Privileged Access Management Solution
Fortify security, control privileges, and streamline compliance with our cutting-edge privileged access management tool.














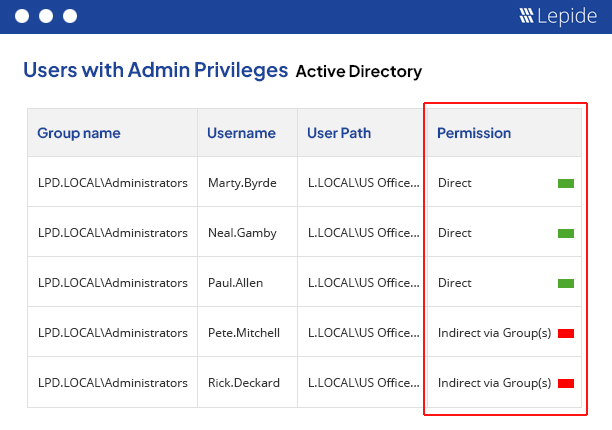
Gain complete visibility into who holds privileged access within your organization. See who your users with administrative privileges are and how they are getting those permissions. With Lepide, you can also identify users that have excessive permissions based on their data usage patterns; leveling up your privileged access management efforts.
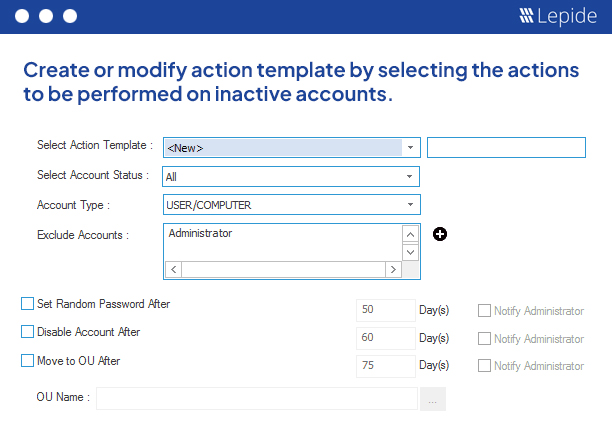
If your AD is unclean, then your whole privileged access management solution will struggle. To help you assess and clean-up your Active Directory, Lepide can help you identify your inactive users/computers, open shares troublesome accounts, legacy issues with users, passwords that never expire, over-privileged users and more.
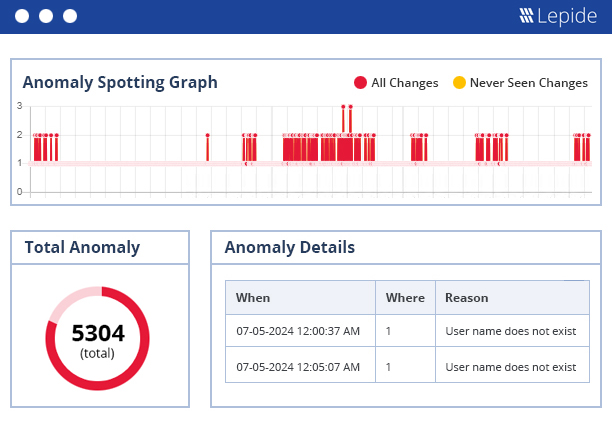
With the Lepide Privileged Access Management solution, you can identify how many privileged users you have, get real time alerts for anomalous user behavior, and monitor their interactions with sensitive data. You can also audit logon/logoff activity and password resets. All this ensures that you fully understand the behavior and hierarchy of your privileged users.
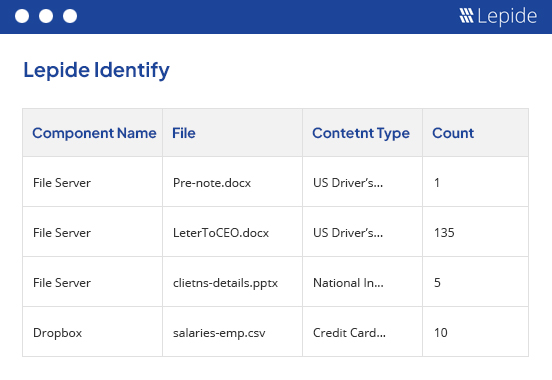
The Lepide Privileged Access Management solution will help you understand where your sensitive data is and why it is sensitive. This is important as it will help you determine which of your users should be able to access the data. The solution will also spot trend in behavior around interactions with this data and identify excessive permissions.
In this webinar, we’ll demystify the principle of least privilege and demonstrate how to implement it effectively to protect your sensitive data.
View recording