Quickly and Easily Reduce Risk to Your Data and Systems
Instantly identify and reduce risk to your most sensitive data and critical infrastructure through visibility over privileged users and over exposed data.














Implement key monitoring, reporting and alerting capabilities to instantly identify areas of risk and improve current security states. Ensure that you are able to keep your Active Directory clean, rotate passwords regularly to prevent credential theft, implement zero trust, react to human error, and more.
Instantly reduce your potential attack surface by ensuring that your users have appropriate access as they join, leave and move in your organization
Identify who your most privileged users are and what sensitive data they have access to. See what changes they are making and revoke access if needed.
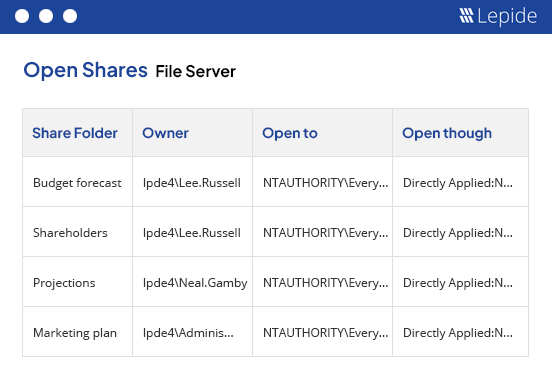
Instantly generate a report of open shares (data open to everyone) and revoke access so that your sensitive data isn’t over-exposed and at risk.
A vast majority of security issues originate with human error – most commonly admin level changes to your critical systems.
Undetected changes to critical security groups or group policy, if unchecked, can cause unprecedented damage to your security efforts.
Lepide ensures you can implement security by design by enabling you to keep track of changes made to critical systems.
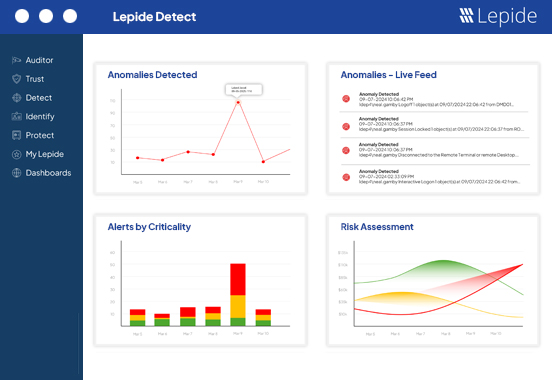
If you are the unfortunate victim of a ransomware attack, you will want to make sure you can mitigate the damage by limiting the data that is at risk.
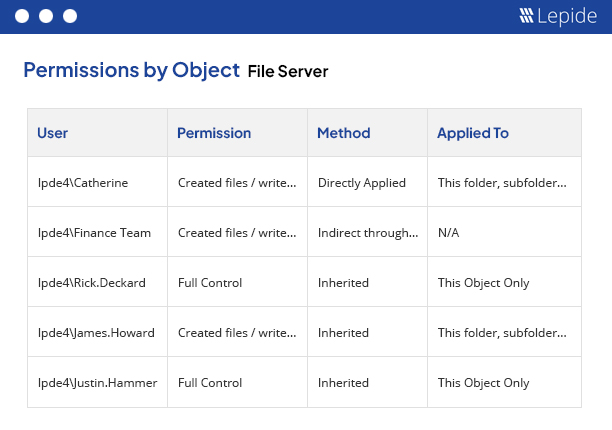
Ensuring you know who has access to your most sensitive data and whether this access is appropriate or excessive is a critical part of the process.
We give you a simple, yet comprehensive way to see exactly what your users have access to and how the access was granted. Enabling you to take the right decisions for your permissions.
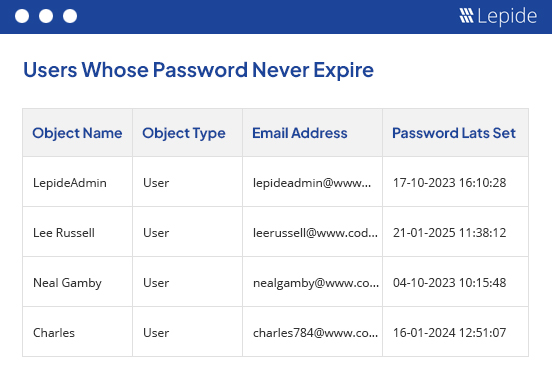
44% of all threats come from credential theft and yet most people still don’t rotate their passwords regularly.
One of the biggest threats to the security of your business is with users whose passwords never expire.
Using Lepide you’re able to see who these people are and automatically notify them to remind them to reset their passwords.
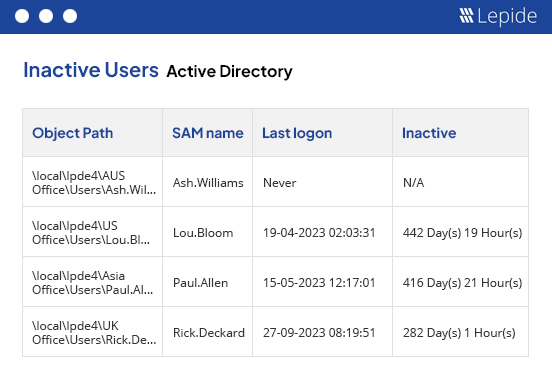
Ensure that you can maintain a clean Active Directory as users join, leave and move throughout your organization.
Revoke access to ex-employees and third parties that you no longer work with to prevent inappropriate access to company resources.
Generate a list of inactive user accounts so that you can take action and reduce your overall attack surface.
Sometimes the biggest threats to your organization come from within. Your Admins hold the keys to your kingdom, so it’s vital that you ensure you are monitoring their activity.
Stories of rogue admins or even admins simply sharing their credentials with other team members are all too common.
Lepide will help you understand what privileges your admins have and at what level so that you can implement a policy of least privilege.
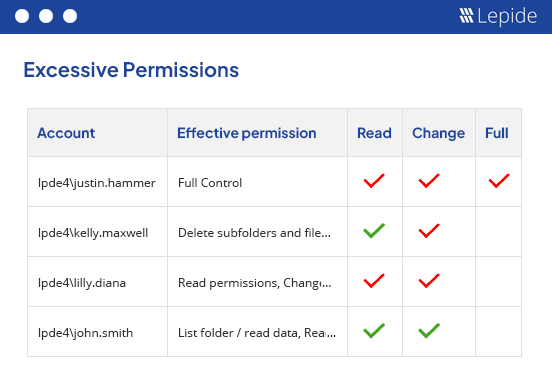
Over-exposure of sensitive data is one of the leading causes of data breaches and security incidents.
Making sure you manage data sprawl is critical in keeping your most sensitive data secure and reducing your potential attack surface.
We help you locate sensitive data in at risk locations, such as ‘open shares’, to enable you to remediate and secure it – reducing your attack surface in the process.
By following the guidelines outlined in this paper, your organization can establish a robust data access governance program that supports its business objectives and protects your valuable data assets.
Get the free guide now!