File Activity Monitoring Software
Track how users are accessing, moving, deleting your sensitive files across Windows File Servers.














Easily monitor file activity on your Windows File Servers and get the vital who, what, when and where audit information in a single pane of glass with easy-to-read reports.
Audit and monitor file activity in real time with a detailed audit trail of all changes and interactions with sensitive data.
Detect and respond to anomalous file activity, such as bulk file copying, mass deletions, failed access attempts, and more.
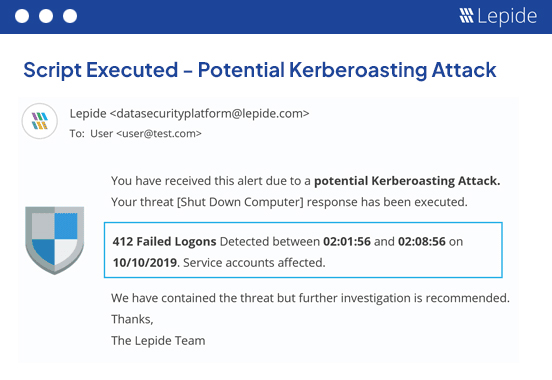
Execute custom scripts in response to anomalous or bulk file activity to shut down threats in real time.
Spot any changes to files in real time, including modifications, copies, deletes, creation events and more. Get real time alerts when threshold conditions are met.
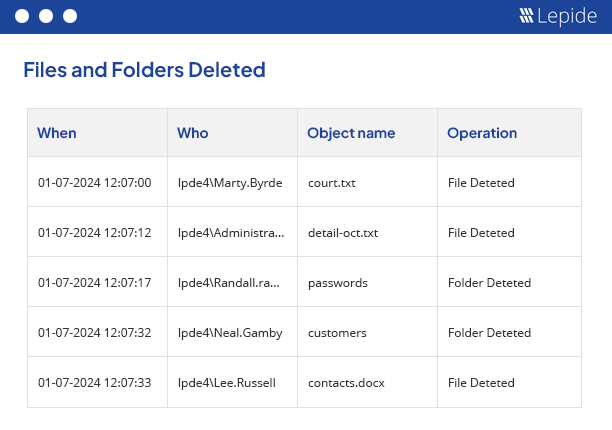
Whether you’re relying on event logs, or using a state of the art SIEM, you’re likely to find file monitoring to be a complex and noisy task. With Lepide, you’ll get a single record for each change with all the important information you need, including who, what, when and where.
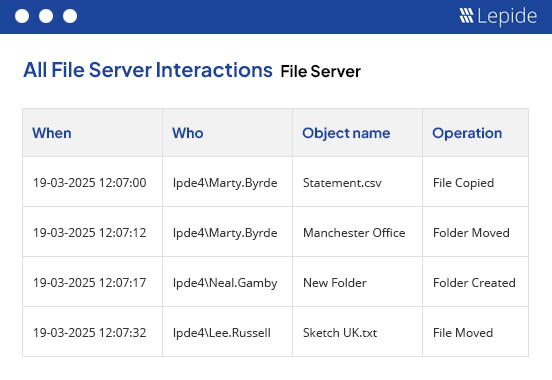
Prevent ransomware attacks from spreading in your file systems with machine-learning-powered detection of anomalous file activity, and automated threat response actions.
By following the guidelines outlined in this paper, your organization can establish a robust data access governance program that supports its business objectives and protects your valuable data assets.
Get the free guide now!