Track Changes Made to Files and Folders
The simple way to audit all changes made to configuration and data stored on Windows File System and NetApp Filers.














Electronic data is easier to manage than physical data, but in some ways, it is more vulnerable. Using Lepide File Server Auditor, you can not only deal with insider threats, but also address common regulatory compliance requirements. Our Solution gives organizations full visibility over the changes made to their Windows File Servers and NetApp Filers. IT Administrators can audit changes in File Server to get answers to common auditing questions (who, what, where and when). They can easily track and compare files and folders permissions on file servers.
File or Folder Created, File or Folder Renamed, File or Folder Modified, File or Folder Moved, File or Folder Deleted, File or Folder Copied
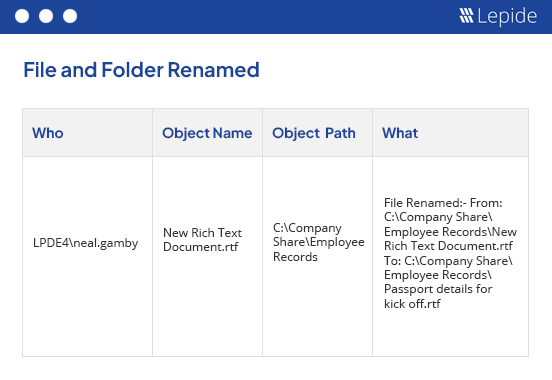
A single-line record of the change is shown in the reports. Just by looking at a record you will understand who made what change, where and when. We also give the details such as time, drive, folder name, file name, process and event details. Delegate the rights to selected users to view the selected reports in a Web-based secured console. You can also schedule it for auto delivery in CSV, PDF, or MHT format through your email or by saving at the shared location.
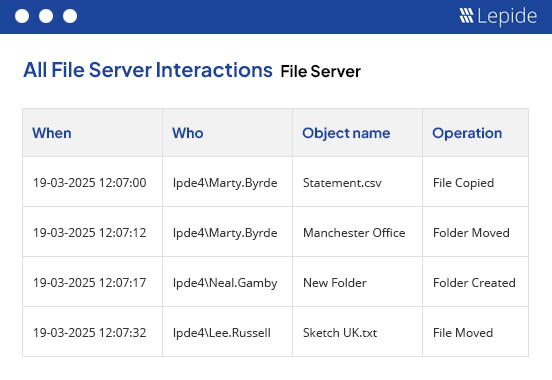
Lepide File Server Auditor delivers real-time alerts for more proactive and accurate reporting. These are delivered whenever any critical change in the files or folders is detected. You can improve the alerting mechanism with advanced filtration and threshold limits. These can be accompanied by your customized scripts that will automatically perform any action; including disabling a user account or removing the permissions of a user.
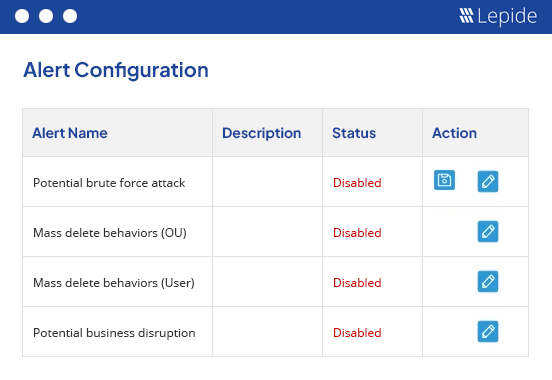
All changes to files and folders are recorded in a SQL Server database and displayed in predefined audit reports, which can be customized with filtration, search, sorting, grouping by and other options. These reports can be saved manually and scheduled to be delivered through email or via saving at any location at periodic intervals. You can create a customized version of any modification report to focus only on specific files, folders or operations. These reports can also be delegated to be accessed by users through a secured Web-based console.
By following the guidelines outlined in this paper, your organization can establish a robust data access governance program that supports its business objectives and protects your valuable data assets.
Get the free guide now!