Here’s where we will focus.
Our risk assessment process is completely free and turnkey, so you can just sit back and relax as our engineers do all the heavy lifting. As part of our risk assessment process, we will assess the following key areas of your data security:
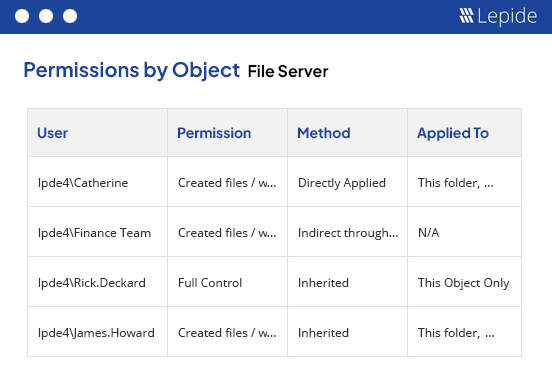
Analyze current permissions and permission changes.
We will determine how many of your users currently have privileged access and the number of permission changes you are seeing so that you can spot over privileged users and prevent privilege abuse.
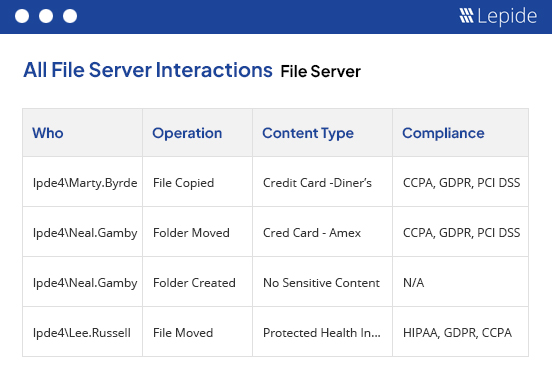
Assessment of changes being made to your data.
We will see whether your users are behaving in a “normal” way when it comes to your data and determine how many anomalies are happening. Spot the signs of a data breach in progress.
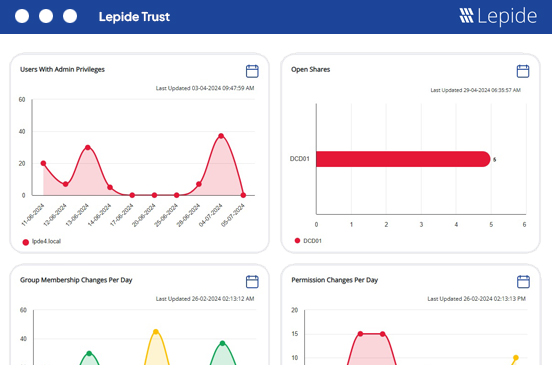
Overview of your environment states and changes.
We can show you whether your environment is posing a risk to your data. Our report will show you how many open shares, stale users and data you have that can be cleaned up to improve security.