
Active Directory (AD) is a database and set of services that connects users with the resources they need to do their work. It enables administrators to manage permissions and control access to network resources, specifying which users and computers are available and who’s allowed to do what.
Active Directory is a fundamental element of any Microsoft Windows environment and plays an essential part in authentication, access management, account management, and authorization. It is because of this that it’s crucial to engage in Active Directory auditing and reporting best practices.
What is Active Directory Auditing and Why it is Important?
Active Directory (AD) auditing refers to the process of monitoring and recording events related to the use of Microsoft’s Active Directory. Active Directory is a directory service used by many organizations to manage users, computers, and other resources on their network.
AD auditing involves collecting and analyzing data on activities such as user logins, changes to user accounts, modifications to group policies, and other actions performed within the Active Directory environment. This information is then used to identify potential security threats and ensure compliance with regulatory requirements.
Auditing is important for several reasons. Firstly, it helps to maintain the integrity of the Active Directory environment by detecting unauthorized access and changes to important system components. Secondly, it provides a valuable source of information for incident response and forensic investigations, enabling organizations to quickly identify and respond to security incidents.
Auditing Active Directory also helps organizations to comply with various regulatory requirements, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA), which mandate that organizations must have appropriate security controls in place to protect sensitive data.
How to Get Started with AD Auditing and Enable Auditing
By default, Active Directory does not audit all your security events. To start auditing, you must enable the auditing of any notable events to ensure your security event log tracks them.
When setting up AD auditing, you can use either basic or advanced security audit policy settings. However, Microsoft does not recommend using both. It is recommended that you use Advanced auditing if you are not currently performing any auditing.
- Basic policy settings are found under: Computer Configuration, Policies, Windows Settings, Security Settings, Local Policies, Audit Policy
- Advanced policy settings are found under: Computer Configuration, Policies, Windows Settings, Advanced Audit Policy Configuration, Audit Policies
Top 10 Events to Audit in Active Directory
The key to an effective AD audit is knowing which events to log. However, because organizations have different priorities and strategies, there is no definitive list of specific things you need to include in your Active Directory security auditing. If too many events are tracked, your logs will get so full that they’ll be hard to analyze and they’ll overwrite themselves quickly. But if you fail to track critical events, you’ll be unable to detect malicious activity and investigate security incidents. The main goal is to identify events that could be a threat to your organization, which means watching for activities that could have serious repercussions, actions that fall outside of your normal working patterns or behavior that violates your established policies.
Here are some of the key events to include in your Active Directory audit:
1. Object Access/Modifications
Undetected and unauthorized changes to object attributes increase the likelihood of your environment being compromised.
2. Group Policy Changes
A single, unauthorized change to a Group Policy object (GPO) can lead to security incidents and violations of data privacy mandates. For example, this could be by allowing unlimited attempts to guess an account password.
3. Security Permissions and Access Rights, Permissions Changes
Privileged users who exploit access permissions can accidentally or deliberately cause serious damage to your organization.
4. Password Resets and Changes
Attackers may be able to steal data and do serious harm if they manage to infiltrate an account in your Active Directory by guessing a password. So strict password policies should be implemented, and password modification attempts audited.
5. Logon Events
Tracking user logon/logoff activity is essential for both security and compliance. Logoff patterns that break from the norm can indicate suspicious activity.
6. Privileged User Activities
Privileged users are often responsible for weaknesses in your Active Directory security, intentionally or otherwise, so it is essential for the activities of these users to be traceable and carefully monitored.
7. Account Lockouts
User account lockouts can bring critical business processes to a halt. In addition, IT teams often overlook the fact that a surge in account lockouts can be a sign of a brute-force attack on your network.
8. Inactive or Obsolete Accounts
Dormant user and computer accounts are open invitations for hackers to gain access to your systems and data but often accumulate unnoticed.
9. Ownership and Audit Settings of Objects
Ownership monitoring is one of the most important Active Directory auditing best practices. To maintain control over the entire network, security restrictions, and access control of objects need to be maintained.
10. Securing Schema Configurations
Ensuring schema configuration security is critical. Securing your network data and assets will help prevent insider abuse and data leakages.
AD Auditing Best Practices
These best practices can help make your AD security auditing more effective:
- Determine the scope of your audit: Before starting your audit, it’s important to define the scope of what you want to audit. This could include specific domains, objects, or events that you want to monitor.
- Enable auditing: To audit Active Directory, you need to enable auditing on the appropriate objects and events. This can be done using the Group Policy Management Console or PowerShell.
- Monitor event logs: Regularly monitor the event logs for any unusual or suspicious activity. This can help you detect potential security threats or compliance issues.
