or proxy accounts with privileged access that these applications are using. You can enable the “Audit Directory Service Access” group policy to monitor what these accounts are doing.
As far as misuse of the Active Directory management solution itself is concerned, you will have to ensure that it has a built-in audit trail to monitor inappropriate use.
8. Users who have admin-level access to virtual infrastructure
Users who manage virtual environments that host domain controllers or member servers have the same privileges as those with administrative access to desktops. For example, if you are managing Hyper-V, members of the Hyper-V Administrators local group have administrator-level access to the host operating system.
You should identify which accounts have privileged access to your virtual infrastructure, either by checking Local Admin groups on a given domain controller/server or by looking for privileged access within the virtual environment itself.
Related Articles:
Free Tool to Find Active Directory Privileged Users
Lepide’s Free tool to List AD Admin Users is designed to help organizations quickly identify users with administrative privileges within their Active Directory environment. This tool scans your Active Directory and provides a comprehensive list of all admin users, making it easier to understand who has elevated access. By investigating how these users obtained their permissions, administrators can spot excessive privileges and implement a zero-trust model to enhance security.
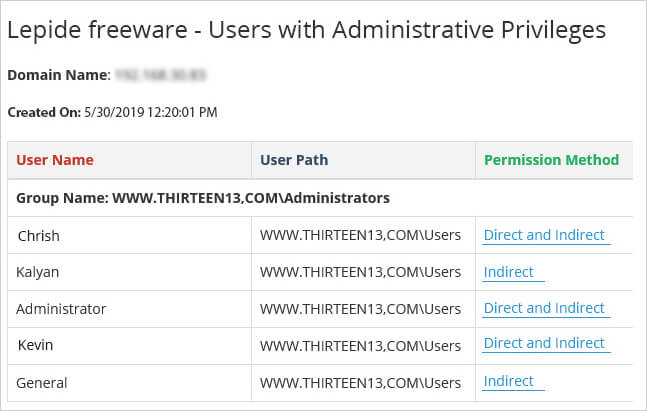
With its user-friendly interface and scalability, the Lepide List AD Admin Users Free Tool makes it easy to manage and secure your Active Directory environment. Plus, it’s completely free of charge with no expiry date or commitment required.
To discover the capabilities firsthand, download the Lepide List AD Admin Users Free Tool now.

 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