- Collect and store audit data: Ensure that you have a process in place for collecting and storing audit data. This can include using centralized logging or third-party tools to help manage and analyze the data.
- Review audit data regularly: Regularly review audit data to identify any issues or potential risks. This can help you proactively address security concerns before they become more serious.
- Use alerts and notifications: Configure alerts and notifications to alert you to any unusual activity or potential security threats. This can help you quickly respond to security incidents.
- Use role-based access control: Implement role-based access control (RBAC) to restrict access to sensitive areas of Active Directory. This can help reduce the risk of insider threats and unauthorized access.
- Limit privileges: Limit the number of accounts that have administrative privileges in Active Directory. This can help reduce the risk of privilege abuse or credential theft.
- Regularly review user accounts: Regularly review user accounts to ensure that they are still needed and that their permissions are appropriate. This can help reduce the risk of inactive or rogue accounts.
- Perform regular security assessments: Perform regular security assessments to identify any gaps or weaknesses in your Active Directory environment. This can help you proactively address potential security risks.
Drawbacks of Native Active Directory Auditing
Microsoft does have some auditing capabilities for Active Directory, but they have several limitations which are described as follows:
- Audit logs are decentralized so to get an accurate picture of AD activity, administrators must analyze the security event log on each domain controller where auditing is enabled.
- Audit logs are incomplete. Critical aspects of Active Directory, such as Group Policy, are either partially audited or not audited at all.
- The log data can be noisy and hard to interpret. Events often contain irrelevant or difficult-to-understand information, plus a single audited event can generate multiple events in the log.
- Log data can be overwritten. Directory auditing information is written into the security event log, which is highly active and regularly overwritten.
- The Event Viewer is limited. You can filter the events, but only by certain set criteria.
How Lepide helps with Active Directory Auditing
An alternative to the time-consuming native method of AD Auditing is to use the Lepide Auditor for Active Directory. This Active Directory auditing software provides a straightforward and comprehensive approach to auditing your Active Directory and overcomes the limitations of native auditing.
Below are some examples of how the integrated reports from Lepide can be used to facilitate your Active Directory auditing:
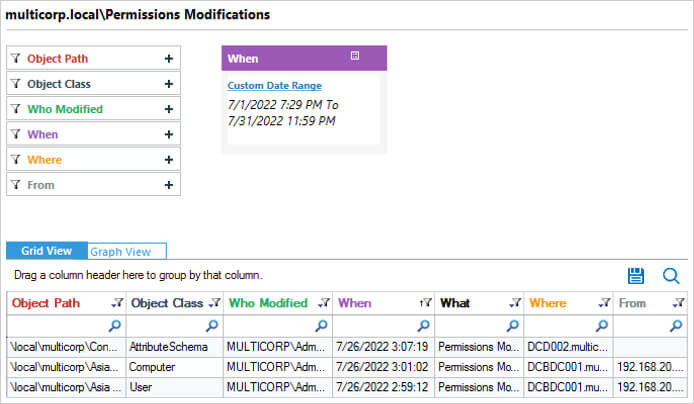
Security Permissions Modifications: This report shows all changes to permissions for the specified date range. The report can be filtered, grouped, saved, and exported.
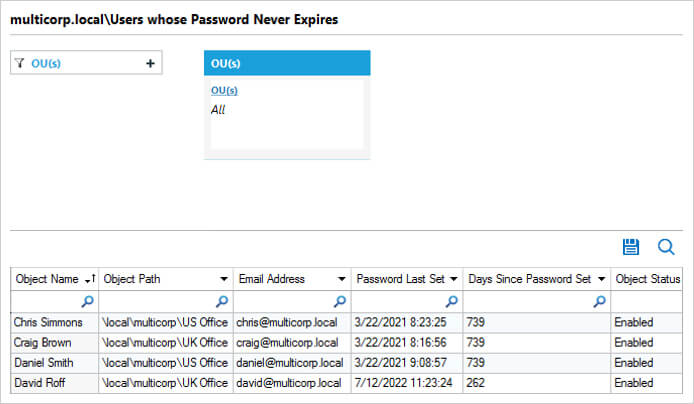
Password Set to Never Expire: This report shows all users whose password is set to never expire. The report can be filtered, grouped, saved, and exported.

 Important Group Policy Settings & Best Practices to Prevent Security Breaches
Important Group Policy Settings & Best Practices to Prevent Security Breaches 15 Most Common Cyber Attack Types and How to Prevent Them
15 Most Common Cyber Attack Types and How to Prevent Them Why Active Directory Account Getting Locked Out Frequently – Causes
Why Active Directory Account Getting Locked Out Frequently – Causes
